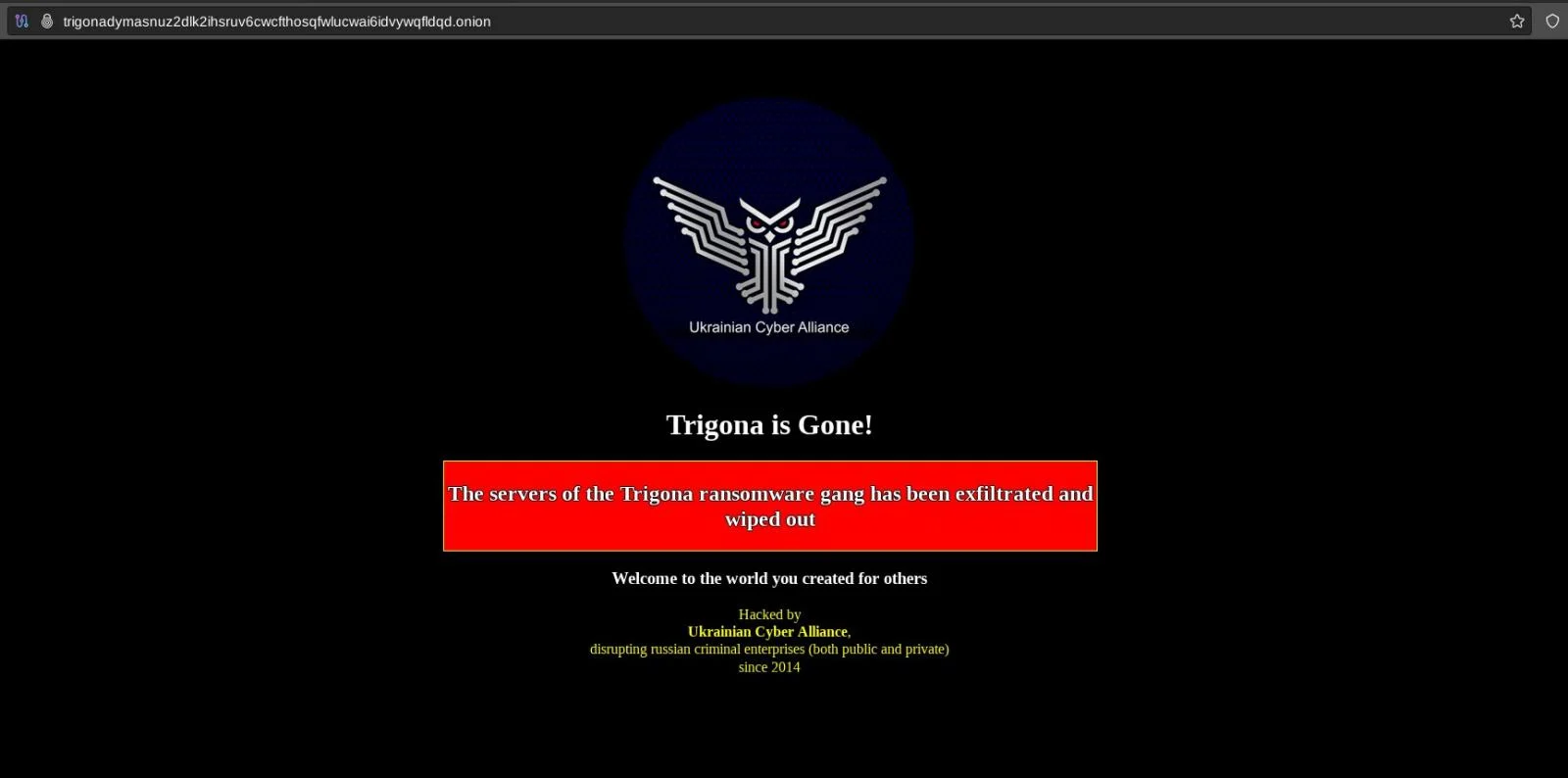
(19/10/23) Blog 292 – Trigona ransomware gang hacked by Ukrainian Cyber Alliance
A post uploaded yesterday by @vx_herm1t on X shows the current home page of Russian…
(18/10/23) Blog 291 – Encryption – a short guide (pt5)
In the last post, I discussed the properties of cryptographic keys, and the different types…
(17/10/23) Blog 290 – Encryption – a short guide (pt4)
So far in this short guide to encryption, we have looked at some of the…
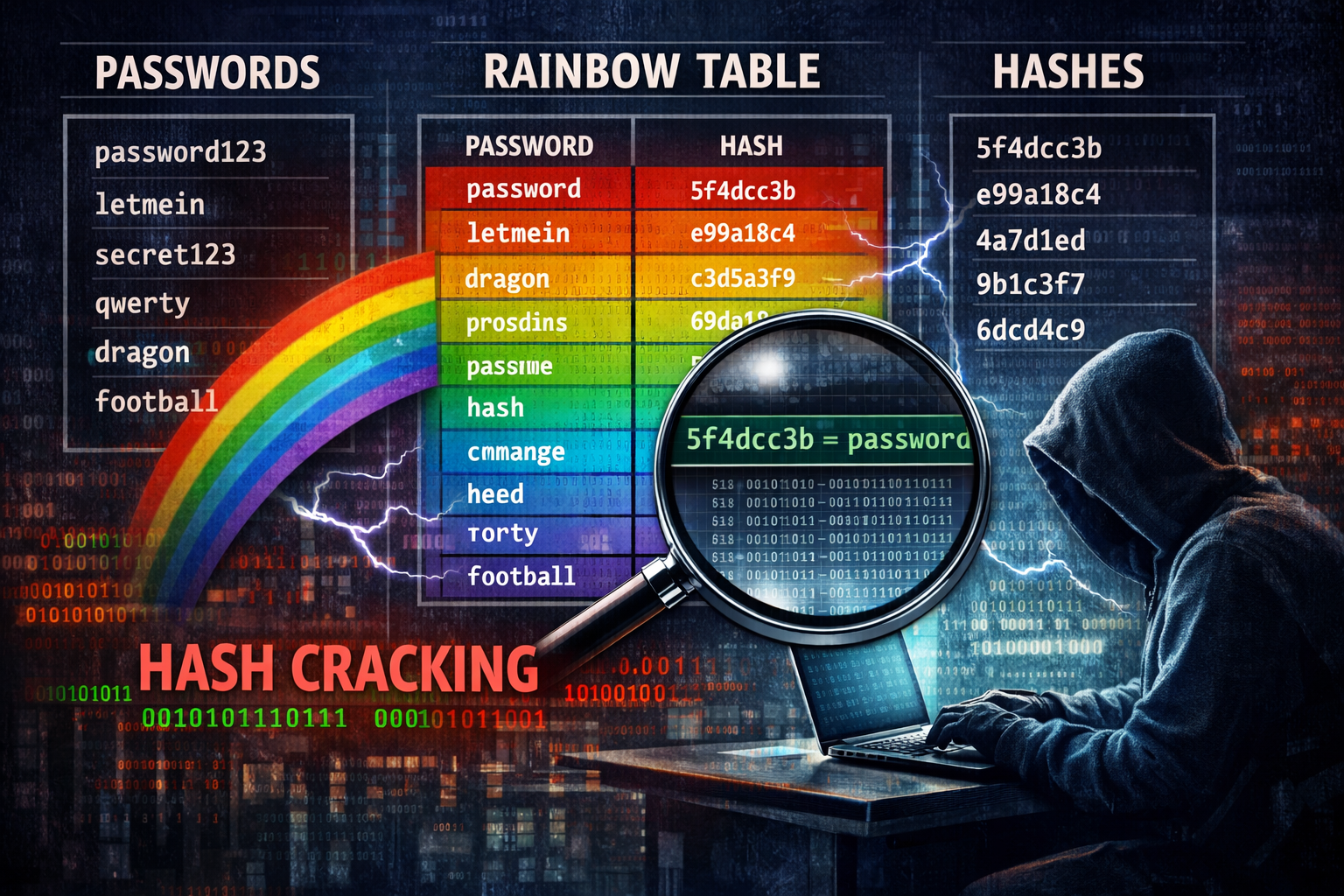
(16/10/23) Blog 289 – Encryption – a short guide (pt3)
One of the desirable properties of an encryption system is that of high variance, or…
(15/10/23) Blog 288 – Encryption – a short guide (pt2)
In the previous post, I identified a few common terms used in encryption, and then…
(14/10/23) Blog 287 – Encryption – a short guide (pt1)
We all know encryption is the no.1 tool used to keep data private - we…
(13/10/23) Blog 286 – Supply chain attacks – what are they? and why do they matter?
SolarWinds, MoveIT, NotPetya, CCleaner, Equifax, Target. All the above names have one thing in common…
(12/10/23) Blog 285 – Google Passkeys now the default option
On Tuesday (10th) Google announced that Passkeys were now the default sign-in option across all…
(11/10/23) Blog 284 – Microsoft Digital Defence report shows we are not learning from mistakes
Microsoft have just released the latest Digital Defence Report, and the findings are not great.…
(10/10/23) Blog 283 – Boots on the ground – coders in the cloud
It's a well known fact that cyber attacks are becoming more and more commonplace in…