(14-03-23) Blog 73 – MoaR Ransomware attacks
In this blog I’ll cover two breaking events which might be very significant in the coming weeks/months.
If you’ve been following my posts over the last few months, you will have noticed a common theme in many of them – The theme of ransomware.
Well that theme continues with two events which have been posted in the last few hours.
Attack one
First of all, we have the news that RING LLC, the Amazon owned company has been hit with a ransomware attack.

The attackers behind this breach call themselves ALPHAV , but are also known as BlackCat, AlphaVM, ALPHV-ng, and Noberus.
This group is fairly new to the ransomware scene, but since their arrival in 2021 have managed to compromise over 60 organisations and demand ransoms of up-to USD $3m.
Some of the organisations known to have fallen victim to the gang include:
- Florida International University
- University of Pisa
- Swissport
- Moncler Group
- Bandai Namco
- Creos Luxembourg
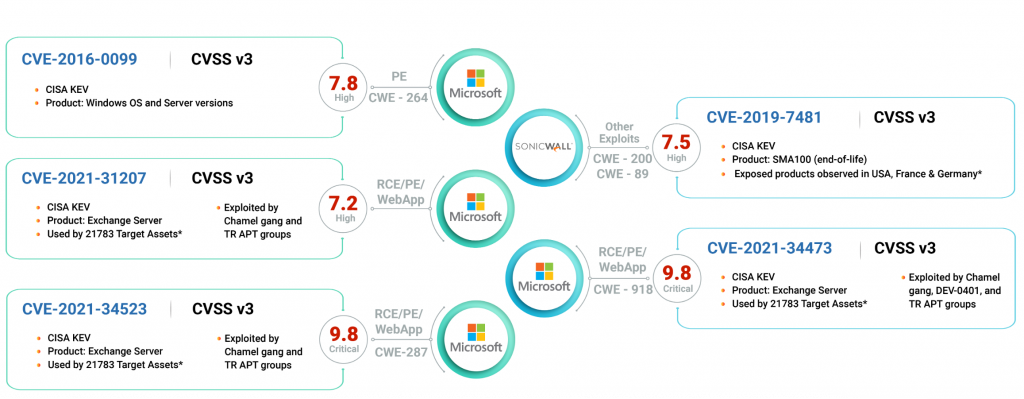
In an expose written by researchers at cybersecurityworks, they say that the group is actively leveraging exploits against five different Windows vulnerabilities.
- CVE-2016-0099 – Secondary Logon Elevation of Privilege Vulnerability
- CVE-2019-7481 – Vulnerability in SonicWall SMA100 allow unauthenticated user to gain read-only access to unauthorized resources
- CVE-2021-31207 – Microsoft Exchange Server Security Feature Bypass Vulnerability
- CVE-2021-34473 – Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2021-34523 – Microsoft Exchange Server Elevation of Privilege Vulnerability
Unusually for a ransomware group, ALPHAV seem to have considered the security and confidentiality of their attacks and victims.
The ransom notes used by the group are customized for each victim, often with links to unique data leak sites, ensuring complete privacy for any negotiations.
Additionally, the sites they use are controlled by an access key, ensuring that the negotiation sites cannot be accessed even in the event of a ransomware code leak.
RING attack

At the time of writing, it is unknown what data the attackers have access to, but if it is customer data, then it could be payment details, email addresses, WiFi passwords, and of course – camera footage.
It could also be internal data the attackers have access to which could be staff data, and even plans for upcoming devices. What ever it is, I’ll be keeping an eye out for news, mainly because I use Ring products, but also to keep this blog updated.
Attack two
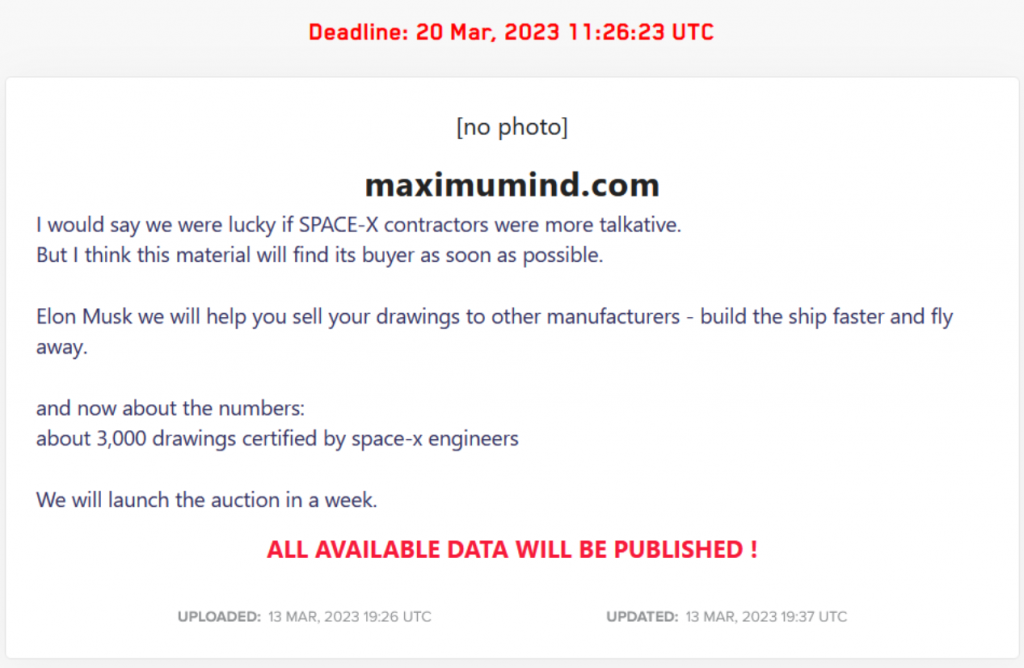
The second breaking news is that a 3rd party contractor to Elon Musk’s SpaceX company has been hit by the LockBit gang.

The company in question is called Maximum Industries Inc. and are a waterjet, laser cutting, and CNC machining company based in Irving Texas.
In a post on their website, the LockBit gang suggest that they have approx. 3,000 technical drawings certified by SpaceX engineers that they will auction to the Internet on the 20th March unless a ransom is paid.
Now, it’s well known that Mr. Musk is quite a strong-willed character, so it will be interesting to see how this one plays out.
Will his ego force him to stand his ground and tell LockBit where to shove their ransom? Or will the worlds richest man stump up a few dollars to protect his intellectual property? Or, will the US government intervene considering SpaceX’s contracts.
Again, this is another event I’ll be keeping my eye on for the next few weeks to see which way it goes.












