Net-NTLMv1 full rainbow tables released
Mandiant (the Google-owned Cyber Security research company) has released a comprehensive dataset of Net-NTLMv1 rainbow tables in an attempt to force organisations to migrate away from the outdated protocol.
The rainbow tables are publicly available from Google’s Cloud service, and full instructions of how to use them to crack an obtained NTMLv1 hash is available here
Net-NTLMv1 has been deprecated since the release of NTMLv2 back in 1989, yet many systems still implement it. Microsoft removed NTLMv1 in Windows 11 24H2 and Server 2025. But millions of older systems are still running with this old version of NTLM.
In 2012, it was demonstrated that every possible 8-character NTLM password hash permutation can be cracked in under 6 hours via the use of a 25-GPU cluster. This attack was refined in 2019 and reduced the time to crack all possible combinations to a little over 2.5 hours
It’s fair to say that this legacy protocol leaves organisations vulnerable to trivial credential theft, yet it remains prevalent due to inertia and a lack of demonstrated immediate risk.
So what’s the issue?
When a user logs in over a network, their Windows device is challenged to prove identity & authenticity. The domain server sends an encrypted response based on the user’s password as the challenge. The problem is that the encryption uses 56-bit DES – A cryptographic systems declared dead many years ago.
NTLMv1 uses a predictable challenge value with the pattern of 1122334455667788 every single time, which means attackers can precompute every possible response to that challenge and store it in a massive table (dictionary).
If you can capture the hash challenge, you can search this table and retrieve the password without any highly-complex brute-forcing of the password.
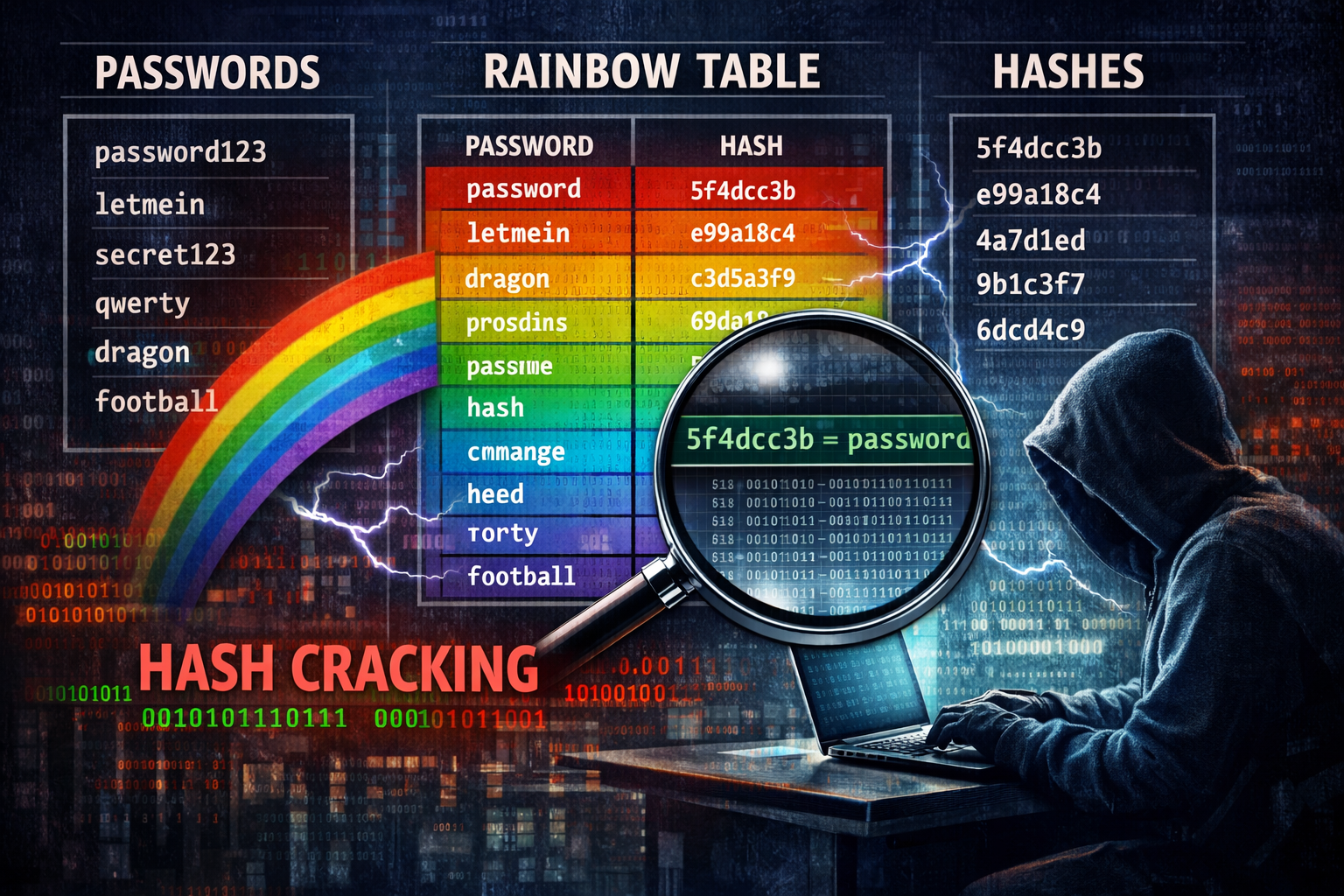
Naturally, with such a system, there are many, many possible password hashes, so this is where Rainbow tables come in handy. Rainbow tables are special types of precomputed dictionaries for caching the outputs of a cryptographic hash function. Rainbow tables massively reduce the number of values stored, which in turn massively reduces the computations required to identify a hash (and thus, its corresponding password)
Rainbow tables use hash-chains, and reduction functions to achieve this.
So, for example, take the word cat. If we run this through a hashing function we get a unique output (hash). If we now run this through a reduction function, we can generate a new word – e.g. dog
We repeat this step multiple times to produce a chain of words & hashes. However, what we store is the 1st password, and the final hash – everything in-between is simply ignored, but can be recomputed at a later date if needed.
This allows millions of passwords to be represented in the rainbow table as just a few hundred hash-chains
So once a hash is obtained , we assume the hash might be somewhere inside one of the chains
If we apply the reduction rule for that step, then compute a hash and repeat until we reach a possible chain end. If that end matches one stored in the rainbow table, we now know which chain contains the password.
All we need to do now is rebuild that one chain from the start, and then simply conduct a lookup of its possible hashes to find the one we have, and that gives us the password for that hash
These rainbow tables are what Mandiant have released – a comprehensive set of every possible password hash for NTLMv1
Why have they done this?
By releasing these rainbow tables, Mandiant aims to lower the barrier for security professionals to demonstrate the insecurity of Net-NTLMv1.
Tools to exploit this protocol have existed for many years, but they often require uploading sensitive data to third-party services or expensive hardware to brute-force keys.
The release of this dataset allows defenders and researchers to recover keys in under 12 hours using consumer hardware costing less than $600 USD
This now means that security professionals have a demonstrable mechanism to run test attacks against the systems they are responsible for to showcase to their organisations the possible issues they are facing in an attempt to get those systems replaced or upgraded as soon as possible