New python hacking tool targeting cloud & payment systems
Security researchers at SentinelOne have released information regarding a newly discovered malware which is being actively used to target cloud and payment services.
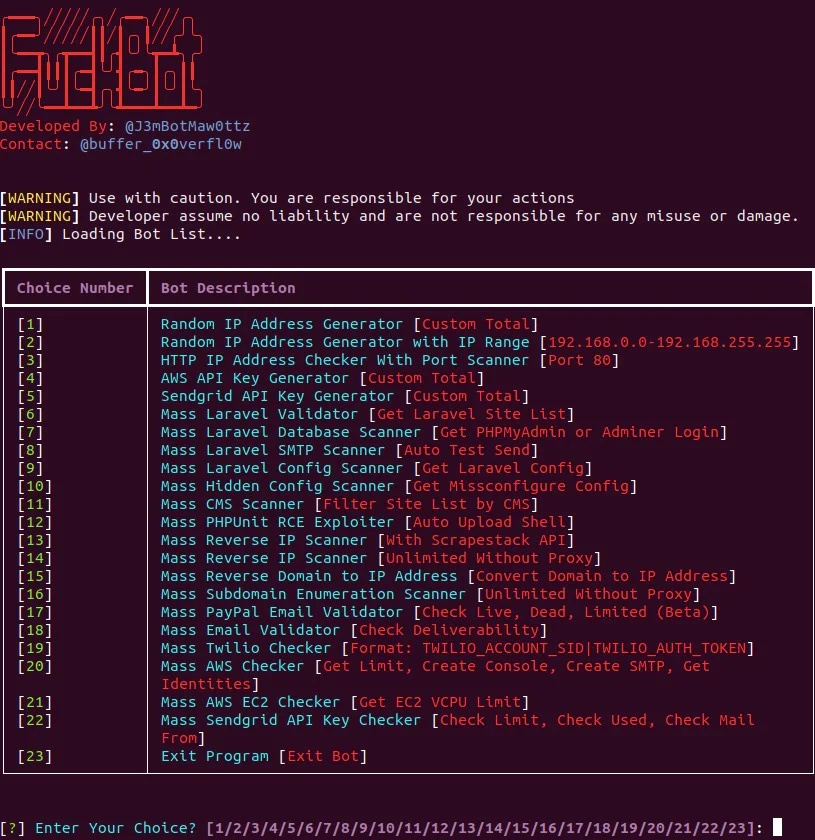
The Python-generated malware is called FuckBot and is capable of conducting a number of common hacking activities including credentials harvesting and AWS account hijacking along with various attacks against different SaaS accounts. The tool also has utilities designed to perform spamming attacks, including IP address generators and port scanners.
Screen-grabs of the malware show that it has the capability or delivering numerous attacks against a range of services, including three utilities that specifically target AWS services:
- AWS API Key Generator
- Generates a random AWS access key ID by appending 16 randomly selected alphabetic characters to the AWS
AKIAprefix. Then, it generates a secret key from 40 randomly selected alphabetic characters.
- Generates a random AWS access key ID by appending 16 randomly selected alphabetic characters to the AWS
- Mass AWS Checker
- Checks for AWS Simple Email Service (SES) email configuration details, including the maximum send quota and rate, as well as how many messages have been sent in the past 24 hours. It also creates a new user account with the username
iDevXploitand the passwordMCDonald2021D#1337and attaches the AdminsitratorAccess policy to elevate privileges for the new account
- Checks for AWS Simple Email Service (SES) email configuration details, including the maximum send quota and rate, as well as how many messages have been sent in the past 24 hours. It also creates a new user account with the username
- AWS EC2 Checker
- Reads a list of AWS identities from a text file in the format of
AccessKey|SecretKey|Region. The script then uses these values to check the targeted account’s EC2 service quotas.
- Reads a list of AWS identities from a text file in the format of
The data released by SentinalOne states that this new tool is novel in the fact that it doesn’t utilise the capabilities of the Androxgh0st code which is commonly used by other, similar hacking tools.
Androxgh0st
AndroxGh0st is a “SMTP cracker” which is primarily intended to scan for and parse the open source PHP framework – Laravel and extract secrets from exposed .env files.
env files are often targeted for their various configuration data including AWS, SendGrid and Twilio.
AndroxGh0st has multiple features to enable SMTP abuse including scanning, exploitation of exposed creds and APIs, and even deployment of webshells. For AWS specifically, the malware scans for and parses AWS keys but also has the ability to generate keys for brute force attacks.
Attacking payment systems
FuckBot has several features that target payment services:
The PayPal Validator feature validates PayPal account status by contacting a hardcoded URL with an email address read from an input list. The email is added to the request in the customer details section to validate whether an email address is associated with a PayPal account.
The script initiates the Paypal API request via the website hxxps://www.robertkalinkin.com which is a Lithuanian fashion designer’s retail sales website. All identified FuckBot samples use this website to authenticate the PayPal API requests.
The PayPal Validator crafts requests to this site with a fake item ID as well as fake customer details, then parses the response for a status message indicating success.
The Twilio feature takes a Twilio SID and Twilio Auth Token as input, and then checks the combination for details about the account, including balance and currency, along with a list of phone numbers connected to the account.
The Sendgrid (another Twilio app) feature is a Sendgrid API Key Generator, which generates a Sendgrid key to attempt account takeover.