Compromising Operational Technology (OT)
When most people think about a cyber attack, they think of things like a phishing attack that allows a threat actor to trick an employee into giving up data, or a Denial of Service attack that stops legitimate users accessing a service, or maybe a ransomware attack that encrypts a companies prized information.
There are many ways in which a cyber attack can happen, but when thinking about them, most people think about attacks against Information Technology (IT) systems. Not many think about attacks against Operational Technology (OT) systems.
OT can be defined as the use of hardware and software to monitor and control physical processes, devices, and infrastructure.
Think of any factory or plant and it will be using OT – a water treatment plant will use OT to run the treatment system – the pumps, the valves, the chemical dosing systems, the filtration systems, the aeration systems – all these things are becoming (if not already) automated with OT.
Sitting behind these systems are SCADA technologies – (SCADA – Supervisory Control And Data Acquisition) that allow humans to monitor and control the OT.
A report by Fortinet security identified that in 2023, 32% of those polled reported that they had experienced an increase in attacks against their OT systems as well as their IT systems.
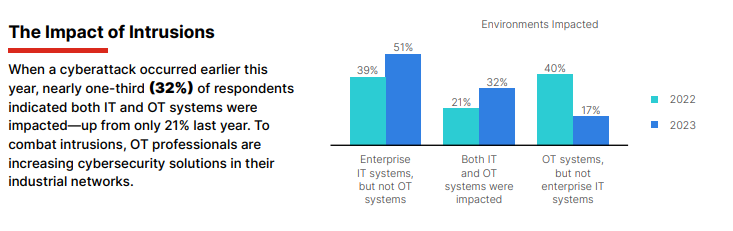
Protecting OT
The cyber security landscape for IT is well established, and whilst there are many successful attacks against IT infrastructure, many more attacks are unsuccessful due to the highly evolved ecosystem of security controls in place. In many cases, the successful attacks are successful because of human error – miss-configured settings, lax security hygiene, phished credentials, etc. The IT is good, the Human often isnt.
When it comes to the world of OT however, the landscape is quite different. OT security for many years has either been forgotten about, or only paid lip-service. The world of OT often has proprietary code which doesn’t lend well to being protected by COTS (Common Off The Shelf) security products. The world of OT often has communications protocols which have little or no security protecting data against eavesdropping or spoofing. The world of OT often consists of small devices with minimal capacity for information processing and as such cannot use encryption, or only encryption with weak algorithms.
As an example – one of the most widely used OT communications protocols is Modbus – Modbus was developed back in 1979 by a company called Modicon as a protocol to enable communications between automation devices and over the subsequent years has become the de-facto protocol to use in the OT space.
One of the reasons for the uptake in Modbus is the fact that it is an opensource and royalty-free protocol system which allows systems engineers all around the world to implement it in their technologies.
Since its introduction, Modbus has undergone a number of updates, but none of the core updates have ever included encryption or authentication. Encryption can be implemented to Modbus if the transport protocol used is TCP, but other than that – Modbus is essentially open to anyone for attack.
An interesting example of a highly vulnerable OT system is one which came to my attention via the user @LaurieWired on X.com the other day.
The post showed a Bosch pneumatic torque wrench which has been compromised by a malware called drillcrypt making the device completely unusable.
The wrench, a Bosch Rexroth NXA015S-36V-B (commonly known as a Nutrunner) was a test device being examined by security researchers at Nozomi Networks

These devices are used in thousands of vehicle manufacturing plants all over the world – the system became an automotive manufacturing standard in 1999.
The nutrunner is equipped with a visual display presenting real-time data and activity results to the operator, and has the capability to connect to a wireless network through its embedded Wi-Fi module allowing for data to be transmitted using various supported protocols to a designated historian server.
The device can be remotely reprogrammed using the management services provided by its NEXO-OS operating system.
The Linux-based NEXO-OS presents a range of application choices, encompassing tightening system configuration, the generation of tightening programs by specifying processes, and the analysis and diagnosis of tightening cases, through the exposed management web application.
The operating system also supports a wide range of communication protocols such as Rexroth OpenProtocol, VW-XML, and BMW-TPC, so that the nutrunner can be seamlessly integrated with SCADA systems, PLCs, or other production devices.
Critical vulnerabilities
The majority of the 25 vulnerabilities identified by Nozomi Networks Labs affected the management web application, although a few were found in the services parsing the mentioned protocols.
The vulnerabilities found on the Bosch Rexroth NXA015S-36V-B allow an unauthenticated attacker the ability to send network packets to the target device to obtain Remote Execution of arbitrary Code (RCE) with root privileges, completely compromising it.
Once unauthorised access is gained, numerous attack scenarios become possible including ransomware attacks and the manipulation of control and view data.
A ransomware attack would render the system completely disabled resulting in a total halt to production, whereas the manipulation of data could see critical fastenings tightened to an incorrect torque resulting is failure of components after manufacture – E.G. engine mounts, wheel bearings, steering components etc.
The vulnerabilities discovered have been given a Common Vulnerability Score System (CVSS) rating ranging from 5.3 to 8.8. The vulnerabilities are tracked as the following CVEs:
- CVSS 8.8
- CVE-2023-48252
- CVE-2023-48253
- CVSS 8.1
- CVE-2023-48243
- CVE-2023-48250
- CVE-2023-48251
- CVE-2023-48262
- CVE-2023-48263
- CVE-2023-48264
- CVE-2023-48265
- CVE-2023-48266
- CVSS 7.8
- CVE-2023-48257
- CVSS 6.5
- CVE-2023-48242
- CVE-2023-48245
- CVE-2023-48246
- CVE-2023-48249
- CVSS 6.3
- CVE-2023-48255
- CVSS 5.5
- CVE-2023-48248
- CVE-2023-48258
- CVSS 5.3
- CVE-2023-48244
- CVE-2023-48247
- CVE-2023-48254
- CVE-2023-48256
- CVE-2023-48259
- CVE-2023-48260
- CVE-2023-48261
Bosch Rexroth is set to deliver official patches for all vulnerabilities by the end of January