(25/12/23) Blog 359 – Wall of Flippers – detects and blocks Bluetooth spam attacks
The Flipper zero is a very well known device in the world of Hacking / Pentesting and mischief. Initially developed as a Kickstarter project back in 2019 – 2020 the device received nearly 23,000 backers and raised a staggering sum of $4, 882,000. Since then the device has gone on to be a world-wide success with hundreds of thousands of the devices being sold all round the world.
Capable of intercepting, copying, and mimicking multiple wireless protocols including Bluetooth, Wi-Fi, NFC, infrared, and many other sub-GHz frequencies.
Due to it’s supported frequency range, the Flipper zero is very adept at capturing and replaying the signals for all sorts of commercial devices such as TV remotes, automatic gates, barriers, and shutters, the cloning of security passes, credit-card / debit-card chips, animal microchips, Transportation cards, keyfobs, wristbands, location tags, and much more.
These capabilities have made the flipper the tool of choice for wireless security testing, but also for pranksters.

Unfortunately, those pranks can have a real-world dangerous effect. At a recent Furry Festival, someone started spamming Bluetooth devices which caused multiple vendors to lose connectivity to their payment devices meaning no sales transactions could be completed, but they also happened to affect someones Bluetooth controlled insulin pump causing it to crash.
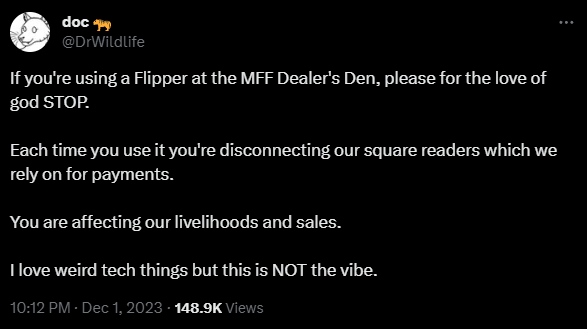
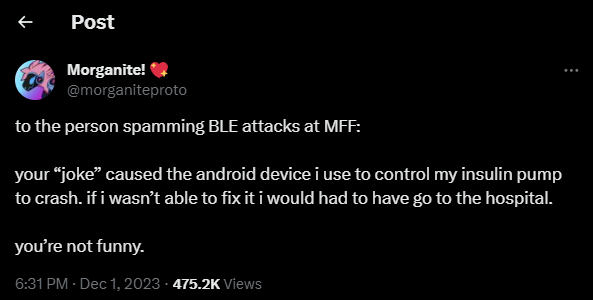
This isn’t the only time a flipper has been used to this effect, the situation is becoming quite a common thing in crowded areas. A recent attack / prank occurred on the New York subway, where someone used a Flipper to run a BTLE spam attack which caused multiple iPhones to continuously try to connect to non-existing Bluetooth devices – thus effectively causing a Denial of Service to the users.
Wall of Flippers
Well, these attacks may be about to become a thing of the past.
A python project dubbed “wall of flippers” allows users to detect and block BTLE spam attacks.
The project was created by a developer called K3YOMI, and is available via their github page for users to install and run on their devices.
Designed to be permanently running on either a Windows or Linux device, the program scans for BTLE packets in the vicinity and analyses the transmitted packets against a set of predefined patterns considered to be indicative of malicious activity.
The program identifies the Flipper via its MAC address and signal strength of the BLTE attack and starts to block any requests it sees. The program then remembers these characteristics in case it happens again.
A video of Wall of Flippers in action has been uploaded to X.com by @androidmalware2