(26/10/23) Blog 299 – Pwn2Own Toronto hands out $800K in prizes in 1st two days
The annual Pwn2Own Toronto event started this week with contestants from all over the world flexing their skills against some of the latest tech to win large sums of cash (and Kudos).

The 4-day event, which is put together by the Trend Micro Zero Day Initiative allows hackers, pentesters, and security experts from across the world descend on Toronto to showcase the latest zero-day exploits against some of the newest technologies in the market today. The prize pot for successful teams is $1,000,000
A wide range of technologies are open for exploitation, including:
- A Canon imageCLASS MF753Cdw printer
- A Lexmark CX331adwe printer
- A HP Color LaserJet Pro MFP 4301fdw printer
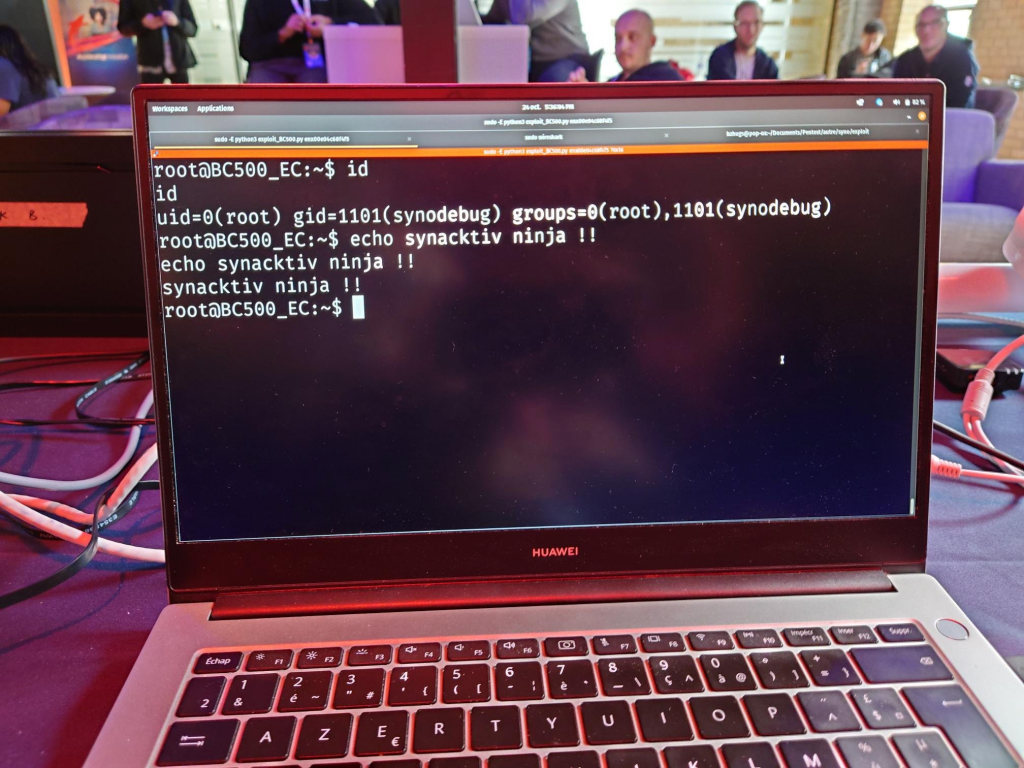
- Synology BC500 surveillance cameras
- Wyze Cam surveillance cameras
- QNAP TS-464 Network Attached Storage (NAS)
- Sonos Era 100 Smart Speaker
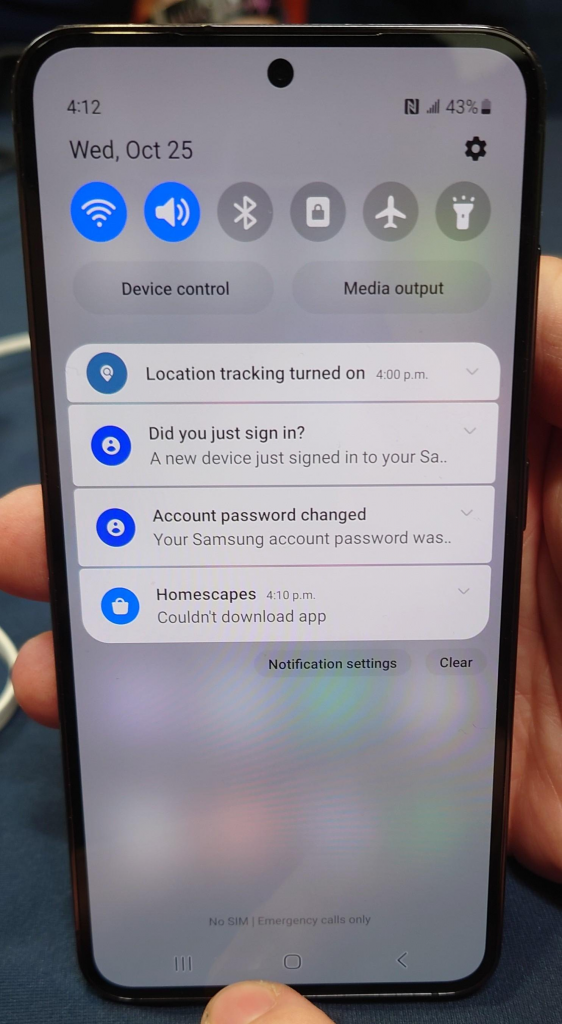
- Samsung Galaxy S23 mobile phone
- Xiaomi 13 Pro mobile phone
There is also a category for network exploitation by accessing a TP-Link router, and then pivoting to other devices such as a Canon printer, Lexmark printer, or Synology BC500 surveillance camera.
Day 1 successes
A number of teams successfully managed to exploit their chosen technologies, earning a collective $438,750 in cash prizes.
The successes were as follows:
- Binary Factory was able to execute a stack-based buffer overlow attack against the Synology BC500. They earned $30,000
- Pentest Limited was able to execute a 2-bug chain against the My Cloud Pro Series PR4100 using a DoS and SSRF. They earned $40,000
- Team Viettel was able to execute a single-bug attack against the Xiaomi 13 Pro. They earned $40,000
- Nguyen Quoc Viet was able to execute a buffer overflow attack against the Canon imageCLASS MF753Cdw. He earned $20,000
- Synacktiv was able to execute a 3-bug chain against the Synology BC500. They earned $15,000
- Team Orca of Sea Security was able to execute a 2-bug chain using an OOB Read and UAF against the Sonos Era 100. They earned $60,000
- Team ECQ was able to execute a 3-bug chain using an SSRF and two injection vulnerabilities against the QNAP TS-464. They earned $40,000
- Compass Security was able to execute a stack overflow attack against the Synology BC500. However, the exploit they used was previously known. They still earned $3,750
- “Ben” was able to execute a stack-based buffer overflow against the Canon imageCLASS MF753Cdw. He earned $10,000
- Pentest Limited was able to execute an Improper Input Validation against the Samsung Galaxy S23. They earned $50,000
- Team Viettel was able to execute a 2-bug chain against the QNAP TS-464. They earned $20,000
- Team PHPHooligans were able to execute a memory corruption bug leading to RCE against the Lexmark CX331adwe. They earned $20,000
- STAR Labs SG was able to execute a 2-bug chain including directory traversal and command injection against the QNAP TS-464. They earned $20,000
- NCC Group was able to execute an attack against the Xiaomi 13 Pro. They earned $20,000
- Team Viettel was able to execute a stack-based buffer overflow attack against the Canon imageCLASS MF753Cdw. They earned $10,000
- STAR Labs SG was able to exploit a permissive list of allowed inputs against the Samsung Galaxy S23. They earned $25,000
- Thales was able to execute an attack against the QNAP TS-464. However, the exploit they used was previously known. They still earned $12,500
- R-sec was able to execute a stack buffer overflow attack against the Canon imageCLASS MF753Cdw. However, the exploit they used was previously known. They still earned $2,500
Day 2 successes
A number of teams successfully managed to exploit their chosen technologies, earning a collective $362,500 in cash prizes.
The successes were as follows:
- Team Viettel was able to execute an OOB write against the Sonos Era 100. They earned $30,000
- Chris Anastasio was able to exploit a bug in the TP-Link Omada Gigabit Router and another in the Lexmark CX331adwe. He earned $100,000
- Bugscale was able to execute a stack-based buffer overflow attack against the Synology BC500. However, the exploit they used was previously known. They still earned $3,750
- A DEVCORE Intern was able to execute a stack overflow attack against the TP-Link Omada Gigabit Router and exploit two bugs in the QNAP TS-464. They earned $50,000
- Team Viettel was able to execute a stack-based buffer overflow attack against the HP Color LaserJet Pro MFP 4301fdw. They earned $20,000
- Interrupt Labs was able to execute a stack-based buffer overflow attack against the Canon imageCLASS MF753Cdw. However, the exploit they used was previously known. They still earned $2,500
- SAFA ex Teamt5 was able to execute a stack-based buffer overflow attack against the Synology BC500. However, the exploit they used was previously known. They still earned $3,750
- Team Orca of Sea Security was able to execute an attack with one bug against the Synology RT6600ax and a three-bug chain against the QNAP TS-464 for the SOHO Smashup. They earned $50,000
- The VNG Security Response Center was able to execute a 2-bug chain against the QNAP TS-464. However, the exploit they used was previously known. They still earned $5,000
- Sina Kheirkhah was able to execute an RCE attack against the Synology BC500. However, the exploit he used was previously known. He still earned $3,750
- Sonar was able to execute a command injection against the Wyze Cam v3. They earned $30,000
- SEFCOM T0 was able to execute a command injection against the Wyze Cam v3. However, the exploit they used was previously known. They still earned $3,750
- Interrupt Labs was able to execute an improper input validation attack against the Samsung Galaxy S23. They earned $25,000
- ToChim was able to exploit a permissive list of allowed inputs against the Samsung Galaxy S23. They earned $25,000
- ANHTUD was able to execute a stack-based buffer overflow attack against the Canon imageCLASS MF753Cdw. They earned $10,000
What happens with the exploits?
The competition is carefully regulated by the ZDI team with a strict code of conduct and rules:
The prize amount offered to a researcher for a particular vulnerability depends on the following criteria:
- Is the affected product widely deployed?
- Can exploiting the flaw lead to a server or client compromise? At what privilege level?
- Is the flaw exposed in default configurations/installations?
- Are the affected products high value (e.g. databases, e-commerce servers, DNS, routers, firewalls)?
- Does the vulnerability require a social engineering component? (e.g. clicking a link, visiting a site, connecting to a server, etc.)
The process of handling the vulnerabilities and exploits is, as you would expect, carefully managed and all discovered vulnerabilities are disclosed to the relevant manufacturers for remediation before any data is released to the public.
All identified vulnerabilities are entered into the CVE database for tracking, and security advisories are published. The Pwn2Own website produces a list of the CVEs and advisories: