(08/09/23) Blog 251 – Electoral Commission failed cyber essentials
You may remember the news last month that the UK’s electoral register was compromised and the PII (Personally Identifiable Information) of millions of registered voters was compromised.

If not – here’s a brief recap:
On the 8th August, the Electoral commission published a notification that:
“they have a duty under Articles 33 and 34 of the UK General Data Protection Regulation to notify data subjects if their data has been breached by inappropriate access, loss, or theft from our systems.”
That notification went on to explain that in October 2022 an incident was identified which, after investigation transpired that unknown actors had gained access to the commissions IT systems in August 2021 and had gained access to servers which held the Commissions emails, control systems, a copies of the electoral register.
The electoral register data which was accessed was that pertaining to anyone in Great Britain and overseas registered to vote between 2014 and 2022, and anyone in Northern Ireland in 2018.
Failed Cyber Essentials
A whistle-blower from within the Electoral Commission has revealed that the organisation had failed the NCSC Cyber Essentials security check list audit around the time of the breach in 2021.
Since the news of the security failure was made public, a spokeswoman for the Commission has admitted the audit failure but claims that the breach was not related to the failings.
One of the reasons the organisation failed the audit was that about 200 staff laptops were running obsolete and potentially insecure software.
The Commission was urged to update the Windows 10 Enterprise operating system, which had fallen out of date for security updates months earlier.
Auditors also issued the failure because staff were using old iPhones no longer supported by Apple to receive security updates.
Regardless of whether the breach was directly related to the security failures or not, what it does show is that at the time of the breach, there was an obvious systematic failure of good security practice leading to a very weakened security posture.
What is Cyber Essentials?
Cyber Essentials is a NCSC-backed scheme which identifies key areas of security that will help security teams and business decision makers to protect an organisation, whatever its size, against a whole range of the most common cyber attacks.
The government requires all suppliers bidding for contracts involving the handling of certain sensitive and personal information to hold an up-to-date Cyber Essentials certificate.
There are two levels of certification for Cyber Essentials:
Cyber Essentials
This is a self-assessment option which gives organisations protection against a wide variety of the most common cyber attacks.
Certification at this level gives an organisation peace of mind that their defences will protect against the vast majority of common cyber attacks simply because attackers are looking for targets which do not have the Cyber Essentials technical controls in place.
Cyber Essentials shows you how to address those basics and prevent the most common attacks.
Cyber Essentials Plus
Cyber Essentials Plus contains all the same advice and guidance as Cyber Essentials, but rather than a self-certification audit, Cyber Essentials Plus includes a hands-on technical verification – akin to a pen test.
Getting certified
To help organisations on their journey to certification, a Cyber Essentials readiness toolkit is available from the NCSC which is a simple set of questions designed to get organisations thinking about their current security posture.
Based on responses given, the toolkit will offer advice to help organisations prepare for the Cyber Essentials process
When an organisation feels it is the time to get certified, the NCSC’s partner for Cyber Essentials – The IASME Consortium will assist with the process.

The process begins with downloading the Cyber Essentials self-assessment questionnaire – regardless of whether you are aiming for the Cyber Essentials, or Cyber Essentials Plus certification, it is advised that all organisations looking at certification completes the questionnaire as it focuses the organisations thought processes.
The questionnaire is a 30-page document with eight distinct categories of security-related questions and three categories relating to the company and the scope of the tests. The categories are:
- Your company – questions about the size of company, number of employees, type of industry, etc.
- Scope of assessment – questions relating to elements of the organisation which they feel need to be assessed as part of the process
- Insurance – questions relating to whether or not a successful company which has a turnover of less than £20M would like to take a free cyber insurance offer
- Firewalls – questions relating to firewalls – how many the organisation has, their configuration state, their deployment within the network, etc.
- Secure configuration – questions relating to secure configuration of both network, and end point devices in both on-premise and cloud environments. i.e. disabling of unused accounts, removal of all unused applications & services, password policies, etc.
- Device locking – questions relating to locking mechanisms on devices – e.g. biometric, passwords, PINs, etc.
- Security update management – questions relating to updates and patches for all devices in scope i.e. the removal of unsupported devices and software for the estate, the use of anti-malware technologies, update roll-out timelines, etc.
- User Access Control – questions relating to user access to accounts, data, devices, and services. i.e. restricted user access, restricted administrator access, account management processes (create, manage, delete, etc.)
- Administrative Accounts – questions relating to those accounts with special privileges i.e. Admin account creation processes, admin account separation processes, etc.
- Password-Based Authentication – questions relating to how users authenticate to systems and how the company protects password data. E.g. password policies, password audits, password hash storage / transfer, processes for if/when a password is compromised, the use of MFA, etc.
- Malware protection – questions relating to the installation and use of anti-malware technologies on all devices in scope.
Once an organisation has completed the questionnaire, if they are wishing to achieve the Cyber Essentials certification, they must use the online application portal to submit their answers to IASME along with the fee, which varies depending on the size of the organisation and await a result.
Organisations have 6 months to complete the process once they apply, which is why it is advised to download the questionnaire first to see what is required of the audit before beginning the formal process.
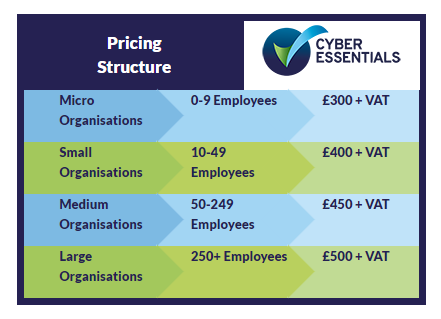
For those wishing to achieve the Cyber Essentials Plus, then a quote will need to be generated based on the size of the organisation and the scope of the systems required to be tested – an online application form is provided for organisations to request a quote.