(18/04/23) Blog 108 – LockBit gang targeting MacOS
I’ve written a number of posts about the LockBit gang so far this year, but this post is something new for them and other ransomware gangs.
Details are emerging online that the LockBit gang have started developing ransomware which aims to targets Mac users with what appears to be the first encryptor for the Apple devices.
In a tweet by @malwarehunterteam, they reveal that they have found a file uploaded to the anti-virus testing site Virus Total which targets Mac OS.
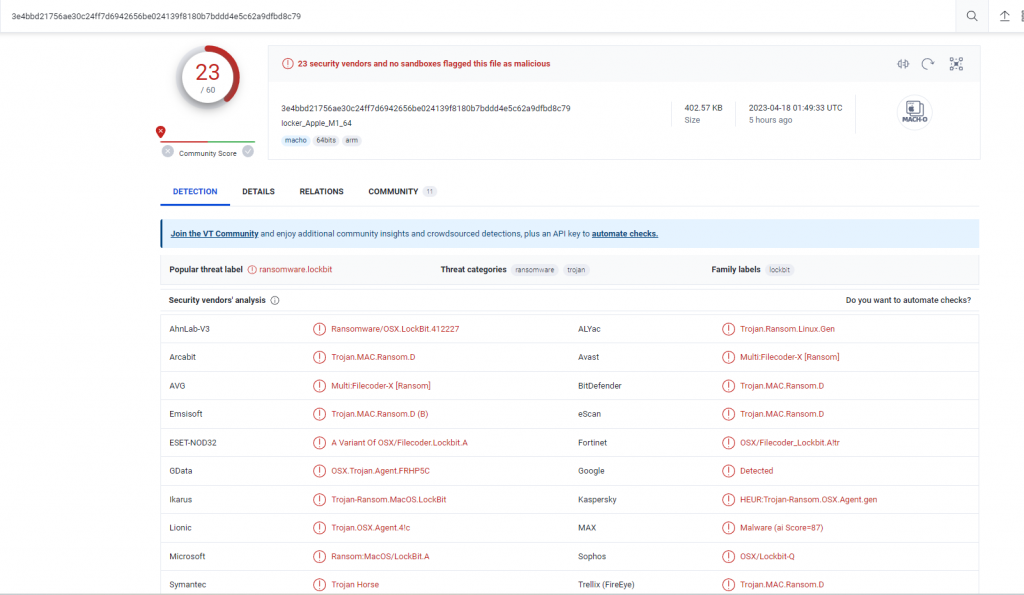
Details of the file from Virus Total show that the malware looks to be designed for the latest Mac operating system and carries the title “Locker_Apple_M1_64“
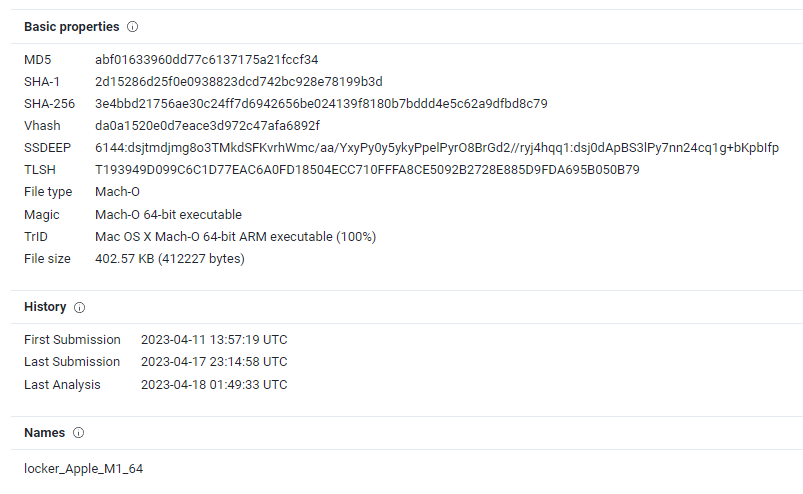
Analysis of the file by the researchers at Bleeping Computer identified a number of references to VMware ESXi, and various Microsoft Windows files, leading to the suggestion that this new malware shares the same codebase as older LockBit encrypters rather than being a fresh build of code.


Work in progress
Mac OS security researcher Patrick Wardle has taken a deep dive into the code and reported his findings via his website.
Patrick has also uploaded a copy of the binary file for others to download and analyse.
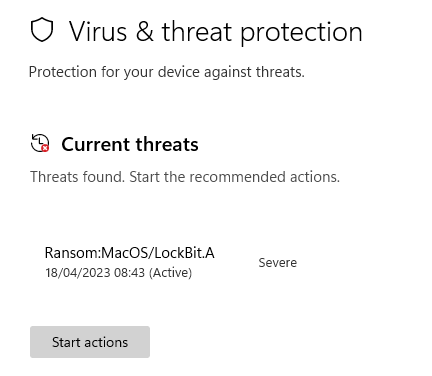
Microsoft Windows Defender detects the file as malicious:
In his research, Wardle reports that the ransomware is currently in very early stages of development. One of the first things he mentions is that currently, the malware file will not be able to run on a Mac as it does not have a valid digital signature – as such, Apple devices will report the fact that the file is corrupt and will not allow its execution.
After decoding the binary, Wardle managed to locate the ransome note which would be deployed on an infected device:
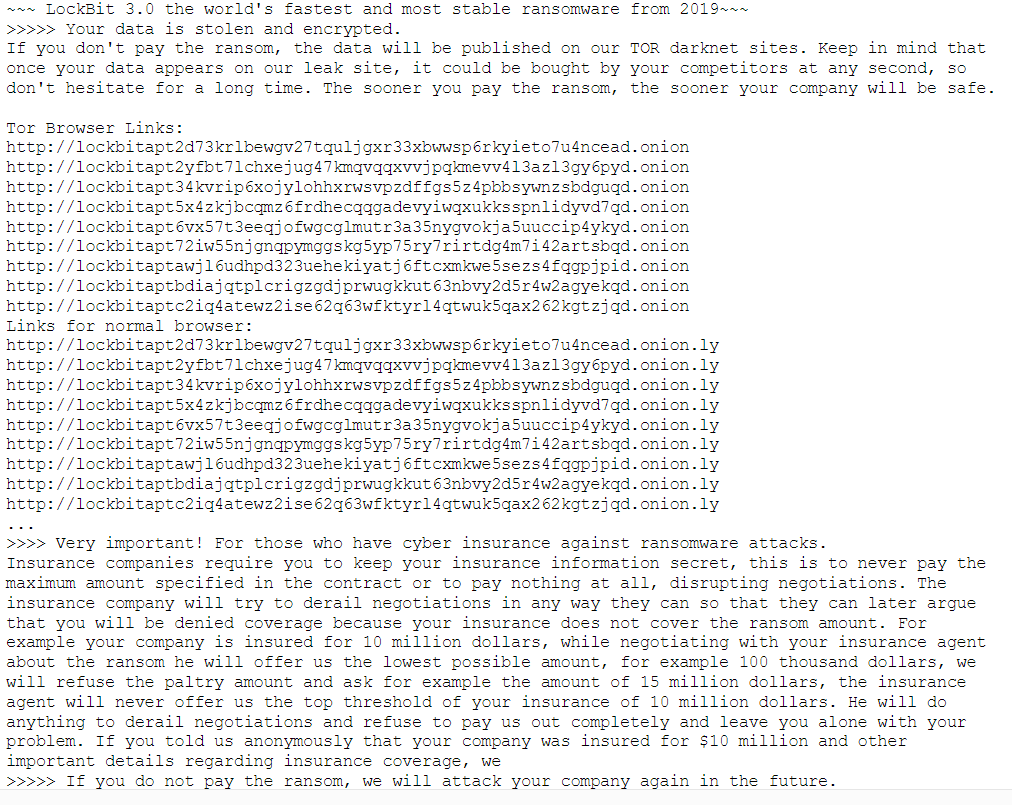
Nothing to worry about (yet!)
In his write-up, Wardle posts a final note about the file and says that whilst the file is most definitely ransomware destined for the MacOS platform, it is unlikely to be able to run as it has no ability to bypass the Apple TCC protection (Transparency, Consent and Control).
TCC was implemented by Apple back in 2012 as a security measure that blocks any service from being able to run on the OS without explicit consent from the user running the device.
Today we dove into a macOS ransomware sample created by the infamous LockBit ransomware gang. And while this may be the first time a large ransomware group created ransomware capable of running on macOS, it worth nothing that this sample is far from ready for prime time. From it’s lack of a valid code-signing signature to its ignorance of TCC and other macOS file-system protections as it stands it poses no threat to macOS users.
Moreover, the variant is rather buggy …containing flaws such as buffer overflows that will cause it to prematurely exit, when run on macOS
Patrick Wardle – objective-see.org
LockBit references on cybertrainer.uk
My previous posts about LockBit are below:












