(15-01-23) Blog 15 – LockBit ransomware
You may have seen over the last few days that the Royal Mail has been informing people that they should not attempt to post anything which needs to go overseas?
The reason for the message is due to the fact that the systems which Royal Mail use for that purpose have been hit with a cyber attack known as LockBit
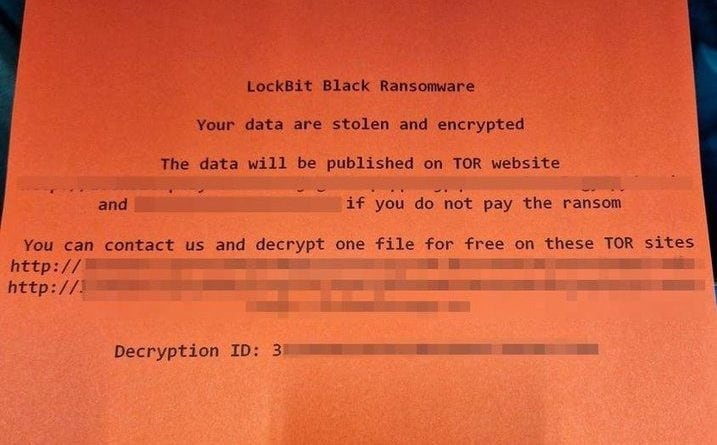
The image above is of the ransomware note which began to appear on a number of printers at a Royal Mail depot in Mallusk, north of Belfast, Northern Ireland. The “old school” mechanism of delivering the ransomware note is a common trait of the LockBit gang.
Unconfirmed reports suggest that it is the label printing system for overseas post which has been attacked at the Royal Mail, but the ability of the malware to run riot throughout a network could mean that other systems are also infected.
At this point, the Royal mail have not commented on whether any other systems have been impacted. The NCSC and the NCA are currently helping the Royal Mail recover their platforms and gather evidence for prosecution – assuming they can prosecute a hidden, Russian gang of cyber criminals.
This attack is not the 1st for the LockBit gang, but this attack is one which is taking a bit to unpick. The attack on the Royal Mail is one being called “LockBit black” which is a fairly new variant of the LockBit malware.
The Lockbit gang has previously made ransom demands of tens of millions of pounds and is thought to have extorted around $100m (£82m) in total from its victims over the past few years.
In November 2022, the Lockbit gang targeted the car dealership Pendragon – owners of CarStore, Evans Halshaw, and Stratstone, attacking computers across its 200 UK sites and demanded a £60m ransom to unlock them.
The hackers also targeted Advanced, a firm which supplies software to 85 per cent of NHS 111 services. The firm’s Adastra system allows call handlers to dispatch ambulances, book out of hours urgent appointments, and fulfil emergency prescriptions.
More than 1,000 care homes, which use the firm’s Caresys software, were also been affected – along with mental health services across the NHS, which use its record management system.
Lockbit origins
Attacks attributed to the LockBit malware started surfacing around September 2019, and were originally called the abcd ransomware due to the fact that the files encrypted had those characters as their file extensions.
In 2020, security company McAfee produced a report in association with Northwave security that examined this new strain of ransomware, and suggested that it was a heavily targeted malware which had a capability to self-spread throughout an infected network.
The ability to self-spread was novel in ransomware, typically ransomware has always involved a human element to allow the ransomware to spread, but in the case of the McAfee report, they investigated one such attack where the malware had used inbuilt Windows technologies to move throughout the network in a fully automated manner.
“With the administrator-level account, the attacker used SMB to perform network reconnaissance, resulting in an overview of accessible hosts. Subsequently, the attacker used the internal Microsoft Remote Access Server (RAS) to access these systems using either the administrator or the LocalSystem account. The LocalSystem account is a built-in Windows account. It is the most authoritative account on a Windows local instance (more potent than any admin account). Using these accounts, the attacker owned these systems and could do anything they wanted, including turning off any end-point security products. Interestingly, both the lateral movement and the deployment of the ransomware was entirely automated.”
McAfee report into Lockbit
Lockbit propogation
After getting in to a network, LockBit uses a dual method to map out and infect the victimised network.
ARP (Address Resolution Protocol) tables, which map local IP addresses to device MAC addresses, help to locate accessible systems, and SMB (Server Message Block), a protocol used for sharing files and folders among networked machines, allows the infected nodes to connect to uninfected ones. LockBit then executes a PowerShell script that spread the ransomware to those machines.
Using SMB, ARP tables, and PowerShell is an increasingly common way of spreading malware throughout a network because almost all networks rely on these systems. It is hard for antivirus products and other network defenses to detect the malicious use of these systems and utilities.
LockBit has another means of staying stealthy as well. The PowerShell script which LockBit downloads to infected machines is disguised as a PNG image file which in actual fact is a program executable that performs the encryption of the machine.
LockBit has another clever trick up its sleeve too. Before the ransomware encrypts data, it connects to an attacker-controlled server and then uses the infected machine’s IP address to determine where it is located.
If it resides in Russia or another country belonging to the Commonwealth of Independent States, it aborts the process. The reason is most likely to prevent being prosecuted by law enforcement authorities there.
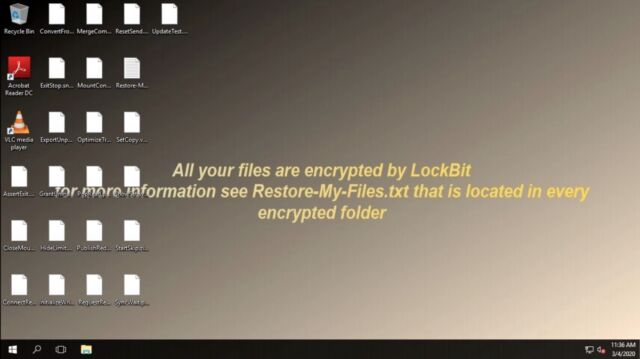
Once LockBit has encrypted the victims device, it displays it’s ransomware note:
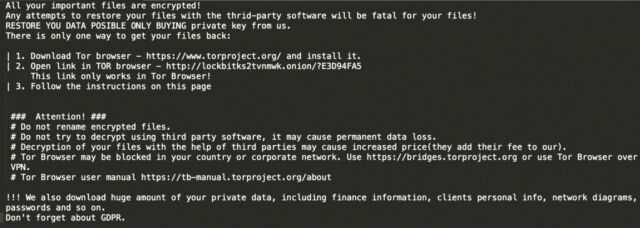
Instructions on how to pay the ransom are included in a txt file on the machine:
Lockbit v2
LockBit version 2 started being seen around the latter end of 2020 and had a few changes to the way it operated.
The encrypted files now had the file extension of .lockbit instead of the older .abcd, the debug function seen in older variants was removed, and some attackes had code which was digitally signed.
LockBit v3 – Blackbit
The latest version of LockBit – the one which has caused the upset at the Royal Mail is considerably different to it’s predecessors, although some researchers have found similarities to another malware strain called BlackMatter. This could be the reason behind the new name – LockBit Black.
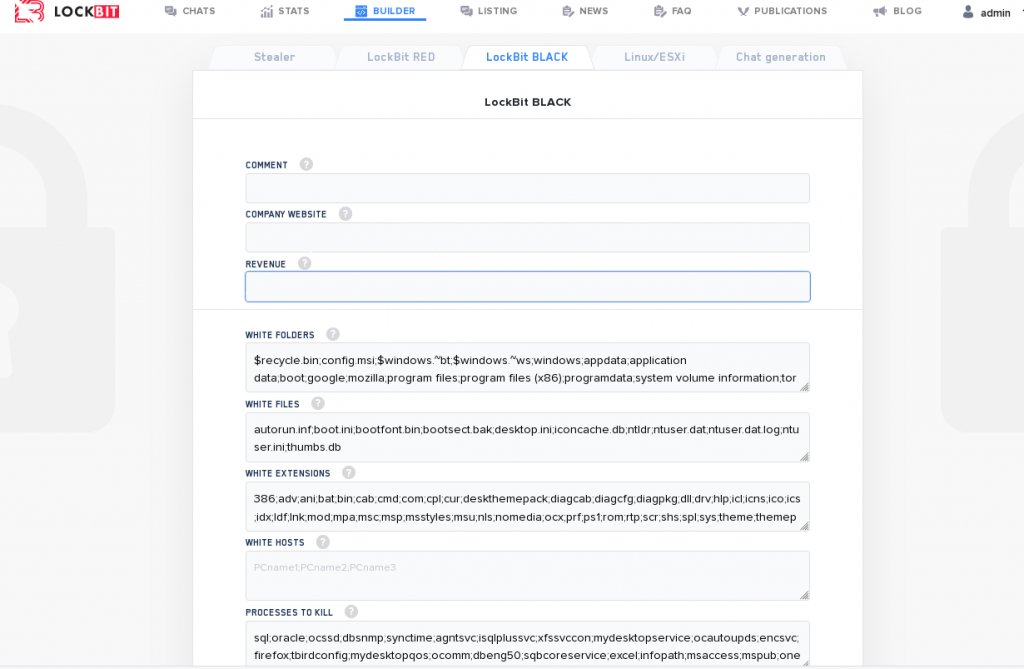
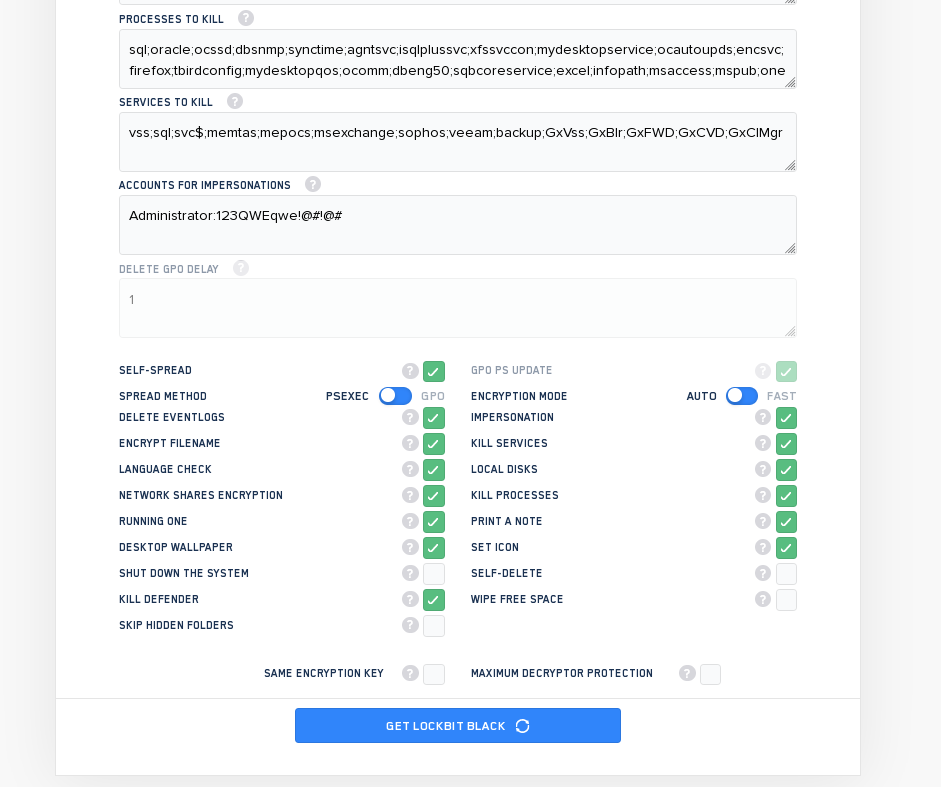
Leaked data about LockBit showed the back-end controls for the ransomware now seems to indicate that the creators have begun experimenting with the use of scripting that would allow the malware to self-spread using Windows Group Policy Objects (GPO) or the tool PSExec
This potentially makes it easier for the malware to laterally move and infect computers without the need for affiliates to know how to take advantage of these features for themselves, potentially speeding up the time it takes them to deploy the ransomware and encrypt targets.
A reverse-engineering analysis of the LockBit functionality shows that the ransomware has carried over most of its functionality from LockBit 2.0 and adopted new behaviors that make it more difficult to analyse by researchers.
It has also been observed that the ransomware runs with LocalServiceNetworkRestricted permissions, so it does not need full Administrator-level access to do its damage.
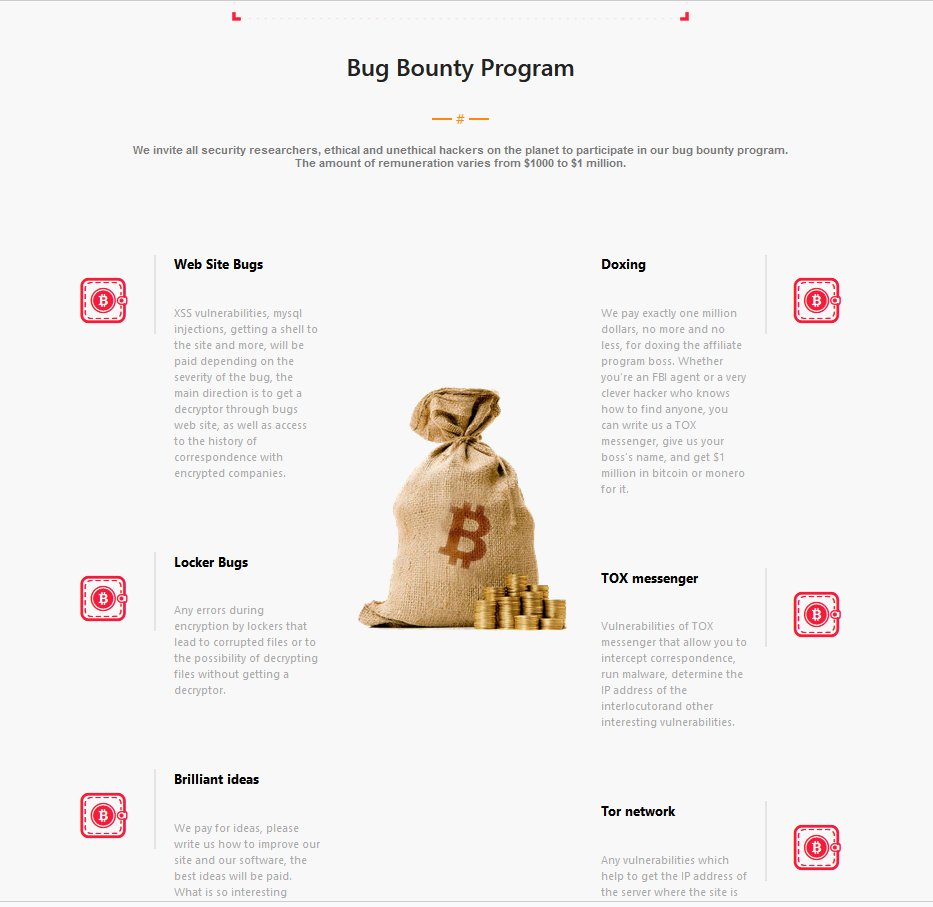
The criminal gang behind LockBit have also started to reach out to the wider hacking community to help improve their software, as well as offering $1M USD for people to doxx their own company executives and get them access to the corporate systems.
LockBit and Ukraine
Instances of LockBit attacks against UK companies have increased since ex-PM Boris Johnson visited Kyiv to meet with Ukrainian President Zelensky, and it appears that the UK’s support to the Ukrainian fight against Russia is directly linked to these attacks.

A Lockbit member said in a blog post published on the dark web last year: “We benefit from the hostile attitude of the West (towards Russia). It allows us to conduct such an aggressive business and operate freely within the borders of the former Soviet (CIS) countries.”
It could well be that the attack on the Royal Mail’s ability to send things overseas is a not-so-subtle message from the LockBit gang to the UK government to stop sending weaponry and support overseas too.
Could we see an escalation of LockBit attacks in the next few weeks now we have an announcement from the UK Government that the UK is to send Challenger tanks to Ukraine?













