Operation Endgame – a new approach to tackling cybercrime
This week has seen the launch of a new approach to tackling cyber crime from law enforcement agencies across the globe.
Operation Endgame is the name given to a series of ongoing actions to close down the illegal activities of numerous cyber crime gangs, but in a new move these actions will be posted on a dedicated website https://operation-endgame.com

The Operation is a joint effort between many agencies across the globe, including the UK’s National Crime Agency (NCA), Europol, The FBI, The national Police for of the Netherlands (Politie), The German Bundeskriminalamt, and many others. A number of industry partners have also been involved, including HaveIbeenPwnd, Bitdefender, Proofpoint, ZScaler, Spamhaus, and more.
The 1st stage of Operation Endpoint occurred on the 28th May which saw the takedown of sevelal high-profile botnets – this activity led to the arrest of four individuals, and 16 searches in various countries.
The botnets which were taken offline included:
- IcedID – Active since December 2022, IcedID has been observed abusing Google pay per click (PPC) ads to distribute IcedID via malvertising attacks. IcedID is detected as TrojanSpy.Win64.ICEDID.SMYXCLGZ. People searching online for certain applications such as Adobe, Anydesk, Discord, Teamviewer, etc. were shown links to spoof sites with app downloads that included the IcedID trojan malware.
- Smokeloader – Active since early 2011, Smokeloader has the ability to drop an array of different malware onto infected systems, including backdoors, ransomware, cryptominers, password stealers, point-of-sale malware and banking trojans. The malware exhibits advanced evasion strategies that make it difficult for traditional security solutions to detect and remove, and it is easily distributed via methods such as spam emails or malicious file downloads.
- SystemBC – Active since 2018, SystemBC is a command and control server malware that allows threat actors to access a remote machine to act as the launch pad for further attacks, thus hiding their true location and identities. The tool has been leveraged by various threat actors across several campaigns as well as used alongside many other malware families, including RHYSIDIA, BLACKBASTA, CUBA, GOOTLOADER, COBALTSTRIKE and EMOTET.
- Pikabot – Active since 2023, Pikabot is a malware loader that allows threat actors to load up different malware to an infected machine depending on what they wish to achieve. Many Pikabot victims are tricked into opening an infected .zip file which installs the malware.
- Bumblebee – Active since late 2021, Bumblebee has had 2 different methods of activity – the 1st iteration of Bumblebee used domain and identity spoofing as a way to gain additional credibility with victim organizations. The threat actors posed as employees of real organizations on social media, sometimes creating fake profile pictures using Artificial Intelligence. The group then began impersonating real employees using their real data taken from social media accounts and business databases. The threat actors sent spearphishing emails via spoofed email accounts. The 2nd iteration of Bumblebee used fake voicemail messages sent in an email. The voicemail links however led to a OneDrive file which contained compromised word documents. These files contained PowerShell commands that acted as multi-stage droppers for further malware.
A statement posted on the websites of many of the law enforcement agencies said:
It is the largest operation ever to combat botnets involved in ransomware worldwide, taking down these botnets and disrupting the entire infrastructure of many cybercriminals simultaneously. It is estimated that the financial damage caused by these criminals to companies and government institutions runs into hundreds of millions of euros.
In the Netherlands, the operation, led by the joint efforts of the High Tech Crime Team of the National Investigation and Intervention Unit and various police units, led by the Public Prosecution Service, led to the takedown of 33 servers in various data centers. More than 100 servers worldwide have been taken offline, and more than 2,000 domain names have been taken over.
Of the various botnets, more than ten thousand infected computer systems could be disinfected by uninstalling the malware.
The investigations running under Operation Endgame revealed that one of the main suspects has earned 69 million euros in cryptocurrency from his criminal activities and this will be seized as soon as possible.
The joint actions were carried out by authorities in the Netherlands, Germany, France, Denmark, United States, and the United Kingdom with support from Europol and Eurojust. In addition, with the cooperation of the aforementioned authorities, there have also been police actions in Ukraine, Switzerland, Armenia, Portugal, Romania, Canada, Lithuania and Bulgaria for the arrest or interrogation of suspects, searches or the seizure and downing of servers.
The Netherlands Politie released a video about Operation Endgame on YouTube – The video is in Dutch, but you can auto-generate subtitles in other languages, including English.
In possibly related news – a post on X by the team at vx-underground suggests that a number of other criminal gangs have suddenly disappeared from their online platforms:
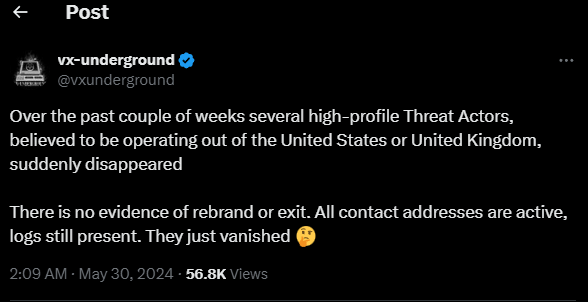
Those in question included Breached admins and users, and some affiliates working with the ALPHAV ransomware gang.
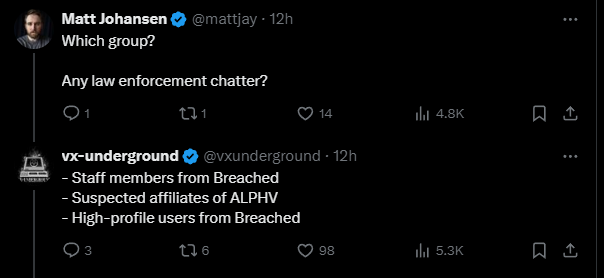
It does seem likely that these incidents are related to Operation-Endgame, hopefully the countdown clock on the website will reveal more …