Outlook vulnerability could expose Windows password
Microsoft released a security update last month to address the recently discovered vulnerability in Microsoft Outlook which, if triggered could leak your Windows password to a threat actor.
The vulnerability was discovered by researchers at Varonis, and is tracked as CVE-2023-35636 with a base CVSS score of 6.5 placing the vulnerability into the medium risk category.
How it works
Varonis researchers found three ways to trigger the vulnerability, but all of them involve a threat actor simply crafting an iCalendar invite with a specific set of values in the header data. These values will force the receiving Outlook client to attempt to authenticate with the sender and thus expose the victims NTLMv2 password Hash file.
Once the threat actor has the victims has file, they can attempt to recover the hashed password.
The attacker needs to include a header in the invite that indicates the “content-class” is set to“sharing,” then they need to include an “x-sharing-config-url” header that directs the victim to an .ics file path on the attacker’s machine.
If an Outlook user opens the calendar invite link (.ics file) the hashed password is sent to the sender (attacker) when Outlook attempts to authenticate on the attacker’s machine to retrieve the .ics file.
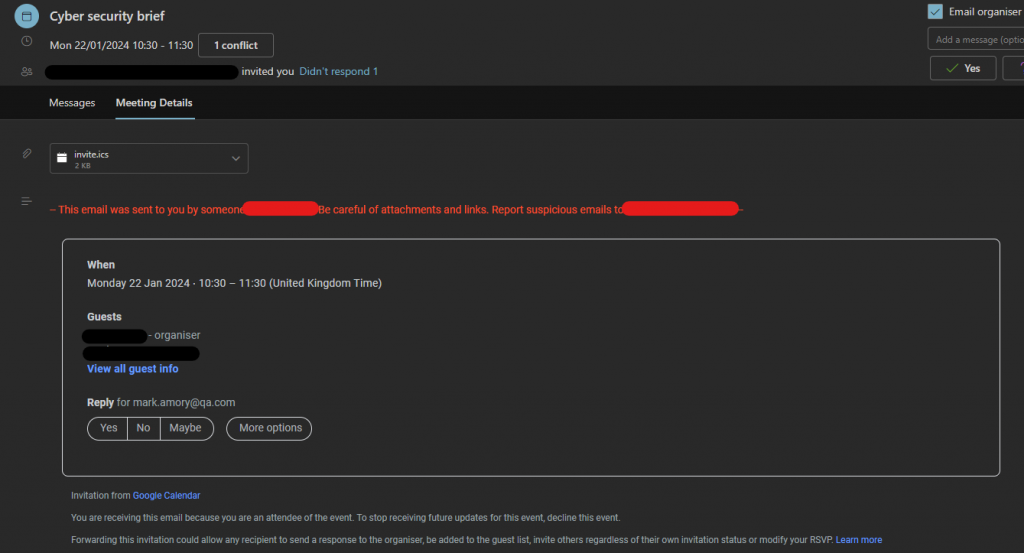
One of the ways the vulnerability can be exploited involves the victim having the Windows Performance Analyzer (WPA) installed – this is a tool widely used by developers, but not so much by the average user.
If the victim is running WPA, then the vulnerability is triggered by them receiving an iCalendar invite where the remote machine is specified with a wpa:// address.
The other two ways of exploiting the vulnerability are both triggered by targeting the search-ms:// feature of Windows Explorer with either the subquery parameter, or the crumb parameter set. Both parameters will force the explorer search utility to reach out across the Internet to a remote machine and attempt to authenticate by sending the NTLMv2 hash.
iCalendar
iCalendar was first defined as a standard as RFC 2445 in 1998 by the Internet Engineering Task Force (IETF). This document was authored by Frank Dawson of Lotus Notes Corporation (now owned by IBM) and Derik Stenerson of Microsoft.
The iCalendar standard was refined in 2009 as RFC 5545 by Bernard Desruisseaux of Oracle Corporation to resolve some ambiguities and deprecate a few features that were no longer needed.
iCalendar is used to import and synchronize events on various platforms such as Microsoft Office 365, Apple Calendar, Google Calendar, and Yahoo Calendar, etc.
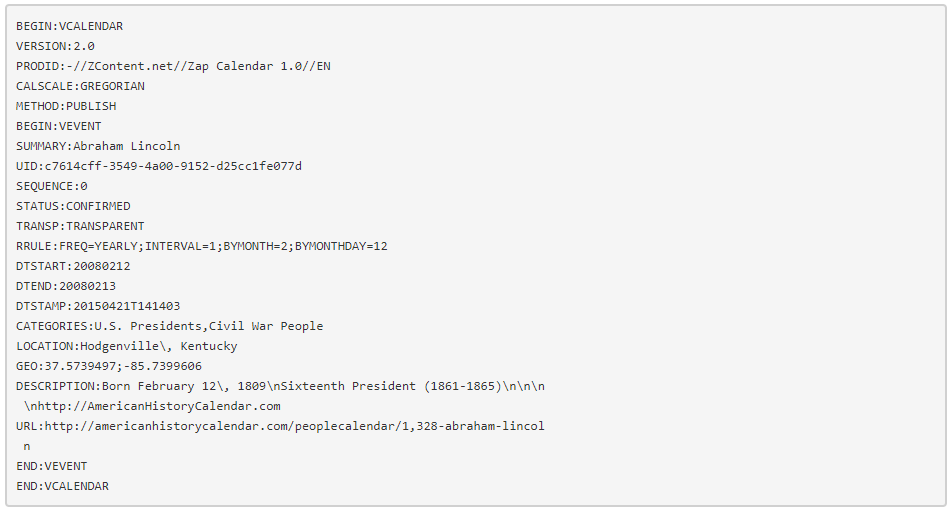
An iCalendar file (.ics) consists of numerous sections starting with “BEGIN:” and ending with “END:”.
The “VCALENDAR” section is the global section that holds all other sections. Other sections can include “VEVENT” for events
- “VTODO” for to-do item
- “VJOURNAL” for journal entries
- “VTIMEZONE” for time zone information.
Multiple sections of the same type can be repeated. For example, multiple “VEVENT” sections can occur in an iCalendar file to describe multiple events.
The image below shows a simple iCalendar file with a single event:
The original iCalendar standard allowed only plain text as part of an event description. HTML markup, such as font attributes and layout tags were not allowed in the text description field.
“X-” fields are allowed for non-standard, experimental parameters – e.g. X-ALT-DESC is a non-standard value for an images alternative text.