Bypassing Windows security with DLL search order hijacking
Security researchers at securityjoes.com have published a paper detailing a new mechanism that allows threat actors to bypass Windows 10 & Windows 11 security controls by leveraging DLLs commonly found in the trusted WinSxS folder. Successful exploitation allows an attacker to to circumvent high privilege requirements to execute malicious code in applications within any location on an affected machine.
What are DLLs
Windows applications utilise files called DLLs (Dynamic Link Libraries) which are prewritten code modules that can be shared among different applications – this reduces the overall size of an applications code as it doesn’t need to have code sections for things like copy, paste, save, etc. The application just needs to call the required DLL for the function to be available.
The use of DLLs helps promote the modularisation of code, code reuse, efficient memory usage, and reduced disk space. This ultimately means that the operating system and applications load faster, run faster, and take less disk space on the computer.
Additionally, when programs are written with DLL use in mind, updates are easier to manage.
When an update is produced, it can be applied to a module without affecting other parts of the program. For example, you may have a payroll program, and the tax rates change each year. When these changes are isolated to a DLL, you can apply an update without needing to build or install the whole program again.
DLL Dependency
One problem with using DLLs is that of DLL dependency.
When a program (or another DLL) uses a function from another DLL, a dependency is created. The program is no longer self-contained, and as such, the program may experience problems if the dependency is broken. For example, the program may not run if one of the following actions occurs:
- A dependent DLL is upgraded to a new version.
- A dependent DLL is fixed.
- A dependent DLL is overwritten with an earlier version.
- A dependent DLL is removed from the computer.
These actions are known as DLL conflicts and if backward compatibility is not managed, the program may not successfully run.
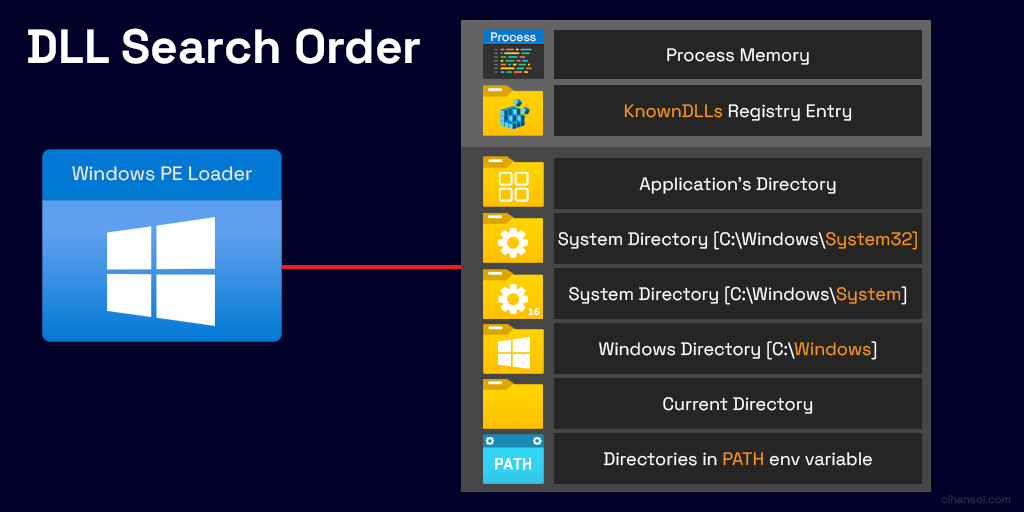
DLL search order
It’s common for multiple versions of the same DLL to exist in different locations within an operating system. You can control the specific location from which any given DLL is loaded by specifying a full path, but if you don’t, then the system searches for the DLL at load time as described below:
- DLL redirection.
- API sets.
- Desktop apps only (not UWP apps). SxS manifest redirection.
- Loaded-module list.
- Known DLLs.
- The package dependency graph of the process. This is the application’s package plus any dependencies specified as
<PackageDependency>in the<Dependencies>section of the application’s package manifest. Dependencies are searched in the order they appear in the manifest. - The folder the calling process was loaded from (the executable’s folder).
- The system folder (
%SystemRoot%\system32)
DLL Search order hijacking
DLL Search order hijacking is a known method of compromising a machine. The attack can be achieved in various ways, but one common way works by planting trojan DLLs in a directory that will be searched before the location of a legitimate library that is requested by an application, causing Windows to load their malicious library when it is called for by the victim application.
If a search order-vulnerable program is configured to run at a higher privilege level, then the adversary-controlled DLL that is loaded will also be executed at that higher level. In this case, the technique could be used for privilege escalation from user to administrator / SYSTEM or from administrator to SYSTEM, depending on the program.
Programs that fall victim to path hijacking may appear to behave normally because malicious DLLs may be configured to also load the legitimate DLLs they were meant to replace.
WinSxS
The new method of DLL hijacking which was discovered by securityjoes deliberately targets DLLs which reside in the WinSxS directory.
The WinSxS (Windows Side by Side) folder is a critical component in the maintenance and recovery of the Windows operating system. Its primary function is to store various versions of important system files side by side. When Windows undergoes updates, it retains the previous versions of components within the WinSxS folder. As a result, the size of the WinSxS folder tends to increase with each Windows update.
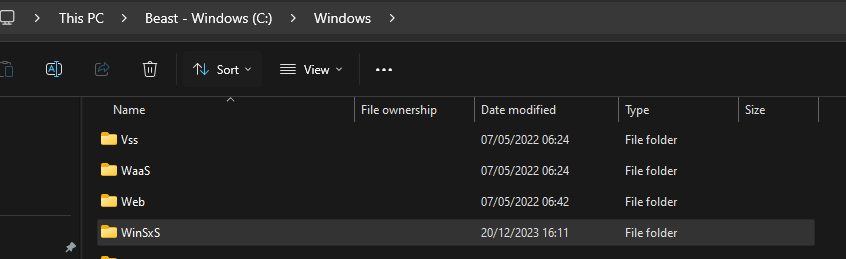
The folder is typically located at C:\Windows\WinSxS
In Windows Server, the WinSxS folder serves additional roles that enhance server capabilities. It holds critical files necessary for system restoration, aiding in recovery processes. It also functions as a protective mechanism, enabling users to revert from problematic system updates to a stable state when necessary, contributing to system resilience and reliability.
Targeting files in the WinSxS folder allows a threat actor to:
- Circumvent High Privilege Requirements: By targeting applications in the WinSxS folder, it eliminates the need for elevated privileges to execute malicious code within applications located in a Windows folder.
- Eliminatethe Need for Additional Binaries: Leveraging the WinSxS folder eliminates the requirement to introduce additional, potentially detectable binaries into the attack chain. Since Windows already indexes these files in the WinSxS folder, there’s no need to bring your own vulnerable application.
- Enhance Stealth: Executing malicious code within the memory space of an application running from the WinSxS folder enhances stealth and minimizes the risk of detection. Security tools and analysts may be less likely to flag this approach as it leverages trusted components already present in the Windows environment.