(29/12/23) Blog 363 – NASA launches space industry cyber security guide
As the latest space race hots up, NASA has published its first Space Security Best Practices guide for organisations who want to be a part of this exciting industry.
The 56-page guide was released to a select audience earlier this year, but has now been released for public consumption.

The guide is based on the existing NIST Special Publication – SP800-53 – Security and Privacy Controls for Information Systems and Organizations which was last updated in 2020, however NASA say that their guide “serves as a translation guide between NIST verbiage and NASA flight project parlance.“
The document also draws on guidance from the Space Systems Protection Standard which was initially published in 2019 and last updated in 2022.
The guide is to be used as an initial starting point to mitigate against any efforts to deny, degrade, disrupt, deceive, or destroy information and technology used to accomplish NASA’s mission success.
Fears about the risks faced by space missions and infrastructure were exacerbated in February 2021 when threat actors believed to be aligned with Russia disabled Ukrainian satellite operations as Russia began its invasion of Ukraine.
The new guide has been developed as a response to Space Policy Directive 5, a document issued under the Trump administration that outlines a series of cyber security principles for protecting the space sector.

Satellite hacking
Earlier this year I posted a story about the first successful hack of a satellite which was in Earths orbit. The hack was achieved as part of a competition, but it highlighted the need for a stronger set of security controls.
Currently, most satellite communications hacking is limited to blocking GPS signals – this isn’t actually hacking the satellites used for GPS, but rather just creating enough RF noise to drown out the GPS signal.
A common use of GPS jammers is by taxi and HGV drivers evading rules on maximum driving hours or trying to stop employers from tracking them.
In some parts of the world, GPS jamming has been used for more sinister purposes – South Korea was subject to a major campaign of GPS jamming from North Korea in 2016, affecting ship and aircraft navigation.
Currently, a large number of GPS signals around Ukraine are being jammed, as well as those around Israel & Palestine – as seen in the image below:
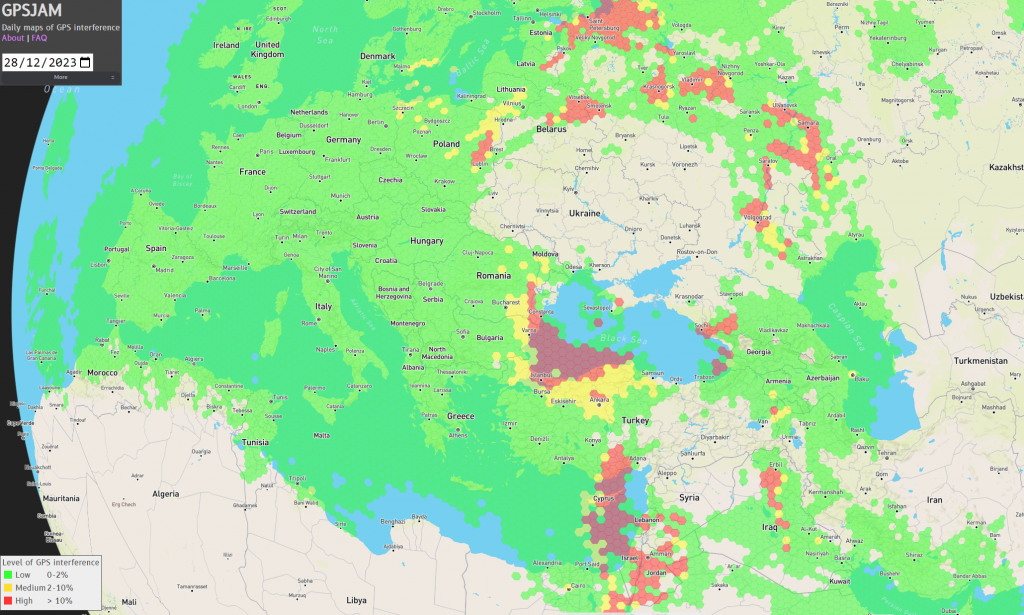
However – If nation states, or other malicious threat actors can manage to compromise the satellites responsible for the GPS data, then it would be very difficult to stop an attack, or even detect that one is taking place until it is too late.
Air Traffic Control (ATC), search and rescue operations, the electricity grid and mobile phone services are all vulnerable to GPS jamming fallout. The London Stock Exchange has been subject to repeated GPS outages, affecting the time-stamping of financial transactions. An article in the Economist in 2013 highlights the effect small GPS jammers have on the Stock Exchange.
An article in the New Scientist tells the story of how in 2007, a navy exercise resulted in the loss of GPS communications in San Diego harbor which meant that residents of the city were unable to withdraw cash from ATMs and doctors’ emergency pagers stopped working – it took 3 days to identify the ships as the cause.













