(11/12/23) Blog 345 – 5Ghoul – new attacks against 5G devices discovered
Security researchers at Asset Research Group – a part of the Singapore University of Technology and Design have released a paper detailing their research into the security of 5G devices and infrastructure.
The paper discloses a total of 14 vulnerabilities (10 CVEs), of which 10 affect commercial off-the-shelf (COTS) edge devices employing 5G modems from Qualcomm and MediaTek. At least two other vulnerabilities are not disclosed yet due to confidentiality.
Named 5Ghoul, the vulnerabilities have the potential to cause various undesirable effects on 5G handsets, and networking infrastructure, including downgrade attacks, and system crashes.
A notable feature of currently disclosed 5Ghoul vulnerabilities is that they can all be fairly easy to exploit by an attacker, as no information about the victim’s SIM card is required. This is due to the fact that 5Ghoul vulnerabilities can be exploited to launch an attack even before any NAS authentication procedure completes.
How does it work?
The 5G network architecture consists of three key components:
- The gNodeB (gNB)
- A.K.A. base station in a traditional mobile network, the gNB serves as the access point for the wireless communication between the UE and the 5G core network.
- User Equipment (UE)
- The UE refers to end-user devices, such as smartphones and tablets (in general, any 5G-enabled device), that connect to the 5G network through the gNB.
- Core Network
- The Core Network acts as the backbone of the 5G architecture by providing control and management functions, including authentication, security, mobility management, session establishment, and data routing between network entities.
To launch an attack, the attacker only needs to impersonate a legitimate gNB using its known Cell Tower connection parameters (e.g., SSB ARFCN, Tracking Area Code, Physical Cell ID, Point A Frequency).
Obtaining cell tower data can be easily accomplished using freely available applications like Cellular-Pro, or some other such app.
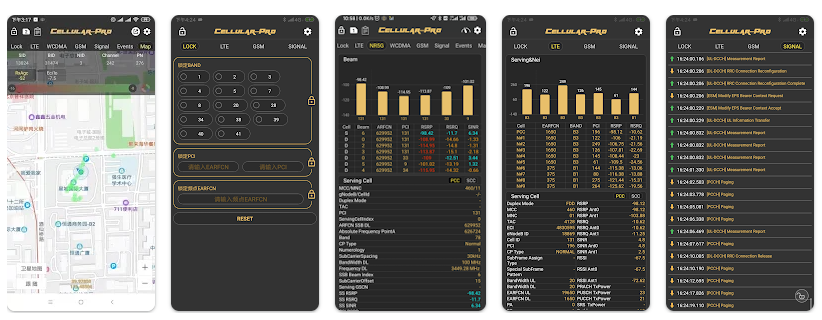
Once an attacker is nearby a target UE and the Received Signal Strength Indicator (RSSI) of the adversarial gNB is higher than the legitimate gNB, the target UE will automatically connect to the adversarial gNB and begin an exchange of data.
If the device is using a chipset with vulnerable firmware, then an attack can take place by either sending the device a malformed RRC Connection setup (Radio Resource Config) message, or a malformed NAS Authentication Request (Non-Access Stratum).
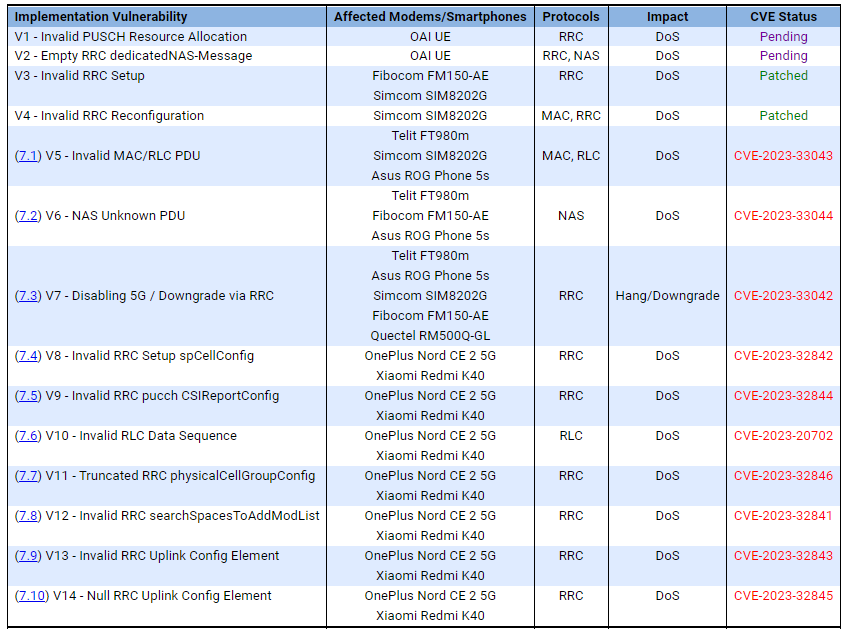
The table below shows the effects of various data sent to vulnerable devices.
A video released by the researchers shows the effects of one attack which completely disables 5G connectivity on devices with vulnerable Qualcomm chipsets. Even when the attack is stopped, the targeted device will not resume 5G connectivity – the SIM has to be manually removed from the device to perform a hard reset to re-enable 5G access.
Not just mobiles
The attacks demonstrated by the researchers don’t just impact mobile handsets – any device capable of accessing a 5G network can be affected – including some routers.
In the below video, the researchers show an attack against a CPE (Customer Premise Equipment) router, causing it to crash and reboot.
The researchers conducted analysis of all known devices with affected chipsets, and have produced a spreadsheet of known affected devices – the list contains over 700 affected devices from manufacturers such as Apple, Asus, Google, Huawei, Lenovo, LG, Motorola, and many more.