(01/12/23) Blog 335 – Microsoft warns of new ransomware campaign
Threat analysts at Microsoft have issued a warning of a new ransomware campaign which appears to have risen from the ashes of the recently dissolved Qakbot campaign.
The recent MS Threat Intelligence update states that through their investigations, Microsoft has seen infections of Danabot (Tracked by MS as Storm-1044) which ultimately lead to hands-on keyboard activity by the Twisted Spider ransomware gang (Tracked by MS as Storm-0216).
Danabot malware
The Danabot malware is described as a modular information-stealing malware which focuses on gaining persistence on a victim machine.
Initially a banking-trojan designed to steal financial information, Danabot has evolved over time to be a full-time info-stealing malware tool. Infections are achieved via Social Engineering a victim into opening an infected file. The latest campaign delivers Danabot via malvertising.

What is malvertising?
Malvertising is a malicious attack that involves injecting malicious code into legitimate online advertising networks which are then displayed to users as they browse the web. Clicking one of these infected adverts takes users to unsafe destinations, such as fake sites, or sites with additional malware in them which ultimately infects the visitors device.
Post-infection activities
Once on a machine, the malware runs a bot which scans the victim machine for as much information as possible, including:
- Targeting Browsers, FTP and SSH services, and email clients
- Extracting data from the clipboard
- Keystroke logging
- Crypto-wallet stealing
- File & folder stealing
- HTML injections
- Web redirection / web blocking
- Installing Tor client as backup option for data exfil
The malware also installs a server function to the victim machine to facilitate the connection of a RAT which allows for attackers to manually issue commands to the victim machine – giving the attackers “hands-on” capabilities.
The Danabot malware was first seen in 2018 and has been consistently updated with new capabilities and obfuscation techniques over the years.
As well as being capable of hiding on a victim machine, the Danabot malware also employs a large number of techniques to avoid analysis and debugging in an attempt to thwart reverse engineering of the malware as part of forensic analysis. For those interested in how DanaBot achieves this, ZScaler wrote a comprehensive blog about these techniques here.
Qakbot reborn?
I posted about the dismantling of the Qakbot ransomware network back in August. The FBI said at the time that the operation, dubbed Op DuckHunt was “the most significant technological and financial operation ever led by the Department of Justice against a botnet.”
While the operation was successful in dismantling the Qakbot Command and Control network, no-one was arrested and as such, it meant that the operators simply had to rebuild their network, and develop a new ransomware variant – which it appears they have now done.
The post by Microsoft’s Threat Intelligence team states that Storm-0216 had historically received hand-offs of compromised systems from Qakbot operators, but have since pivoted to leveraging different malware for their initial access.
The current campaign appears to be using a private version of the Danabot malware as opposed to the malware-as-a-service version used by others. In the infections seen by Microsoft, the Danabot malware collects user data, exfiltrates it to a C2 server and then threat actors use RDP connections and finally hand-off compromised machines to the Twisted Spider gang.
Twisted Spider – what’s in a name?
Twisted spider is the name given to the threat actor by CrowdStrike. The Taxonomy used by CrowdStrike uses the term Spider to denote a threat actor whose primary goal is financial gain. Threat actors who are tied to nation-states are denoted by that countries national animal, so Russian threat actors are <something>+Bear (e.g. Fancy Bear), Chinese threat actors are <something>+Panda (e.g. Putter Panda). and those threat actors who are deemed to be hacktivists are termed Jackals.
Twisted Spider is just one of a number of financially motivated threat actors tracked by CrowdStrike, as shown in the image below.
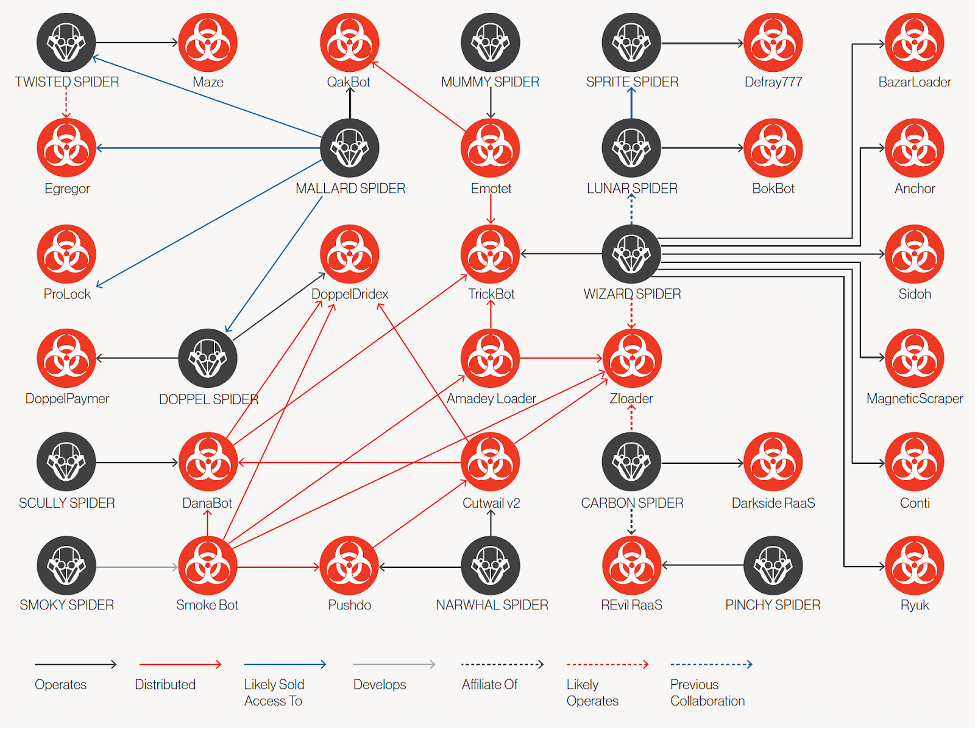
CrowdStrike has observed formal collaboration among eCrime adversaries as well as shared tactics. In June 2020, the self-named “Maze Cartel” was created when TWISTED SPIDER, VIKING SPIDER and the operators of LockBit ransomware entered into an apparent collaborative business arrangement. After this occurred, leaks associated with VIKING SPIDER’s Ragnar Locker began appearing on TWISTED SPIDER’s dedicated leak site and Maze ransomware began deploying ransomware using common virtualization software, a tactic originally pioneered by VIKING SPIDER.