(28/11/23) Blog 332 – Slovenia’s largest power supplier in ransomware attack
Cyber security experts are working to recover systems at Slovenia’s biggest power distribution supplier – HSE which was hit with a ransomware attack on Wednesday 22nd November.
Officials at HSE reported on Sunday that the situation was under control, assessing there appeared to be no major damage, but could not pinpoint the source of the incident yet.
HSE general manager Tomaž Štokelj said he was pleased with the work done by the in-house services and several external experts in resolving the situation.
“Based on what we’ve seen we can be optimistic that there will be no major consequences both in terms of system security and the impact on the company’s business performance,” he said.
He added that “the operational system, which serves as a control system for the operation of the power plants, is functional to a large extent”
Uroš Svete, director of the Government Information Security Office, said “I believe that the process itself, both the detection of the incident itself and the reporting and engagement of all actors, at expert, technical, company and the level of state authorities, has been appropriate and in line with the national cyber incident response plan. So, in reality, at the moment, the situation in this case is under control“
In a later statement, the Slovenian Government’s Information Security Office issued a reassuring statement in a press release saying that “HSE group power plants operate smoothly, Slovenia’s electricity supply remains safe and reliable“.
HSE
HSE operates the Šoštanj thermal plant, which accounts for around a third of domestic electricity production, as well as chains of hydro plants on the Drava, the Sava and the Soča. The group accounts for roughly 60% of domestic electricity production.

Who carried out the attack?
Rumours online suggest that the attack has been carried out by the Akira ransomware gang which formed from the ashes of the now defunct Conti gang, although at the time of writing, nether HSE have mentioned this, nor is there any posting related to the attack on the Akira dark web leak site.
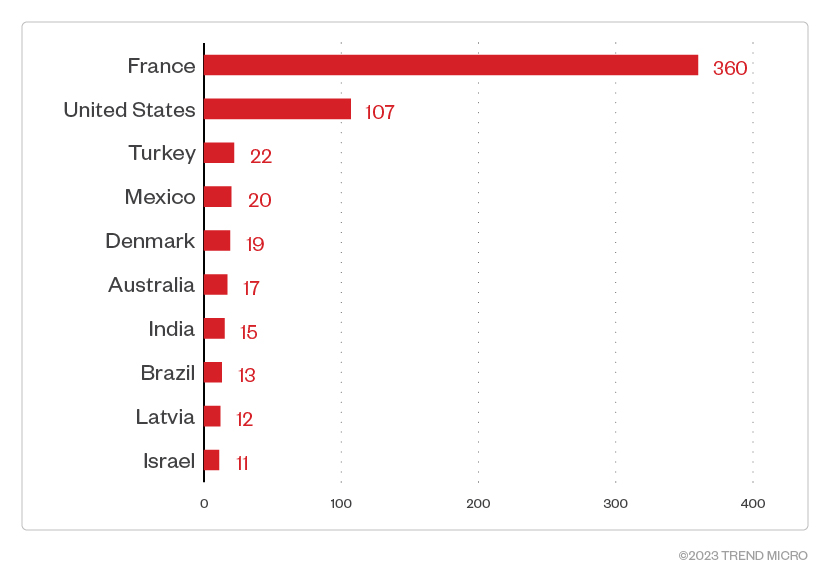
First seen in March this year, the Akira gang has carried out attacks in numerous countries across the world with France being the most targeted country and the US in second position.
The gang utilises the now familiar double extortion tactic where they steal victims’ critical data prior to encrypting devices and files.
Akira operators in the past have provided victims the option to pay for either file decryption or data deletion; they don’t force victims into paying for both. According to reports, ransom demands for Akira typically range from US$200,000 to over US$4 million.













