(26/11/23) Blog 330 – ClearFake campaign targets Windows and Mac users
A malware campaign designed to trick users into installing malicious code under the guise of a browser update has now started to target Apple Mac users.
The campaign which is called ClearFake, first started to be seen in July of this year targeting users of the Chrome browser on Windows machines. It was then expanded to target MS Edge and Firefox users.
If users follow the fake update instructions, they end up actually installing one of a number of malicious exploits which attackers then use to steal data such as usernames, passwords, crypto-currency wallets, stored payment data, and other local files.
For Windows users, the malware which has been seen to be downloaded has included RedLine, Amadey, and Lumma – all are classed as info-stealers
Attackers have now extended their reach to target MacOS users by using the ClearFake browser alert to distribute malicious DMG files. A DMG file is a Disk Image File used by Apple devices to install programs and apps and is the file of choice for downloading compressed application installers from the Internet to Apple devices.
The malware seen being used against Mac usres is called Atomic, which is another Info-stealer sold for around $1,000 to attackers.
The campaign has been called ClearFake because of the majority of the malicious code in the fake web pages is not obfuscated in any way, other than some simple Base64 encoding.
Using Blockchain to evade detection
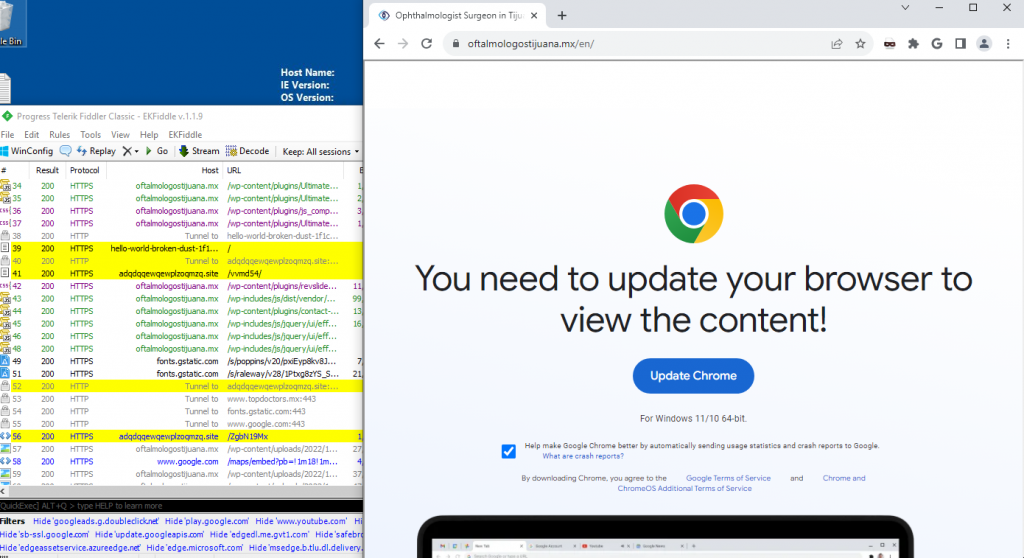
The main delivery vector of the ClearFake hackers is to compromise a vulnerable WordPress website and use that site to host their malicious code.
The attackers use a technique called EtherHiding to distribute code to victims which is very difficult to detect and block.
Etherhiding uses a feature of blockchain technologies called Smart Contracts to automate the process of running code.
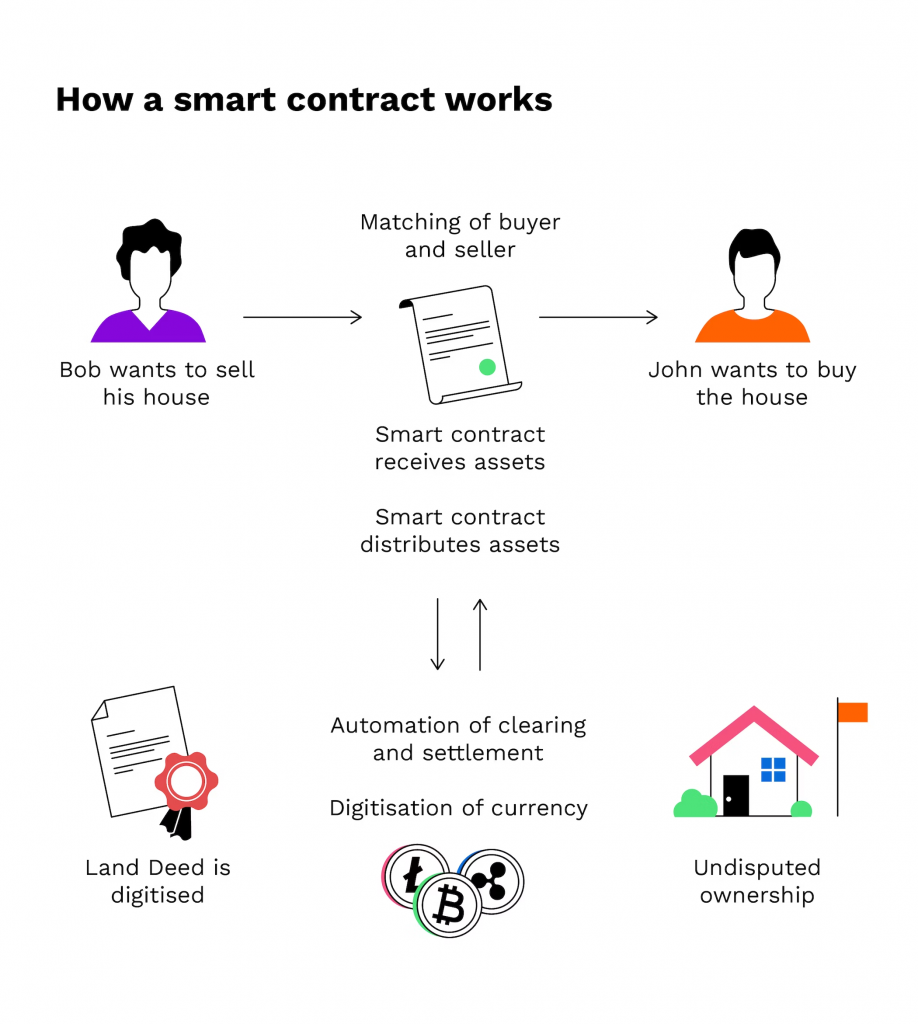
A Smart Contract is a program stored on a blockchain that runs when a set of predetermined conditions are met. They are typically used to automate the execution of an agreement so that all participants can be immediately certain of the outcome, without any intermediary’s involvement or time loss.
Smart contracts are used in many places to automate what used to be time consuming events. One example of a smart contract is in the transferal of title deeds when buying properties. The traditional way deed transfers were conducted was to get conveyancing lawyers to call each other to check bank account payments to see if funds had been transferred. This could take hours, or days depending on how busy the involved parties were. With smart contracts, this process can now take milliseconds.
In the ClearFake attacks, the attackers inject malicious scripts into vulnerable websites which allows them to load the Binance Smart Chain (BSC) JS library and fetch further malicious scripts from the blockchain which are then injected into the site to trigger the download of the third-stage payload, this time from the threat actors Command and Control (C2) servers.
The IP address of the C2 server is referred to directly from the blockchain, allowing the attackers to quickly and easily change it to evade blocks.
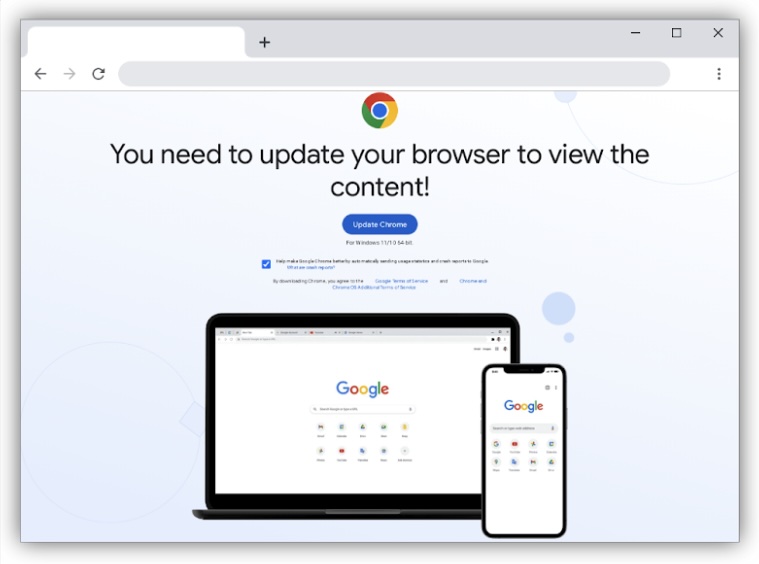
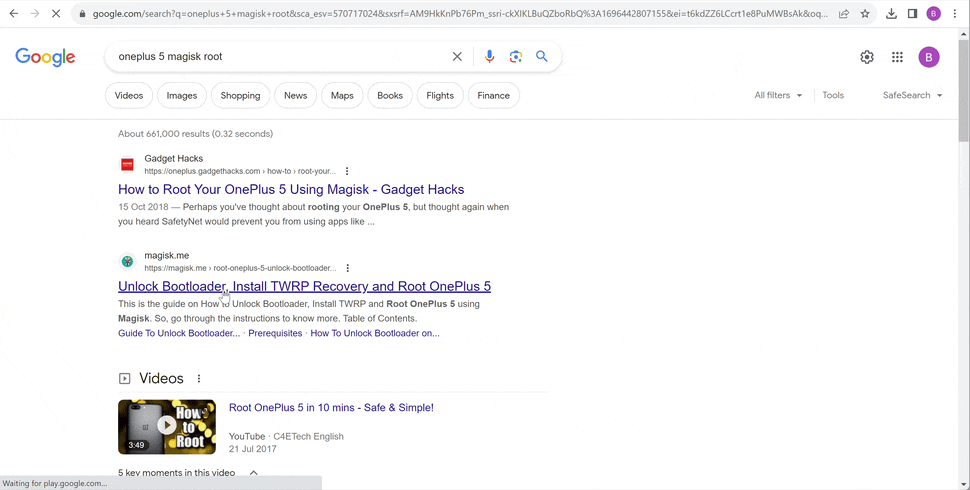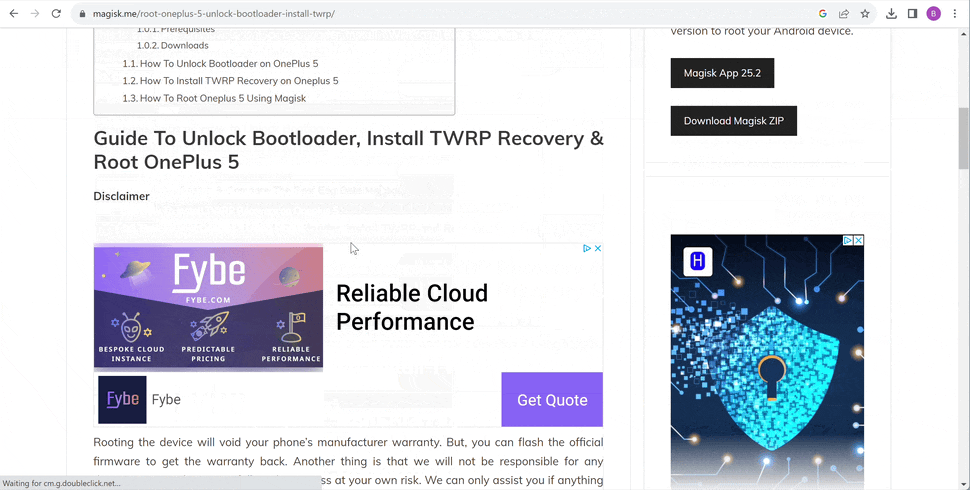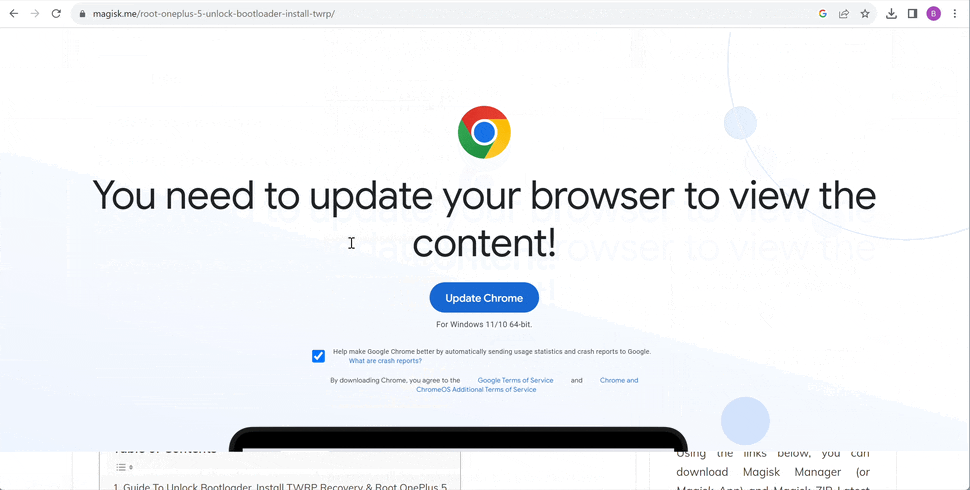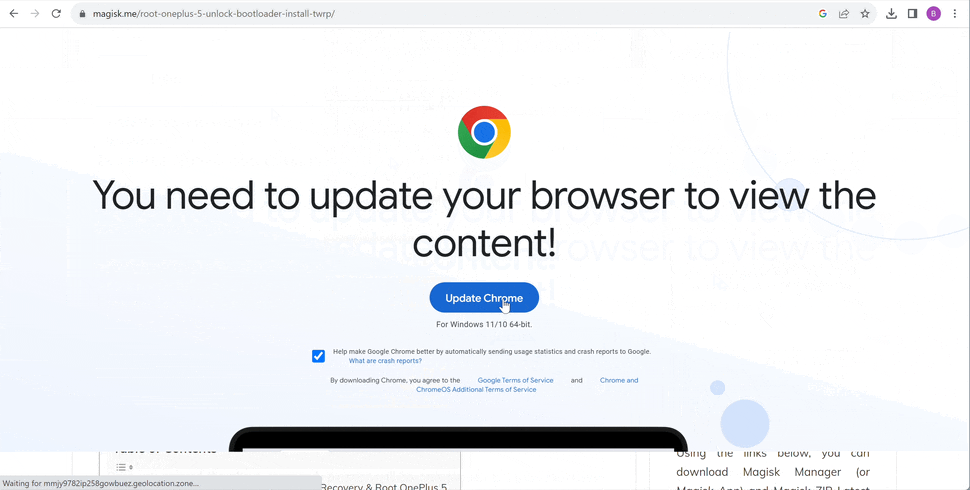
These third-stage payload then runs in the victims browser to show a fake overlay on the site they are viewing that prompts users to update their browser to continue being able to access the sites content.
Free and easy attack method
This novel way of hosting malicious code offers a very inexpensive, and unblockable way of running operations for threat actors.
To facilitate the attack, the attackers build a Smart Contract on the Blockchain at a fairly low cost. This contract holds the malicious code which infects the victim.
Once on the blockchain, the code can never be blocked or taken offline – such is the nature of blockchain technologies.
The code which is injected into the victim website conducts what is known as a eth_call which is a read-only and cost-free operation.
eth_call was originally designed to simulate contract execution for testing smart contracts without any real-world impact. As such, it is not even recorded on the blockchain.
So by using the eth_call in an attack, threat actors get a free, untracked, and robust way to get their malicious payload onto victim systems without leaving traces.
Once downloaded, the malware then calls to the C2 server for the final stage payloads. If these calls get blocked, then all the attackers need to do is make a tiny change to the data in the blockchain, and a whole new domain can now be used for the C2 connections.
These changes cost the attackers a very negligible amount – often in the realms of 0.0001 to 0.0005 BNB which is approx. 2p – 9p