(23/11/23) Blog 327 – RFC 9424 – An NCSC first
The UK’s National Cyber Security Centre (NCSC) has published it’s 1st ever Request For Comments (RFC) to create an Internet Standard.
The RFC is titled “Indicators of Compromise (IoCs) and Their Role in Attack Defence” and is designed as a document to help support organisations and businesses when designing secure systems.
One of the co-authors was Ollie Whitehouse, who helped put the document together before he became the new Chief Technology Officer (CTO) at NCSC. Ollie took up the role with NCSC in September this year. Prior to joining the NCSC, Ollie was CTO at NCC Group and also ran a security company called BinaryFirefly helping organisations create a strong security posture.

RFC 9424
The new RFC which can be read via the Internet Engineering Task Force (IETF) RFC Tracker identifies the typical Indicators of Compromise organisations should be aware of which common threat actors display at different stages of an attack.
IoCs are described as observable artifacts relating to an attacker or their activities, such as their tactics, techniques, procedures, and associated tooling and infrastructure.
By understanding IoCs organisations can configure their security controls to be more aware of these artifacts and help boost their defensive posture.
Pyramid of Pain
To help understand the often complex nature of attacks, the RFC introduces the concept of the Pyramid of Pain (PoP) – a simplistic diagram which identifies types of IoCs and the degree of pain a typical adversary experiences as part of changing the activity that produces that artifact. The greater pain an adversary experiences (towards the top), the less likely they are to change those aspects of their activity and the longer the IoC is likely to reflect the attacker’s intrusion set.
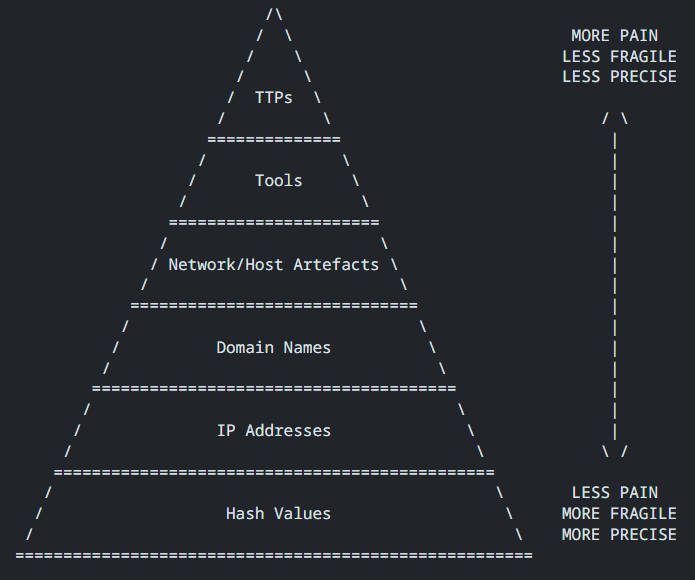
By way of an example, the RFC describes how the PoP can be used to see how a particular IoC can be used to help protect a network, and how painful it is for both defender and adversary if that IoC is used.
On the lowest (and least painful) level are hashes of malicious files. These are easy for a defender to gather and can be deployed to firewalls or endpoint protection to block malicious downloads or prevent code execution. Not much pain for a defender to do this.
Hashes are precise detections for individual files based on their binary content. To subvert this defence, however, an adversary need only recompile code, or otherwise modify the file content with some trivial changes, to modify the hash value. Not much pain for an adversary to do this.
At the highest level of the PoP are Tools, Tactics, and Procedures (TTPs). These take intensive effort to diagnose on the part of the defender, (much pain) but they are fundamental to the attacker and campaign and hence incredibly painful for the adversary to change.
Hopefully, this will be the first of many RFCs the NCSC publishes in to the IETF to seal our countries place as a leader in technology security.













