(21/11/23) Blog 325 – Rhysida gang behind British Library attack
At the end of October, I posted about a ransomware attack against the British Library, which had rendered most of the facilities and services offered by the library’s sites in London and Yorkshire inoperable.
That attack is still being felt by the British Library as many of its services, including its website, payment systems, onsite WiFi networks, and more still being out of action.
In a thread on X.com last week, the library admitted that they were still unable to confirm if any personal data of customers had been compromised in the attack.
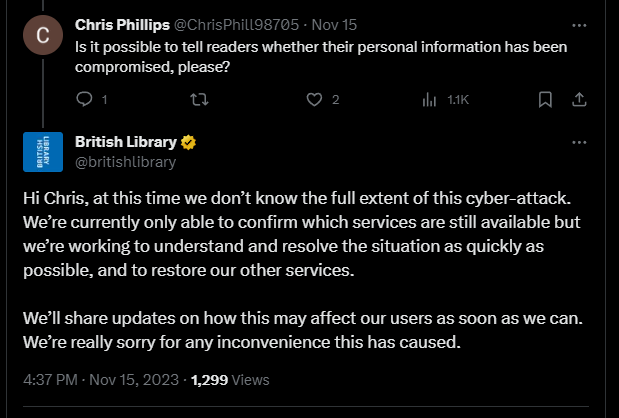
Well the answer to that question appear to have now been answered.
Rhysida announce breach
The fairly new ransomware gang known as Rhysida has released a post on their dark web leak site suggesting that they were the ones behind the attack, and have offered the data stolen for sale with bids at 20 BTC (roughly £600,000)
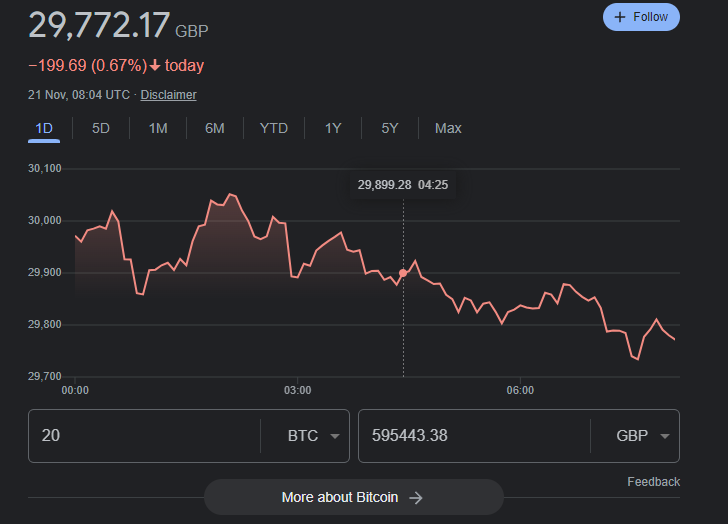
The gang have posted a screenshot of what appears to be multiple passport photos along with other documents as proof of their attack, and the data for sale.

The British Library has yet to confirm that this gang is the one behind the attack.
Who are Rhysida?
Rhysida is a new ransomware-as-a-service (RaaS) group that has emerged around May 2023.
Rhysida appear to be still in early stages of development, as indicated by a lack of advanced features in their attack software and the program name Rhysida-0.1.
The ransomware leaves PDF notes in all affected folders, instructing the victims to contact the group via their dark web portal and to pay the ransom in Bitcoin.
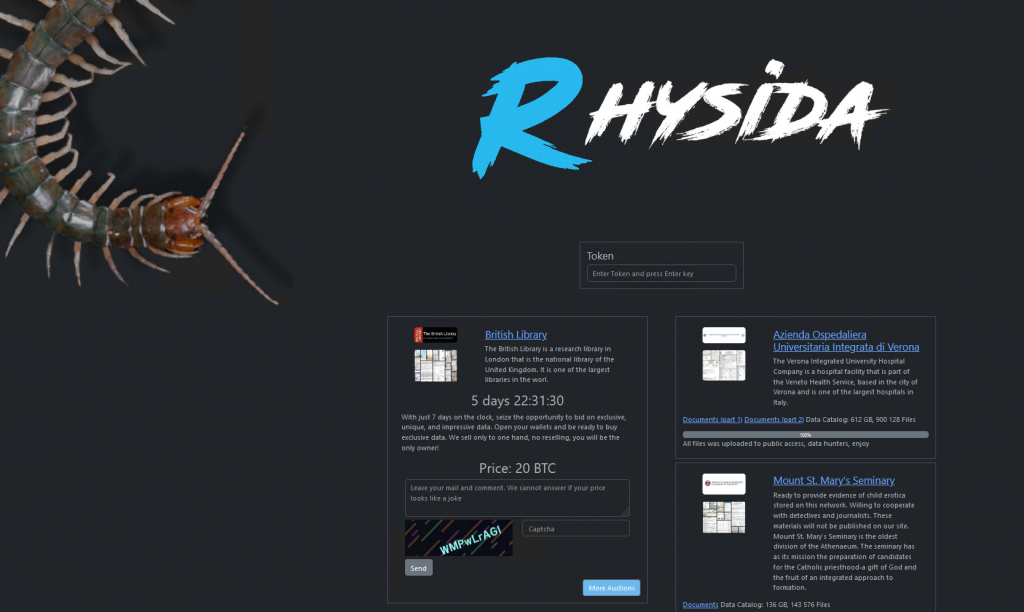
Rhysida describes itself as a “cybersecurity team” that aims to help victims highlight potential
security issues and secure their networks. While not much is known about the group’s origins or country
affiliations, the name Rhysida is a reference to the Rhysida genus of centipede which is found in the Neotropics, Indo-Malaya, and Africa and is reflected as the logo on their victim blog.
Primary methods of Rhysida malware deployment include breaching targets’ networks via phishing attacks, and by dropping payloads across compromised systems after first deploying Cobalt Strike or similar command-and-control frameworks.
For the encryption phase, Rhysida uses a 4096-bit RSA key with the ChaCha20 algorithm. After the
encryption details are established, Rhysida enumerates files and folders connected to the system. The
main function ends by calling a PowerShell command to delete the binary after encryption has completed.
Victims of the gang are distributed throughout several countries across Western Europe, North and South America, and Australia, loosely aligning the group’s targeting with other ransomware operations that avoid targeting former Soviet Republic or bloc countries in Eastern Europe and Central Asia’s Commonwealth of Independent States.













