(28/10/23) Blog 301 – Ransomware gangs turn to Violence-as-a-Service
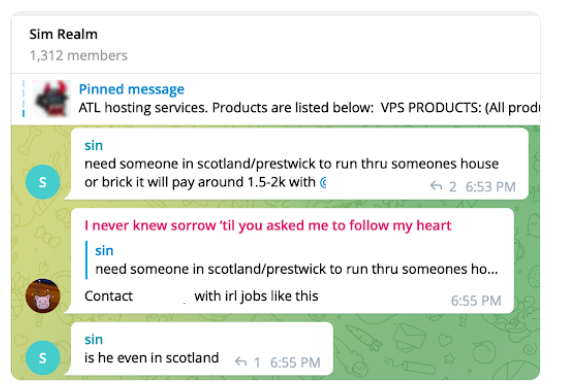
A recent report by independent journalists and researchers from 404media.co highlights an emerging trend which shows that some ransomware gangs are turning to another type of criminal gang to further their attacks – those who offer Violence-as-a-Service
In order to gain access to high-profile targets, when traditional social engineering attacks fail, some ransomware gangs are enlisting the help of SIM-swapping gang “the comm” who specialise in both electronic attacks, but also more real-world, physical brutality.
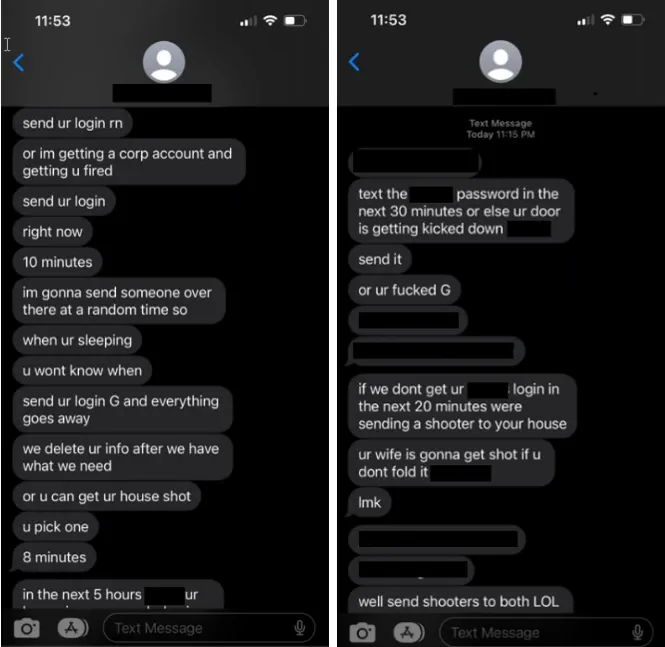
The Comm target employees of the ransomware gang’s prospective victims and threaten them with violence if they don’t offer-up access credentials to their company networks.
Octo Tempest is an affiliate of Blackcat / AlphaV – the ransomware gang behind multiple high-profile attacks on victims including The NHS trust – Barts Health, Reddit, Western Digital, Ring, and many others.
The Comm
The comm are a wide collective of individuals who are loosely connected over comms channels such as Discord and Telegram who will extort monies, and sensitive data for victims with threats of physical violence, and in some cases actual attacks.
There appears to be not much of a collaborative nature within the group which has many different subsections and subgroups focusing on their own priorities. In some instances, members have targeted each other to gain access to cryptocurrency wallets.
In the majority of cases, gang members tend to be either UK, or US citizens, but are happy taking work from whoever wishes to pay them. Those in the UK seem to be fans of throwing bricks through windows of victims, or setting fire to property, whilst in the US, the trend is drive-by shootings of houses, and “swatting” which is the act of calling the federal authorities with a made up story of child-abuse, or illegal weapons, etc. so that the authorities send in the swat teams to raid the victims house.
Extreme measures
One video circulating on various channels used by the Comm members shows a small bedroom, depicting the aftermath of a robbery: dry blood can be seen smeared across a Macbook Pro, a pair of pliers lay on an unmade bed, and more blood is speckled across the floor and walls.
In another chilling incident, a set of photos show a young man in his underwear, restrained with zip ties and an attacker holding a syringe of what was claimed to be heroin. The boy’s captors threatened to inject him with it unless he handed over his cryptocurrency wallet data.
These images have been collected by website Vice, and sanitised snippets have been posted on their YouTube channel highlighting the lengths these gang members will go to.
Patrick McGovern-Allen
In September 2022, Patrick McGovern-Allen, a New Jersey resident who was a member of The Comm with the online tag of “Tongue” was arrested on multiple counts.

Federal prosecutors explained that McGovern-Allen was very explicit in his activities as a member of the Comm.
“In the chats, [Tongue] tells other Discord users that he was the person who shot K.M.’s house and that he was willing to commit firebombings using Molotov Cocktails,” the complaint against McGovern-Allen explains. “For example, in one Discord chat from March 2022, [the defendant] states ‘if you need anything done for $ lmk [“let me know”]/I did a shooting/Molotov/but I can also do things for ur entertainment.”
McGovern-Allen had shared video proof that he and anothe Comm member had carried out attacks for money.
The first video posted showed two men tossing a Molotov Cocktail at the side of a residence in Abington Township, Pa, setting it ablaze. The second featured two men with handguns unloading multiple rounds into the first story of a house in West Chester, Pa. Fortunately in both cases, the occupants of the homes were unharmed in the attacks.
In October this year, Mc-Govern-Allen was sentenced for 13 years for his crimes.
A copy of McGovern-Allen’s sentencing statement says that he pleaded guilty to three criminal counts, including two for stalking, and one for the use of fire in commission of a federal felony. The judge in the case gave McGovern-Allen 160 months (13 years)in prison. After completing his sentence, McGovern-Allen will be on supervised release for three years.

Court papers specifically state McGovern-Allen’s membership of a online gang of SIM swappers who engage in various illegal acts for money.

SIM Swapping
SIM swapping is the act of tricking a mobile network operator to port a victims mobile data to a new SIM by pretending to be the victim.
In some cases of SIM swapping, the threat actors social engineer a mobile operators call centre staff to unwittingly send the port code, in other cases, gangs have threatened, coerced, or blackmailed staff to send the codes, and on some cases even managed to get their own gang members inside the mobile operator as staff members.
In the majority of cases, the SIM swap attack involves obtaining as much information about the victim as possible, and using this data to social engineer the call center in order to convince the call centre staff that they are the victim and that the have a new phone and need to transfer their number to it.
If the SIM swap is sucessfull, the gang will then be able to attack the victims various online accounts and as such intercept any MFA codes sent via SMS, or to security apps such as DUO.
Once the attackers have the security codes, they can fully compromise the accounts, or in the case of people like Octo Tempest, sell the access to the ALPHAV ransomware gang.