(24/10/23) Blog 297 – Identity & access experts Okta attacked with compromised identity
In one of the biggest cases of irony so far, Okta, one of the worlds leading providers of Identity and access management systems to millions of customers all across the world were breached with stolen identity token for its customer case management portal.
The latest incident is another example of a supply chain attack given that once Okta were breached, the threat actors had access to sensitive customer data, potentially giving the attackers data to breach other companies. A number of companies have already reported suspicious activity on their networks as a result of the Okta incident.
How it happened
Unusual activity was first identified by BeyondTrust – another Identity and access management company who detected and blocked an attempt to log-in to an in-house Okta admin account on October 2nd
It appears that the attackers used an identity token which had been stolen from Okta’s customer support system.
BeyondTrust notified Okta of the breach and provided thm with forensic data and analysis provingf that the token had originated from Oktas systems, but it was two week later that Okta publically announced the breach. A spokesperson for Beyond trust said that they were not notified of the fact that they were an affected customer until the 19th October.
On the 18th October, Internet giant CloudFlare also announced that they had identified malicious activity on their networks as a direct result of a compromised Okta token. A blog on the cloudflare website explains how they identified and contained the attack against their systems.
On the 20th October, David Bradbury – Oktas’ Chief Security Officer released an official statement about the incident.
How were the tokens obtained?
When an Okta customer has difficulty with their Okta system, as part of their correspondence with Okta support teams, they are requested to submit a HTTP Archive (HAR) file for the support team to analyse.
A HAR file is a data archival format used to analyse the data flow between web browsers and websites. All modern browsers have the ability to generate HAR files. THe generation of the har files will include sensitive data, including authentication tokens.
A threat actor somehow compromised the Okta support system and from their obtained copies of har files, extracted the authentication tokens, and used those to target other companies. At this time, it is unknown how the threat actor compromised Okta to gain access to the support systems, but it is being speculated that it was a social engineering attack which revealed an Okta staff members credentials
Damaging incidents
This is not the first time Okta has suffered a sever breach of its systems – back in December 2022, another breach saw a large amount of Oktas’ source code stolen following a breach of its GitHub repositories.
Another breach in January 2022 saw the Lapsu$ gang infiltrate the Okta network and post screenshots online of their access, which was gained after the compromise of a third-party organisation and the theft of VPN credentials which allowed access to Okta’s network.

Some of the screenshots posted by Lapsu$ of the Okta breach
This latest incident at Okta saw a large hit to the Okta share price as the financial markets reacted to the attack. The share price has fallen by 20% in the 4 days since the announcement of the breach, wiping almost $2B of the companies fortunes.
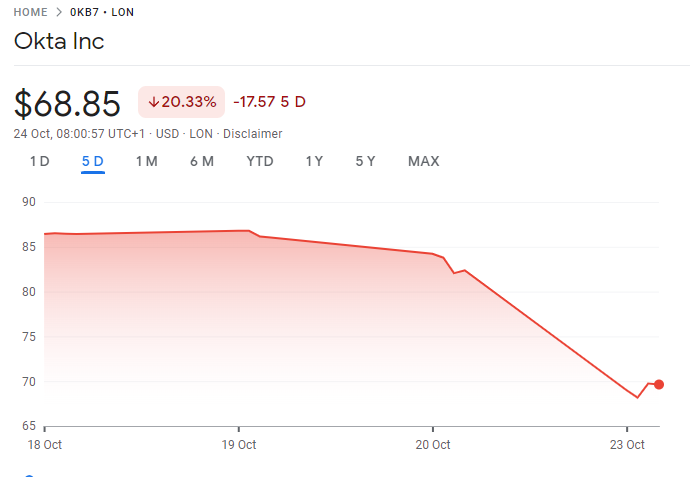
Okta share price performance













