(20/10/23) Blog 293 – WinRAR vulnerability used by state-backed threat actors
Google’s Threat Analysis Group (TAG) have released a statement this week showing that multiple government-backed threat actors are actively exploiting a vulnerability within the WinRAR archiving utility.

The vulnerability is being tracked as CVE-2023-38831 and causes WinRar to execute arbitrary code when a user double-clicks a benign file within an archive.
A blog post by researchers at Group-IB shows that the vulnerability has been used as a 0-day exploit since April of this year targeting financial traders to deliver malware. Just a few hours after the blog post from Group-IB was published, multiple Proof of Concept (PoC) examples were uploaded to GitHub repositories.
Since then, Google’s TAG have observed activity involving exploits related to the vulnerability being tested by threat actors known to be affiliated with government entities.
Attack campaigns
In April 2023, TAG reported on FROZENBARENTS (aka SANDWORM) targeting the energy sector and continuing their hack & leak operations.
Using a lure themed as an invitation to join the Ukrainian Drone Training School, the email sent by SANDWORM contained a link to an anonymous file-sharing service, which delivered a benign PDF document with a drone operator training curriculum and a malicious ZIP file exploiting CVE-2023-38831.
In September, CERT-UA identified FROZENLAKE (aka APT28), a group attributed to Russian GRU, using CVE-2023-38831 to deliver malware targeting energy infrastructure companies.
FROZENLAKE used a free hosting provider to serve CVE-2023-38831 to target users in Ukraine. The initial page redirected users to a mockbin site to perform browser checks and redirect to the next stage, which would ensure the visitor was coming from an IPv4 address in Ukraine and would prompt the user to download a file containing a CVE-2023-38831 exploit.
TAG has also observed government-backed groups linked to China exploit CVE-2023-38831. In late August, ISLANDDREAMS (aka APT40) launched a phishing campaign targeting Papua New Guinea.
How the vulnerability works
Consider the below rar archive file:
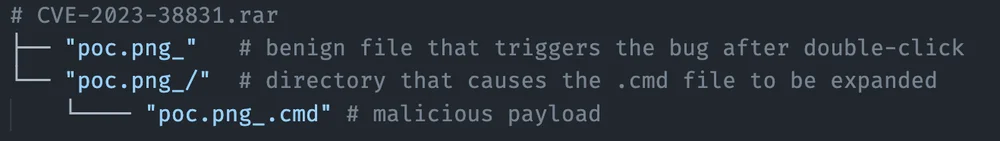
When a user clicks the poc.png_ file (note the underscore is not a part of the file name, here it is used to illustrate the presnece of a space), WinRAR will attempt to identify which files need to be decompressed by iterating through all the associated files in the archive.
Due to the way the file matching is made, if a directory is found with the same name as the selected file, both the selected file and the files inside a matched directory are extracted to the root of a random temporary directory.
In this example, poc.png_/ indicates a directory which contains poc.png_.cmd
When writing the contents of the files, WinRAR performs path normalisation that removes appended spaces, because Windows doesn’t allow files with trailing spaces.
Finally, WinRAR calls the ShellExecuteExW function, passing the non-normalised path with a trailing space “%TEMP%\{random_directory}\poc.png_” to run the user-selected file. Internally, ShellExecute attempts to identify file extensions by calling “shell32!PathFindExtension” which fails because extensions with spaces are considered invalid.
Instead of crashing, ShellExecute proceeds to call “shell32!ApplyDefaultExts” which iterates through all files in a directory, finding and executing the first file with an extension matching any of the hardcoded extensions: “.pif, .com, .exe, .bat, .lnk, .cmd”.
As such, the poc.png_.cmd file is executed even though this is not the file initially selected by the user.













