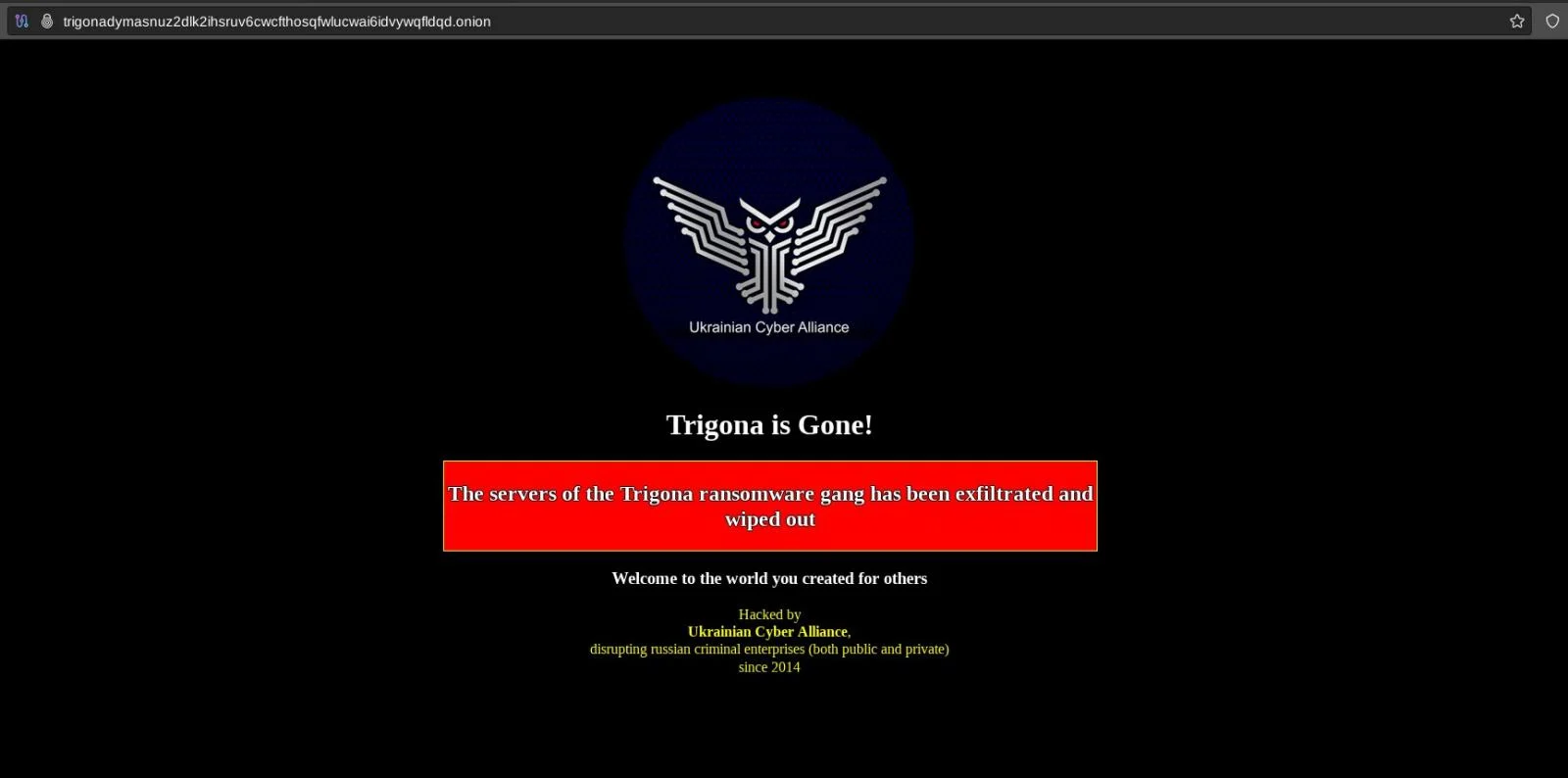
(19/10/23) Blog 292 – Trigona ransomware gang hacked by Ukrainian Cyber Alliance
A post uploaded yesterday by @vx_herm1t on X shows the current home page of Russian ransomware gang Trigona and that it has appears to have been completely wiped out by the Ukrainian Cyber Alliance.
Who are / were Trigona?
Trigona is the name of a malware which appeared initially in late 2022, although samples of the malware had been observed earlier in the year, suggesting the gang behind the attacks were developing their tools for a while before launching their attacks.
Analysis of the malware used by the gang by Trend Micro suggests that the Trigona malware was developed by the same threat actors who developed the CryLock ransomware. It has also been linked to the ALPHV / BlackCat group though any similarities between Trigona and BlackCat ransomware are only circumstantial at best (one possibility is that ALPHV collaborated with the threat actors deploying Trigona but were not actually involved with its development and operation).
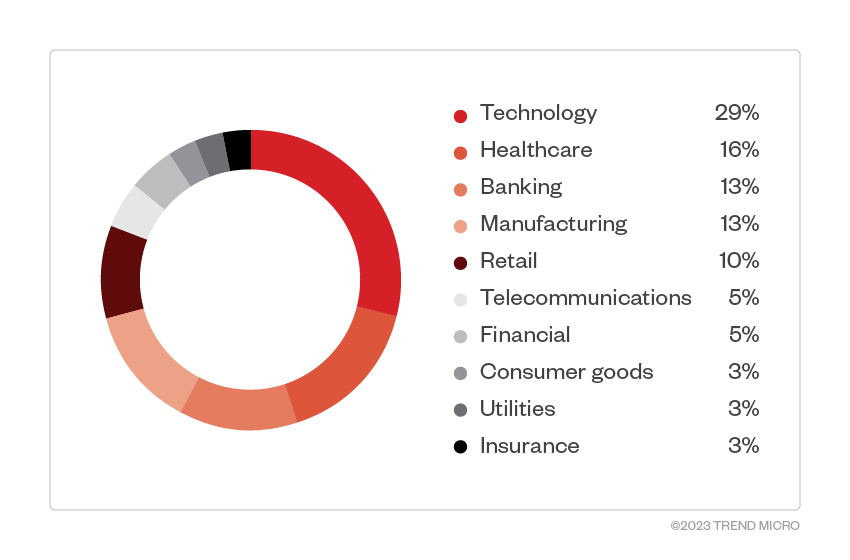
The US and India were the countries with the highest number of Trigona ransomware detections, with Israel, Turkey, Brazil, and Italy also having a significant count.
Attacks focused mainly on the technology and healthcare industries, which had the highest number of detections.
Who are the Ukrainian Cyber Alliance?
The Ukrainian Cyber Alliance (UCA) is a community of Ukrainian cyber activists from various cities in Ukraine and around the world.
Formed in the spring of 2016 from the merger of two other cyber activist groups, FalconsFlame and Trinity, the group was later joined by the another group (RUH8) and individual cyber activists from the CyberHunta group.
The hacktivists united to counter Russian aggression in Ukraine under the ruling of with Art. 17 of the Constitution of Ukraine to defend the independence of their country and its territorial integrity, as is the duty of every citizen.
Since their formation, the UCA have had multiple successes against Russian targets:
- 2016
- OpDonbasLeaks saw over 100 attacks against websites and email accounts of militants, propagandists, and others operating in occupied territories.
- The Abkhazian Network News Agency (ANNA News) – A Pro-Kremlin news agency was hacked and taken offline for 5 days
- OpMay9 saw nine websites of the Donetsk People’s Republic terrorists, propagandists, and Russian private military companies were hacked
- OpMay18 saw the gang target the website of Sergey Aksyonov – the chairman of the council of ministers of the Republic of Crimea, and put his voice into a fake message
- OpDay28 targeted 17 resources of Russian terrorist organisations
- Sometime in July, the group hacked the document management server of the Department of the Ministry of Defense of the Russian Federation, and made public defense contracts executed during 2015.
- Op256thDay saw more than 30 sites of Russian foreign aggression destroyed
- 2017
- In February and March 2017, the UCA exposed the correspondence of Belarus citizen Alexander Usovsky, a publicist whose articles were often published on the website of Ukrainian Choice, an anti-Ukrainian NGO backed by oligarch Viktor Medvedchuk. Analysts conducted a study of the emails and published two articles on how the Kremlin financed anti-Ukrainian actions in Poland and other Eastern European countries. The published materials caused outrage in Poland, the Czech Republic and Ukraine.
- An attack of the CIS Institute by the group revealed that the NGO is financed by the Russian state company Gazprom who allocated $2 million annually to finance the anti-Ukrainian activities of the CIS Institute
- The hacking of the Russian Foundation for Public Diplomacy provided insight to the forms of Russia’s foreign policy strategy. On the eve of the war, funding for a six-month propaganda plan in Ukraine reached a quarter of a million dollars. Under the guise of humanitarian projects, subversive activities were carried out in Ukraine, Serbia, Bosnia and Herzegovina, Bulgaria, Moldova, and the Baltic States.
Trigona takedown
Information provided to BleepingComputer outlines how the attack against Trigona unfolded.
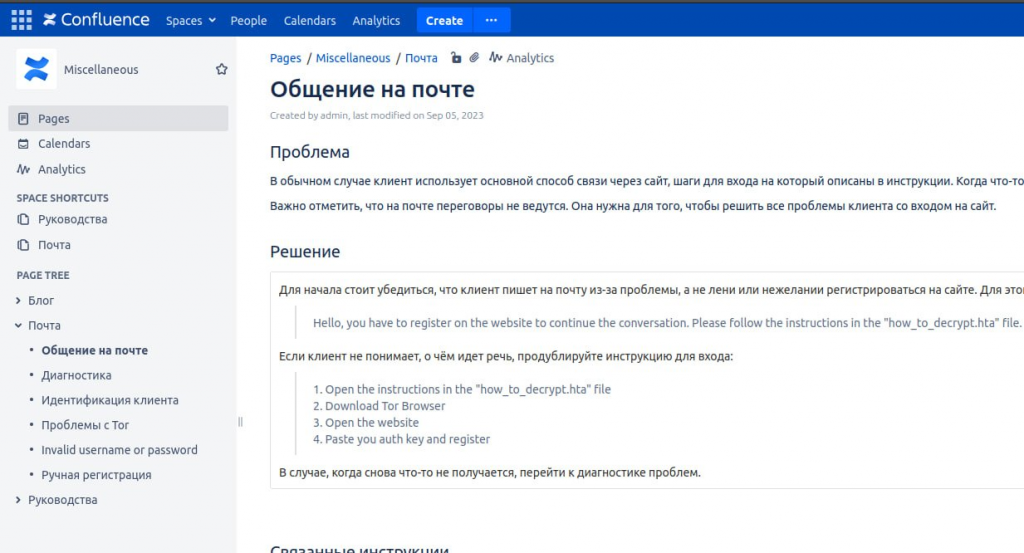
Members of the UCA gained access to Trigona ransomware’s infrastructure a week ago by using a public exploit for CVE-2023-22515, which is a critical vulnerability in Confluence Data Center and Server that can be leveraged remotely to escalate privileges.
@vx_herm1t published screenshots on the 12th October showing that they had access to the confluence server of the Trigona gang
Trigona swiftly changed their passwords for the service and shut down their public-facing infrastructure, but the UCA were already inside the network with persistence and backdoor mechanisms and over the forthcoming week exfiltrated all the information from the ransomware gangs servers, including the threat actor’s administration and victim panels, their blog and data leak site, and internal tools (Rocket.Chat, Jira, and Confluence servers).
The UCE also exfiltrated the developer environment, cryptocurrency hot wallets as well as the source code and database records. At this time it is unknown if the developer data and source code contains any decryption keys for any of the gangs victims, but UCA have said that if they do find any, they will immediately release them.
TH UCA also state that they were able to exfiltrate three backups from the gang with hundreds of Gb of stolen data from victims.
After harvesting all available data from the ransomware gang, the UCA activists deleted and defaced their sites, also sharing the key for the administration panel site.