(15/10/23) Blog 288 – Encryption – a short guide (pt2)
In the previous post, I identified a few common terms used in encryption, and then identified some early examples of ancient encryption .
In those early methods of securing data, we see three more fundamental encryption terms being used. Transposition, Substitution, and the use of a key.
Lets take a look at why those things are important in encryption.
Transposition (A.K.A. Permutation) is the name given to the process of scrambling the plain-text data by altering the position of characters. The Scytale used a rudimentary form of transposition – by scribing the characters of the message along the baton, when the parchment is unwound, the position of each character is altered. The permutation value being constrained by the diameter of the baton.
Another example of transposition in use is with the use of a rail-fence cipher.

The rail-fence cipher (named after the rails and spikes used in a typical fence ) uses a grid whereby the letters of the message are written in a downward-diagonal along each rail. When reaching the bottom rail, the message is continued in an upwards-diagonal. Thus the message zig-zags up and down the rails.
Once completed, the encoded message is then output by reading along the rails from left to right, thus transposing the positions of the characters in the original message. Decrypting the message can only be done correctly if the recipient knows how many rails to use.
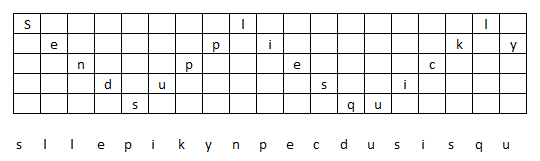
In modern cryptography, Transposition is often used in the form of a P-Box (Permutation box) as part of the process of altering data before, during, or after the encryption process as a way of adding more variance to the enciphered data.
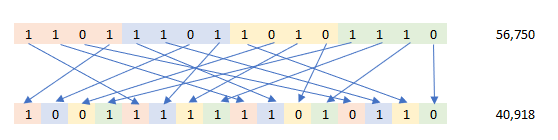
In the image below, the value 56,750 is shown in binary. The p-box is operating on 4-bits at a time moving each bit position 4 positions. The resulting output is a value of 40,918
Substitution is the swapping of data for another data, often following a pre-determined sequence. In the Data Encryption Standard (DES) encryption cipher, an S-Box is used to alter input data to a different output data.
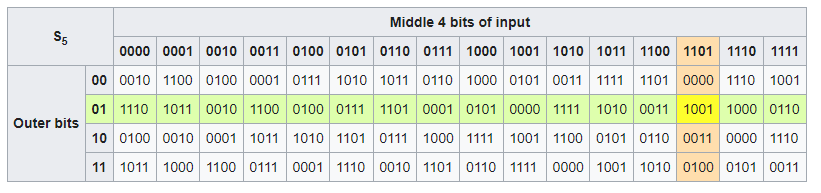
In this example, we have 4 rows of possible 0 and 1 combinations (00,01,10,11) and 16 columns of bits ranging from 0000 to 1111.
The grid is then composed of a set of pre-determined values
The s-box is then used as a lookup reference for each set of 6 bits to be manipulated
So, for example, if the 1stsix bits of our data are 011011, we take the 1st and 6th bit (0 & 1) which tells us to use the 2nd row of the S-box. We then locate the remaining bits (1101) along the columns. The output is the value where the column and row intersects – In this case 1001.
In many cases, P-boxes and S-boxes are used consecutively as a way of jumbling up data before encrypting it.
The key to it all
Encryption relies on the use of a key which alters how the algorithm operates on the input data. The key is of utmost importance to any cipher system and must be protected at all costs. If the key is known, then the cipher system is compromised.
Taking the Caesar cipher as the basic example, we know that the process (algorithm) is to move each character by a number of positions. The key is how many positions we are moving the characters 3?, 5?, 12?
In the scytale example, the key is the diameter of the baton – to small or too large and the characters on the parchment will not align correctly
In the late 19th Century, Dutch linguist and mathematician Auguste Kerckhoffs published a paper entitled La Cryptographie Militaire in Le Journal des Sciences Militaires in which he outlined a number of principles for practical cipher design.
The principles were as follows:
- The system should be, if not theoretically unbreakable, unbreakable in practice.
- The design of a system should not require secrecy, and compromise of the system should not inconvenience the correspondents.
- The key should be memorable without notes and should be easily changeable.
- The cryptograms should be transmittable by telegraph.
- The apparatus or documents should be portable and operable by a single person.
- The system should be easy, neither requiring knowledge of a long list of rules nor involving mental strain
The 2nd principle became known as Kerckhoffs’s principle in that it does not matter if another person knows the function of a cryptographic system, so long as the compromise of the key is not achieved.
Kerckhoffs’s principle was reformed by Claude Shannon, a late 20th century mathematician in a document where he said we should assume the “enemy knows the system” – This term is known as Shannon’s Maxim.
All the example I have shown so far utilise simple processes to encipher the plain-text. The use of transposition and substitution start to make things a little more difficult to would-be decryptors, and the use of a secret key makes it even harder.
In the next post I take a look at entropy – where start to add a high number of possibilities to the equation.













