(14/10/23) Blog 287 – Encryption – a short guide (pt1)
We all know encryption is the no.1 tool used to keep data private – we hear it mentioned everywhere, but to many it’s just some magical thing involving hard maths that just works right? Well that’s mostly true, but it can be explained in some simple terms
In this mini-series of posts, I will explore the evolution of encryption and how it is utilised in the modern world to keep our data and systems secure.
Some terminology
Before I get into the weeds of encryption, we need to understand the meaning of a few common encryption-related terms:
Encryption / Decryption – The process of changing data from one form to another
Plain-text – The data to be encrypted / the message after decryption
Cipher-text – The data after encryption / before decryption
Algorithm – In the context of encryption, the algorithm is the sequence of events which changes the plain-text to the cipher-text / cipher-text to plain-text
Key – A value which is used in conjunction with the algorithm which alters the behaviour of the algorithm
Hash function – An algorithm which maps data of arbitrary length to that of a fixed-length (see hash digest)
Hash digest – The output of a hash function
Avalanche effect – A desirable property of a hash function where a small change to input data results in a huge change in output data
Hash collision – A non-desirable feature of a hash function where two dissimilar pieces of input data produce the same hash digest
History of encryption
There has been a need to keep information secret for millennia – some of the earliest known examples of such practices go back to Egyptian times. One of the earliest forms of encryption is that of symbol replacement, which was first found in the tomb of Khnumhotep II, who lived in 1900 BCE.

Another ancient example of encryption is found in the Kama-sutra, which was written in the 4th century CE by the Brahmin scholar Vatsyayana, but is based on manuscripts dating back to the 4th century BCE.
The writing in the Kama-sutra recommend that women should study 64 arts, including cooking, dressing, massage, the preparation of perfumes, conjuring, chess, bookbinding and carpentry.
Number 45 on the list is mlecchita-vikalpa (the art of secret writing), advocated in order to help women conceal the details of their liaisons.
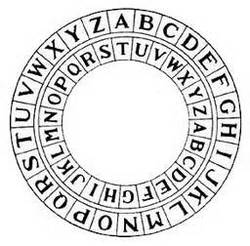
Probably the most well-known of these ancient forms of enciphering messages is the Caesar cipher.
Named after Julius Caesar, who lived 100 BCE, the principle of the Caesar cipher is that each of the letters in the plain-text message are moved a number of positions in the alphabet. This cipher system is sometimes called a Rot cipher (Rotation cipher) due to the fact it is often easy to replicate by using 2 rings with the characters of the alphabet on each ring. To encode you rotate one ring clockwise n-places, to decrypt you move the ring anti-clockwise n-places.
Another ancient form of ancient encryption is the Scytale. This was a device used in ancient Greece and involved the use of a tapered wooden baton (The scytale) and a parchment strap.
The sender of a message wrapped the parchment around the scytale and then scribed their message along the length of the scytale. Once the parchment was unwound from the scytale, the letters of the message would be jumbled, and the only was to recreate the message would be for the recipient to have a scytale of the same diameter.

Stonemasons used their chisels to create a form of symbol encryption known as pigpen. With this method, the cold chisels were used to carve lines and dots is specific forms to represent letters of the alphabet.
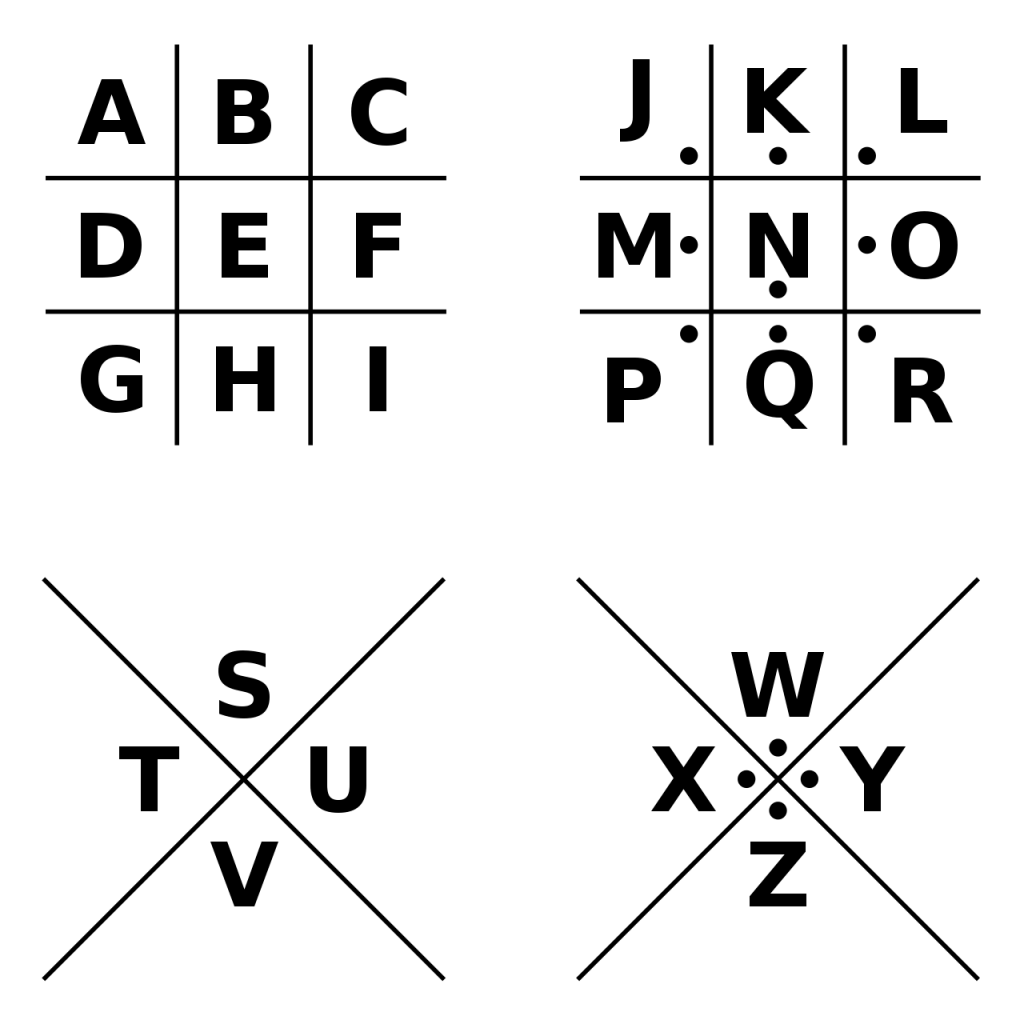
By carving the lines which represent each letter, secret messages could be carved into the brickwork by the mason.
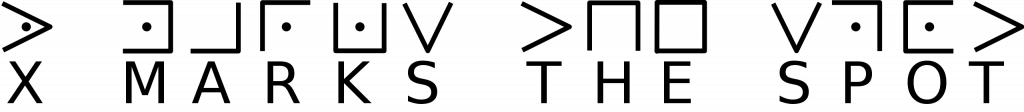
Not every stonemason used the same symbols, so reading a message is only possible if you know how the mason designed their pigpen mappings.
The image below shows a gravestone with a pigpen message carved around the top. In this case, the message is deciphered with the pigpen mapping shown underneath the image to read “remember death”


In the next post I will start to cover some of the principles of encryption which are used in more complex forms of encryption to those shown here.













