(13/10/23) Blog 286 – Supply chain attacks – what are they? and why do they matter?
SolarWinds, MoveIT, NotPetya, CCleaner, Equifax, Target.
All the above names have one thing in common – at some point, all of these have been involved in large supply chain attacks which have affected in some cases, millions of unwitting victims.
What is a supply chain attack?
Companies rarely operate as isolated entities – they have a supply chain of materials, software, data, and more from multiple third parties. In many cases, the product from one company doesn’t go straight to the end user, it goes to another company for inclusion in their product to be output as a product from that company, and so on.
A supply chain attack is a type of attack which targets an organisation through vulnerabilities in this complex supply chain.
A vulnerability in a third-party vendor makes it is possible for attackers to gain access to the supply chain and affect the onward flow of products, potentially affecting many thousands of down-stream victims.
Because third-party organisations require access to sensitive data to integrate with the internal systems of others (suppliers and customers). When a vendor is compromised, this shared pool of data is breached.
How do supply chain attacks happen?
Supply chain attacks can occur via multiple attack vectors, but once inside a vendor’s network, the attackers need to find a way to hide their malicious code so that it goes unnoticed by others.
One highly effective mechanism is to employ the use of trust. By leveraging the trust of one internal system with another, attackers can move their malware freely around the vendor, and then on to others.
In the world of I.T., trust often comes in the form of digital signatures – cryptographic values that can only come from a trusted, known source. Code is typically signed by an issuing entity with a digital signature which others then use to validate and verify the legitimacy (and thus, trustworthiness) of the code.
By hiding behind a digital signature, malicious code is free to infect the steady stream of software update traffic between a compromised vendor and its client network.
SolarWInds
This is the case with the fairly recent SolarWinds Orion supply chain attack.
The SolarWinds Orion Platform is a powerful, scalable infrastructure monitoring and management platform designed to simplify IT administration for on-premises, hybrid, and software as a service (SaaS) environments.
Towards the latter end of 2019, a team of suspected Nation-state hackers (Tracked as Nobelium by Microsoft, this team is linked to the Russian state) infiltrated the SolarWinds network. Aproximately one month after the initial breach, the gang uploaded a test malware to the Orion software tool to gauge reactions of any victims.
In the following year, a more nefarious malware (codenamed Sunburst) was injected into Orion and was digitally signed, thus giving the malware an air of trust.
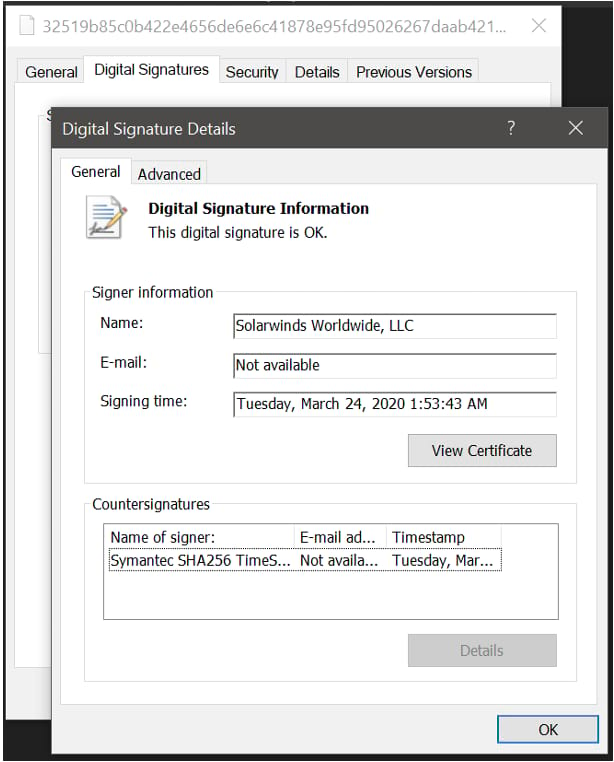
In the March of 2020, SolarWinds started pushing out software updates to their customer base which included this added malware.
More than 18,000 SolarWinds customers installed the malicious updates, and through this code, the attackers accessed the networks and data of many of the affected companies. Many of the affected organisations were US Government entities, including The Office of the President of the United States, The Secret Service, The Department of Defence, The NSA, and all branches of the US military.
MoveIT
MOVEit is the name of a highly popular file transfer software application which is used by over 1700 organisations worldwide.
On May 31st, a critical zero-day vulnerability was discovered in the MOVEit Transfer web application. The vulnerability was a SQL injection vulnerability, which allowed threat actors the ability to extract data from the victim’s database, execute their own SQL queries, and manipulate or delete data.
It is now known that the vulnerability was widely exploited in the wild prior to its official disclosure and the subsequent patch that was made available.
The Cl0p ransomware group were not the only attacker who made use of the MOVEit vulnerability, but they are by far the most successful with its effects.
One of the notable victims of the MOVEit vulnerability was Zellis, a UK-based provider of payroll and HR solutions. Utilising the vulnerability, the Cl0p ransomware group launched an attack on Zellis, and gained unauthorised access to sensitive information belonging to Zellis and its clients.
It is known that over 1,000 companies were affected by the Cl0p attack on MOVEit, which had the cumulative effect of impacting over 60,000,000 individuals, makinmg it one of the worlds biggest supply chain attacks.
Why do they matter?
As evidenced in the two attacks highlighted above, supply chain attacks have the potential to impact on millions of down-stream customers. Due to the levels of trust employed between organisations and their suppliers and customers, supply chain attacks can be very wide in reach, very stealthy, and have long-lasting ramifications.
The ever evolving digital world offers a multitude of vectors for attackers to infiltrate even the biggest of companies via smaller ones elsewhere in the chain.
NCSC advice for managing supply chain issues
Yesterday (12th Oct) saw the latest update to the continuously growing list of guidance offered by the UK’s NCSC.
The eight-page guidance highlights the issues of supply chain attacks, and offers a set of guidance documents for organisations to use to help understand supply chain issues and how to mitigate the risks.
Split into three topic areas, Foundations covers the 12 principles of Supply Chain Security, Application looks at applying the 12 principles, and Consolidation shows how to build a supply chain map to help manage supply chain risks.













