(04/10/23) Blog 277 – LockBit exfil infrastructure exposed
Researchers at securityaffairs have released an fascinating insight in to the global infrastructure used by LockBit during their ransomware attacks.
The blog post : “LIGHTING THE EXFILTRATION INFRASTRUCTURE OF A LOCKBIT AFFILIATE (AND MORE)” gives a detailed look at how one common string of characters led the researchers on a trail all across the globe.
FTP/TLS tunnel
After a long time tracking the LockBit gang, the researchers eventually found an attack where the threat actor exfiltrated some victim data via a TLS encrypted FTP connection.
The process was achieved by exploiting the FileZilla FTP client and used the tunneling services offered by Ngrock Application Programming Interface (API).
Analysis of the connections made during this attack led the researchers to identify a server located in Moscow which was being administered by a Chinese hosting provider called Chang Way Technologies.
A scan of the ports and services open to the Internet identified an accessible Remote Desktop Protocol (RDP) port which when probed further identified the underlying operating system and the hostname of the device.
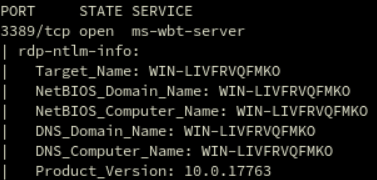
The researchers very quickly identified that they had seen the string of characters in the hostname before – many times in fact.
For background info: When installing the Windows operating system, unless specified by the user, Windows generates a random string for the hostname, so that it is (hopefully) unique on the users network. This format is always WIN:XXXXXXXXXXXX where the X’s correspond to the random string generated.
Users can change this string at any time to something meaningful to them, but typically when they do, they change the entire string to a word or phrase such as “main-PC” or “John’s-Laptop”, etc.
In this case, the choice of characters used which researchers had seen before was very interesting.
Multiple past LockBit victims show this exact hostname within their dedicated page on the gang’s dark web leak site. The chance of multiple LockBit affiliates randomly chosing the same hostname is almost zero, so this correlation enabled the researchers all to spot the connection between this particular affiliate and their victims.
Deeper investigation of WIN-LIVFRVQFMKO
The researchers targeted the network they had connected to and identified a total of 105 hosts all with the same hostname serving an IIS FTP service. IIS is the Internet webserver available in all versions of Microsoft Windows.
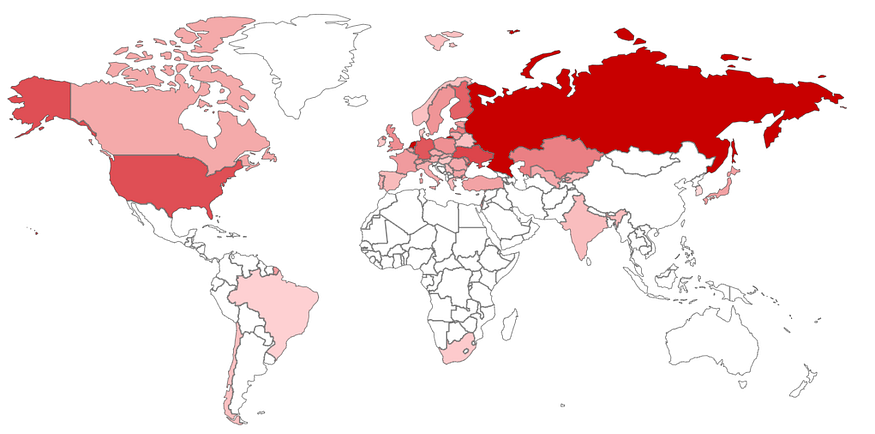
The researchers identified that these servers have been deployed in 16 countries across the world. The servers were identified as being in Russia, Netherlands, Finland, United States, Kazakhstan, Turkey, Ukraine, Czech Republic, Latvia, Norway, Poland, Romania, Uzbekistan, Germany, France, and Greece.
Collating other research
Focusing their attention on the identified hostname, the researchers found that many other researchers had reported the same string, but until now no-one had made the connection.
- In September 2019, Cybereason found the hostname in old LockBit 2.0 extortion activity, linking the “WIN-LIVFRVQFMKO” hostname to another exfiltration endpoint handled by the same provider, Chang Way Technologies Co. Limited.
- In 2021, the hostname appeared in SMTP messages reported as a “romance scam” in a popular romance and dating scam tracking forum.
- In March 2022, the hostname appeared in the Conti Leak chat in a particular conversation dated back to October 2021 where Bentley (one of the group system admins), was switching a piece of their Tor infrastructure from onion v2 domains to onion v3. In this context, a user named “bloodrush” leaked the hostname by copy-pasting a chat line written by Bentley, and accidentally leaking the hostname.
- Indicators shared by the NetmanageIT Threat Intelligence team, about a June 2023 Ursnif campaign targeting Italy report many remote destinations hosting Ursnif tier 1 command and controls sharing the same hostname.
- On August 2023, the security researcher 0xToxin documented an infection chain leveraging AutoIT scripts to deliver the DarkGate malware, a particular stealer supporting also HVNC and HAnyDesk, and the C2 he decoded was using the same hostname too.
Cloned base image
The researchers concluded that the reason for seeing the same hostname multiple times must be that the affiliate behind the system had built one base image with a default set of configuration variables and tools and simply re-deployed that image multiple times to build their network of endpoints.
This approach is not an unusual one – most commercial entities do exactly the same – by building a “known-good” image, the company can quickly deploy multiple instances of a known configuration across their IT estate, and then configure a small set of devices for specific departments, or users.
Eight-thousand strong army
With a good degree of confidence, the researchers conclude that there are multiple instances generated from the same base image, likely linked to a single organisation. The extension of this linked infrastructure involves more than 8 thousand hosts worldwide, and at least a third of which is located in CIS countries – Commonwealth of Independent States

As a final piece in their report, the securityaffairs researchers say:
All these pieces draw a very unsettling picture. In fact, since 2019, the hostname has linked a wide range of eCrime activities such as ransomware and data extortions, info-stealing malware spreading, botnet infections, and scams. Basically, seems we are observing a piece of infrastructure linked to a very well-organized criminal gang operating in the full depth of the eCrime ecosystem: stealing initial access credentials, deploying banking bots and ransomware precursors, conducting digital extortions, and laundering money through unaware individuals. And, to make it worse, this hostname seems also related to an ex-Conti sysadmin, dreading a link with the Wizard Spider criminal group.













