(03/10/23) Blog 276 – BunnyLoader – new malware spreading faster than rabbits
Security researchers at Zscaler have discovered a new malware-as-a-service (MaaS) named ‘BunnyLoader’ being advertised on multiple dark web forums as a file-less loader that can perform multiple tasks including data stealing, keystroke sniffing, and replacing the contents of a victims system clipboard.

Rapid development
The researchers said in their report that the malware appears to be under rapid development, with frequent updates adding new features and bug fixes.
The first version of BunnyLoader was seen on September 4th and since then, its developers have pushed out 9 minor updates and 1 major update which have added more capabilities such as various anti-detection mechanisms and extra data harvesting capabilities. The major revision update was released just 3 weeks after the initial release.
The BunnyLoader development timeline:
- v1.0 (Sept 4): Initial release.
- v1.1 (Sept 5): Fixed client bug, introduced log compression before upload, and added ‘pwd’ command for reverse shell.
- v1.2 (Sept 6): Enhanced stealer with browser history recovery, NGRok auth-token recovery, and supported additional Chromium browser paths.
- v1.3 (Sept 9): Added credit card recovery for 16 card types and fixed C2 bugs.
- v1.4 (Sept 10): Implemented AV evasion.
- v1.5 (Sept 11): Introduced VPN recovery to stealer, fileless loader bug fixes, and log loading optimizations.
- v1.6 (Sept 12): Added downloads history viewer and anti-sandbox techniques.
- v1.7 (Sept 15): Enhanced AV evasion.
- v1.8 (Sept 15): Implemented keylogger functionality and resolved various bugs.
- v1.9 (Sept 17): Enhanced stealer with game recovery, more Chromium browser paths, and added a desktop wallet recovery.
- v2.0 (Sept 27): Updated C2 GUI, fixed critical vulnerabilities, including SQL injection and XSS, introduced exploit attempt detection, and further optimized stealer and fileless loader functionalities
Capabilities
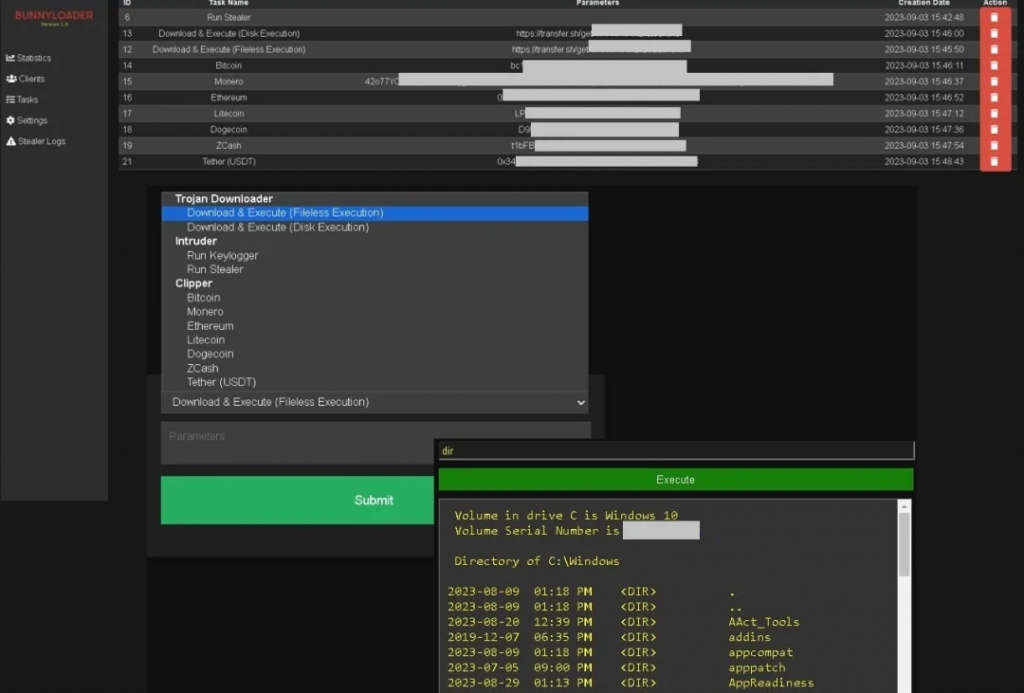
Bunny loader appears to have numerous capabilities as shown in the above release updates, but analysis of screenshots show other capabilities as well.
Zscaler show that BunnyLoader has the following capabiltiies
- Downloading and executing additional malware
- Keylogging
- System credential theft
- VPN credential theft
- Messaging application credentials theft
- Browser AutoFill data theft
- Manipulating a victim’s clipboard to steal data including cryptocurrency wallet info
- Running remote commands on the infected machine
- Anti-malware detection processes
- Sandbox awareness
- Docker container awareness
- Virtual Machine awareness
The malware is being sold on dark web forums by a user called PLAYER_BUNNY for the fairly low price of $250 for a lifetime subscription.
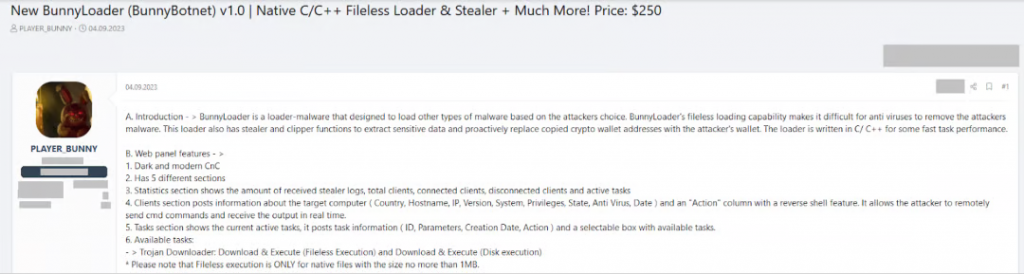
For those who require the tool to have a bit more capability, there is a private stub version on offer which features stronger anti-analysis capabilities, in-memory injection, AV evasion, and additional persistence mechanisms – this is selling for $350.













