(02/10/23) Blog 275 – Operation DreamJob targets victims via LinkedIn
North Korean hacking group – Lasarus are currently running a targeted campaign against people in specific industry sectors via an elaborate social engineering campaign dubbed Operation DreamJob.
As the name suggests, the operation begins with identifying people who are seeking new employment via social media platforms such as LinkedIn and Facebook.
Victim selection
The Lasarus gang are scouring social media platforms looking for people in specific industries who appear to be open to new job opportunities and are then contacting them with the goal of convincing them to download documents with details of exciting opportunities.
Unfortunately, the files are compromised with malicious content, which when opened, install malware allowing the gang to infiltrate the device, and ultimately the network of the victim.
A recent attack using this approach was conducted against an Aerospace company in Spain.
The victim was approached on LinkedIn by one of the Lasarus gang who pretended to be a recruiter from Meta named Steve Dawson.
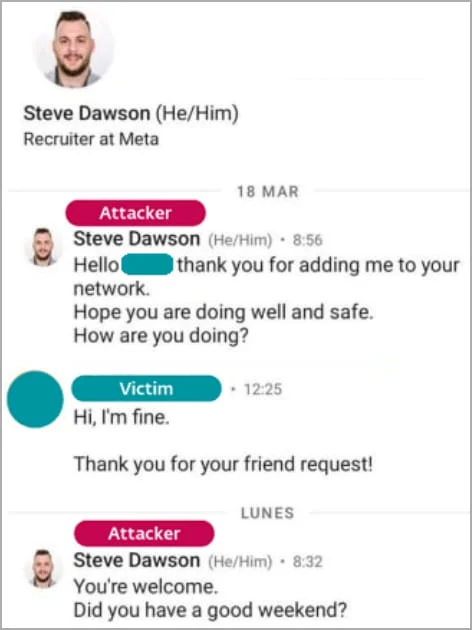
The attacker started a seemingly innocuous conversation with the victim which eventually progressed to asking the victim how proficient they were in C++ programming.
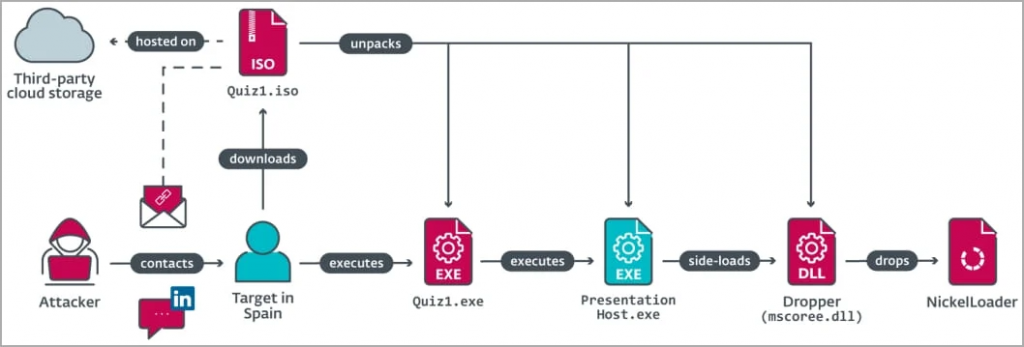
The attacker asked to victim to download some quizzes which were in the form of executables within ISO files.
When the malicious files were executed, an additional payload from the ISO file was silently installed onto the victim’s machine via DLL side-loading attack (mscoree.dll) using a legitimate program called PresentationHost.exe
The malicious payload is the NickelLoader malware loader which installs two backdoors, a variant of BlindingCan with toned-down functionality (miniBlindingCan) and a malware calledLightless Can.
The commands supported by miniBlindingCan are:
- Send system details (computer name, Windows version, code page).
- Update communication interval (value from C2 server).
- Stop command execution.
- Send 9,392-byte configuration to C2 server.
- Update encrypted 9,392-byte configuration on file system.
- Wait for the next command.
- Update communication interval (from configuration).
- Download & decrypt files from C2 server.
- Execute the provided shellcode.
The commands supported by LightlessCan include:
- Mimic the
ipconfigcommand from the Windows command prompt - Mimic the
netcommand from the Windows prompt - Mimic the
netsh advfirewallfirewall command from the Windows prompt - Mimic the
netstatcommand from the Windows prompt - Mimic the
ping -6command from the Windows prompt - Mimic the
regcommand from the Windows prompt - Mimic the
sccommand from the Windows prompt - Mimic the
pingcommand from the Windows prompt - Mimic the
tasklistcommand from the Windows prompt - Mimic the
wmic process call createcommand from the Windows prompt - Mimic the
nslookupcommand from the Windows Server prompt - Mimic the
schtaskscommand from the Windows prompt - Mimic the
systeminfocommand from the Windows prompt - Mimic the
arpcommand from the Windows prompt - Mimic the
mkdircommand from the Windows prompt
Same malware – different approach
One of the first attacks using this malware came in March of this year when a digitally signed and trojanised version of the 3CX Voice Over Internet Protocol (VOIP) desktop client was used to target the company’s customers in a supply chain attack.
Victims were attacked when they downloaded an update to the companies softphone app
Customers who use 3CX include American Express, Coca-Cola, McDonald’s, BMW, Honda, Air France, Toyota, Mercedes-Benz, IKEA, and the National Health Service.
The threat actors behind the attack targeted both Windows and macOS via the compromised 3CX softphone app.













