(25/09/23) Blog 268 – Phishing, SMShing, Vishing, now Quishing
Most people are aware of the various tactics employed by many cyber criminals that attempt to get a victim to divulge sensitive data – Phishing, SMSishing, and Vishing. Well there’s a new approach that is gaining popularity – Quishing – the use of QR-Codes to attack a would-be victim.
Before I get to Quishing, and why its becoming popular – For those who unfamiliar with the other types of attacks – here’s a quick run-through.
Phishing (Spear phishing & Whaling)
Phishing, and its sub-categories (Spear-phishing & Whaling) is the use of emails with enticing messages, designed to get a victim to respond by either replying with data, clicking a link to a fake site, or opening an attachment.
Think of phishing as a bit like trawler fishing in that the one who sends the email (like casting a trawl-net) doesn’t know who or what will get snared. They send the emails out and hope they get a nice haul as a response.
Spear phishing is named after spear fishing, in that the phisher (fisher) knows exactly what their target is and takes a precise aim to get their prey. In a spear phishing attack, the threat actor crafts a carefully worded message that they hope will convince the victim that it is legitimate, and thus they fall for the attack.
When spear phishing, a predator will try to go for the largest of the available prey, so with whaling, a phisher goes for the biggest phish (whale) of an organisation – the CEO, the CTO, the CFO, etc. As they will often have the juiciest data to steal, or accounts to compromise.
SMSishing
SMSishing is the use of SMS messages to send links, etc in the same way that Phishing does. Often, SMSishing attacks try to entice a user to click a link to a malicious website, or to download a malicious app.
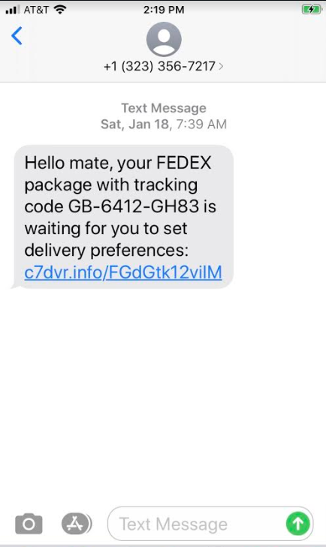
Occasionally a SMSishing attack might include a (fake) phone number for you to call which puts you straight through to a gang member who will then try to convince you to divulge sensitive details, or ask you to provide verification data, such as a legitimate One-Time-Code that allows the gang to instantly access your accounts.
Another attack type linked to SMSishing is the tactic of using social media apps to send messages. Attackers will use Facebook messenger, WhatsApp, Instagram, and other such sites to try to trick victims into clicking links, sending sensitive data, or engage in other forms of scam.
In these types of attack, often the attacker will initiate the attack through a social messaging app, but once the victim responds, they will try to get them “off-platform”, such as direct SMS messaging, or email so that the victim cannot use any security features of the social messaging platform to try to protect themselves.
Vishing
Vishing – or voice phishing – is where criminals attempt to trick victims into giving up sensitive information over the phone.
Modern vishing attacks often make use of automated voice simulation technology and will use personal information gained from other cyber attacks (data breaches) to put victims at ease and create an air of legitamacy.
Vishers typically pose as a trusted source (bank, credit card company, HMRC or a service provider) to trick people into handing over sensitive data. Typically, they’ll make the conversation sound urgent in order to panic their victims into acting without thinking first, such as suspicious activity on an account, or an over-payment that they need to refund, for example.
So how does Quishing work?
Quishing leverages the fact that you can put almost any type of data into a QR code – Images, videos, links to websites, app downloads, etc. but more so that a lot of current security software doesn’t have the facility so check the legitimacy of a QR code, so they act as a great way to bypass email filters, etc.
Often, an attacker will take the link which sits behind the QR code and use a URL shortening service such as bitly, TinyURL as an extra layer of obfuscation.

The other reason why Quishing is becoming popular is that when a victim receives one in an email, they have to use their phone to scan it – thus taking the victim out of the safety of their corporate network.
A number of recent attacks have taken place which use this new approach to targeting a victim organisation.
In May this year, a large US energy company was on the receiving end of over 1,000 emails which attempted to compromise staff credentials for their Office 365 accounts.
The staff at the company were sent fake Office 365 MFA (Multi-Factor Authentication) messages with embedded QR codes. The codes, when scanned allowed attackers to gain access to the users accounts
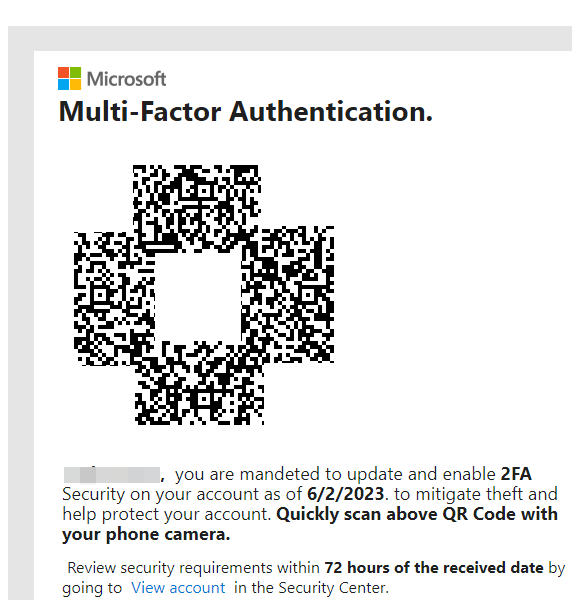
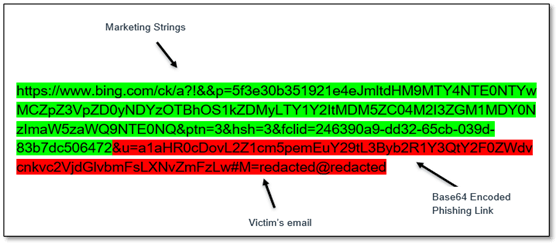
MS Bing redirect
Some email security tools can read QR codes and as such block any which are deemed to be malicious, so in their never-ending approach to snare victims, attackers have found another way to ensure that a company doesn’t filter out the malicious QR code.
Microsoft have an option within a users Bing account that allows for the creation of marketing URLs that includes a payload of the marketeers choice.
By generating a Bing Redirect URL, a company can send a legitimate looking URL which is tied to the bing.com domain, that then has a redirect component which takes the user to a second domain.
Attackers are leveraging this to hide URLs inside QR codes which, if scanned appear to originate from trusted domains (bing.com) but then re-direct to a malicious domain. To further their chances of getting through to an inbox, attackers will encode (typically base64) the malicious part of the redirect.