(15/09/23) Blog 258 – ‘Scattered Spider’ suspected as MGM attackers
A relatively new gang of cyber criminals is the prime suspect behind the recent attack against MGM International which saw the hotel and casino chain take many systems offline earlier this week in an attempt to stop the spread of the attackers malware.
Who are Scattered Spider?
Scattered Spider first appeared around May 2022 and have so far shown a strong capability in Social engineering and Phishing to obtain credentials which allows them to gain initial access to victim networks.

The gang is tracked as Scattered Spider, Storm-0875, Roasted 0cktapus, Scatter Swine and UNC3944 by various cyber security organisations. Due to their past exploits which have been predominantly financial in nature, they should receive a designation from Microsoft which falls into their new taxonomy framework as <something>-Tempest, as it stands, due to their short life of activity, they are currently classed as Storm-0875.
Storm-0875 has been reported by Microsoft as using the Blackcat/AlphaV ransomware, so has been rumoured for a while that Scattered Spider are an Affiliate for the ALPHAV ransomware gang.
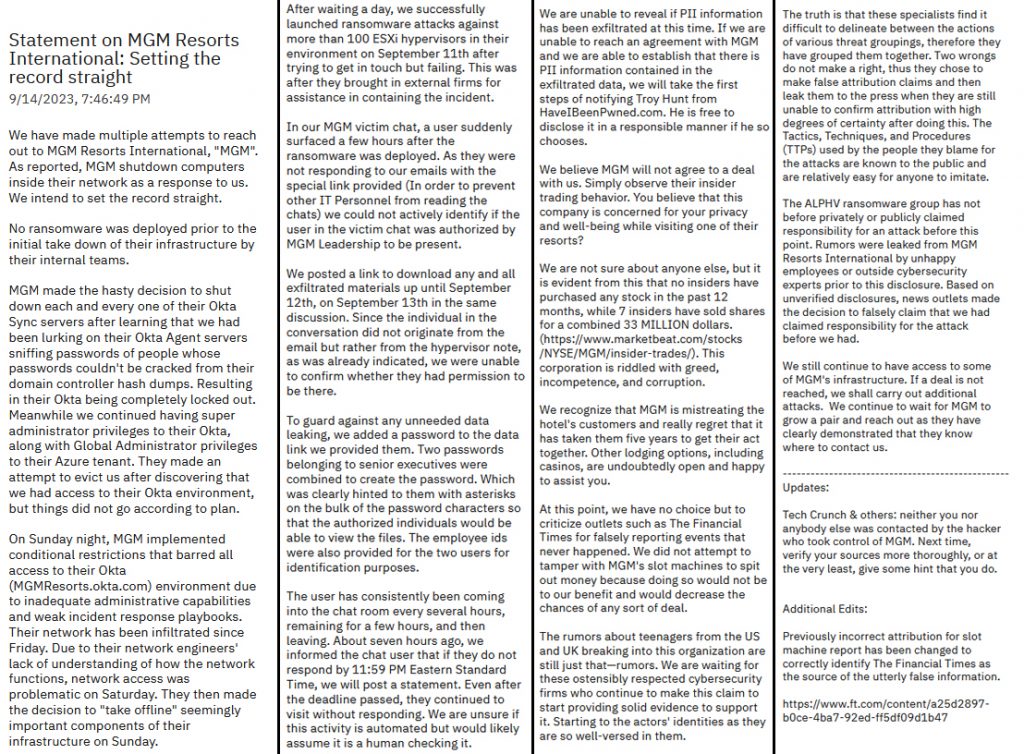
Initially, after the attack, ALPHAV had not posted anything relating to MGM on their Tor leak site, but late yesterday (14th September) they released a statement about the attack entitled Statement on MGM Resorts International:Setting the record straight – This comes after a number of misleading reports in from various newspapers, including one in the Financial Times that stated a that a source informed them that the gang tried to force slot machines to start spewing money out – A claim ALPHAV deny as it “would not be to our benefit and would decrease the chances of any sort of deal.“
Scattered Spider activity
Some of the recent events by Scattered Spider include:
- June – December 2022: Scattered Spider targeted telecommunications and BPO companies to gain access to mobile carrier networks and perform SIM swapping
- January 2023: Scattered Spider initiated a Bring Your Own Vulnerable Driver (BYOVD) attack campaign against various targets to exploit a high-severity vulnerability (CVE-2015-2291) in the Intel Ethernet diagnostics driver
- January 2023: Scattered Spider deployed phishing web pages to expand their target scope to include technology sector organisations
- May 2023: Scattered Spider expand their attack vector arsenal by abusing the Microsoft Azure Serial Console on virtual machines (VMs) to install third-party remote management tools within target environments
Known activities
Once the gang gains access to a network, they deploy a number of malware to gain a stronger foothold and elevate privileges. Known malware activity includes:
- BURNTCIGAR: Scattered Spider utilise this malware loader to disable endpoint detection tools and to exploit vulnerabilities in security systems to terminate defence services.
- Cuba Ransomware (COLDDRAW): A ransomware variant that is delivered via malspam campaigns or the Hancitor loader.
- POORTRY: A Windows kernel driver that terminates security software and deletes files as a component of BYOVD attacks. It is often used in conjunction with a userland component called STONESTOP, which installs the POORTRY driver and instructs it on what actions to perform. The first signed
POORTRY drivers were observed in June 2022, whereby Scattered Spider were attributed to the creation of the respective toolkits. - STONESTOP: Scattered Spider utilise this tool to install and command operations of the POORTRY Windows kernel driver
There is a theory that Scattered Spider are not one of the Russian-speaking cyber gangs that dominate the multi-billion-dollar ransomware industry with some suggesting that the gang is a western European one. This is another point ALPHAV make in their statement, saying that “The rumors about teenagers from the US and UK breaking into their organization are still just that – rumors“
“The group’s members are likely based in the UK or Europe and that they’re successful because they are very good at research and have good skills,”
Charles Carmakal, Chief CTO at Mandiant
The gang conducts Open Source Intelligence research (OSINT) to learn about individuals from social media profiles in order to impersonate them and make phone calls in English to glean passwords or or other data needed to access networks.
It appears that the access to MGM’s network was gained by a Social Engineering attack against an employee













