(11/09/23) Blog 254 – Ransomware – an in depth view of the Internets’ biggest problem
If you’ve been following my posts so far this year, you will have noticed that many of my posts involve the topic of ransomware – well there’s a reason for that – ransomware is by far the biggest cyber threat facing organisations in today’s world.
In this post, I will take a look at the complex world of ransomware – from Initial Access Brokers, affiliates, ransomware gang tactics, infighting, and payment issues brought about due to the Russian invasion of Ukraine.
Initial Access Brokers
Initial Access Brokers (IAB), are cyber criminals who focus on gaining privileged IT access to corporate environments, which they then auction off on dark web forums.
Most forums are a mix of Russian and English language with many written exclusively in Russian.
Posts by IABs will typically include a number of bullets describing the type of access available, the industry sector of the victim, the level of access gained, and the size (and thus revenue) of the victim organisation.
The below image is an example of such a post
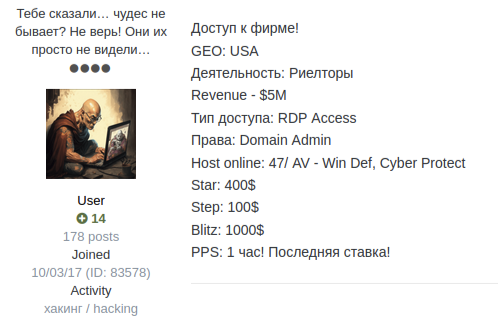
- Доступ к фирме! (Access to the company)
- Деятельность (Occupation): Describes the industry of the victim company. Finance, Retail, and Manufacturing are the three most common targets. In this example, the target company is a realtor (Риелторы)
- Тип доступа (access type): Describes the type of access obtained, most commonly RDP or VPN access.
- Права (Rights): Describes the level of privileges obtained.
- Revenue: Describes the revenue of the victim company, often obtained from U.S. based data providers publicly available online.
- Host Online: Often describes the number of hosts from the victim and sometimes includes antivirus and security systems in place.
- Start: The starting price of the auction.
- Step: The bid increments.
- Blitz: The buy it now price.
Often, an IAB will only put some details on the forum and then instruct would-be buyers to contact them privately through an encrypted messaging system, such as Telegram, for more details – this is typically done to improve the IABs anonymity and to attempt to evade law enforcement.
In terms of payment, IABs will usually only accept cryptocurrency – typically this will be Bitcoin, but Etherium is also a common alt-coin they accept.
A recent report into the world of IAB activity by researchers at flare found that:
- Attacks against U.S. companies are the most common, with 36% of all listings on the Tor forum “Exploit”. The UK is the second most common location for victim organisations.
- Finance and Retail are the most targeted industries, followed by Construction and Manufacturing
- The top 7 threat actors are responsible for 55% of listings
- Access to RDP and VPN accounts account for the vector in 60% of all posts
- The average price of corporate IT access is $1,328. Prices range from $150 to more than $120,000 based on the type of access being sold, the country, and the industry of the victim
- Some actors specifically advertise the lack of backup systems at victim companies, or advertise that they had access to backup systems. This suggests that some IABs likely expect the access they sell to be used for ransomware attacks.
IAB or affiliate?
IABs typically work alone and will sell access to the highest bidder, whereas an affiliate is someone who typically supplies access to one ransomware gang, often using that gangs specially built malware.
Affiliates will typically pay a ransomware gang a fee to use their access malware and then use that to target victims – this approach can see affiliates earn up to 75% of any ransoms paid.
Some ransomware gangs have specific rules for affiliates that they cannot target certain industries (e.g. hospitals, schools, governments) or organisations inside specific countries (e.g. BRIC countries).
Penalties for affiliates who do target victims not approved by a ransomware gang are often that the affiliate is made unwelcome by that gang and will no longer be able to sell the gang access.
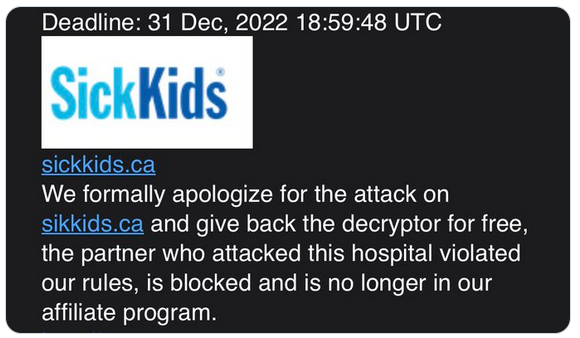
One such example of an affiliate being banned occurred towards the end of 2022. An affiliate working for LockBit targeted a Canadian hospice for ill children. The target was SickKids and the attack saw their entire network encrypted.
LockBit issued an apology to SickKids and offered the decrypter for free to the hospice.
Gaining access
As mentioned previously, IABs most commonly gain access to victim networks via Remote Desktop Protocol (RDP) and Virtual Private Network (VPN) technology.
These technologies are widely employed by organisations for external access to corporate sites – the rise in their use since Covid could explain the rise in these technologies becoming such a target for IABs
In the past few years, researchers have discovered many vulnerabilities affecting various VPNs technologies, which gives IABs a serious advantage in attacking a system.
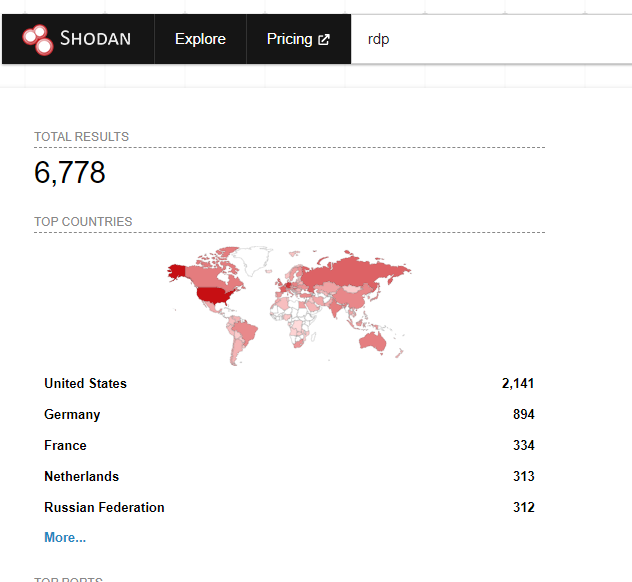
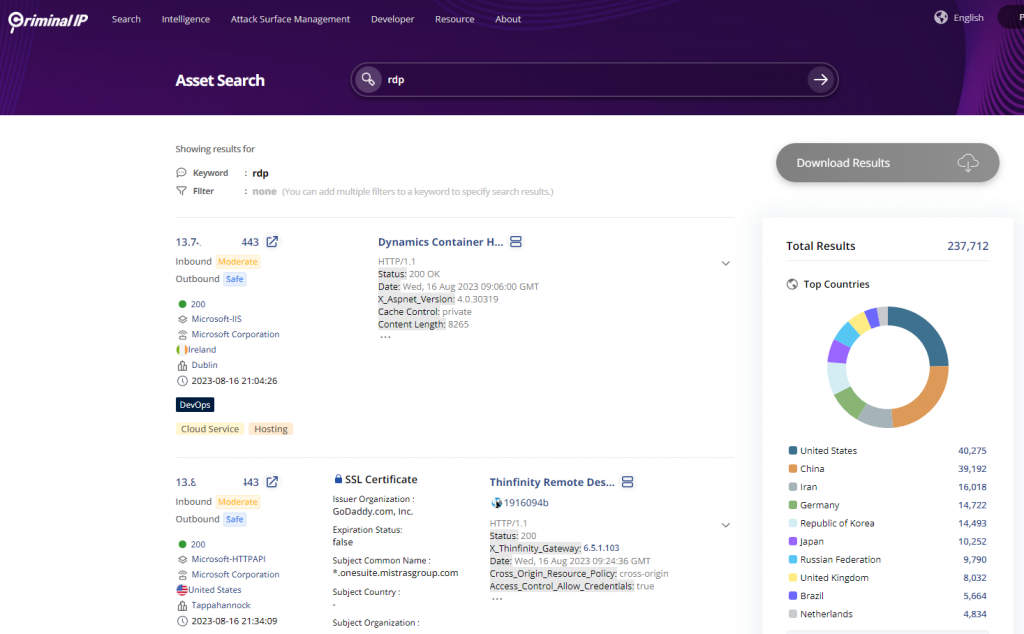
Internet scanning tools like Shodan, Censys, or Criminal IP allow IABs the ability to look for networks with RDP ports open to the internet.
A brute force attack of username and passwords, or the use of stolen login information from other breaches for a credential stuffing attack can see an IAB gain access within a matter of minutes.
0-days, supply chain attacks, bribery, and coercion
When a target is a potentially lucrative one, and RDP or VPN access is not an option, then a more specialised approach is often taken.
A recent “state of the Internet” report by Akamai, entitled ransomware-on-the-move shows a 143% increase in the use of 0-day exploits being used by IABs when comparing Q1 2022 and Q1 2023.
The recent supply-chain attacks against technologies and services such as Log4Shell, ProxyLogon, and MOVEit has enabled IABs to access victim systems in ways never seen before
In some instances, IABs have also been known to target staff at potential victim companies with bribery and coersion tactics. By scouring the web for staff members who show signs of being disillusioned with their company, the IABs reach out with offers of financial benefit if they agree to either provide the IAB with credentials, or would be willing to install malware inside the organisation.
Phishing still remains as the most commonly seen attack vector by IABs
Access sold / extortion time
Once an IAB has gained access to a target organisation, and the details sold to a ransomware gang, the gang will now start their attack.
Before launching the ransomware which will see the victim network paralysed, the common tactic of most gangs now is to go for the double-extortion approach.
Many companies have backup copies of their most sensitive data, so a simple encryption attack could fairly easily be recovered from by isolating the network, rebuild the targeted systems, and then a re-install of data from the backups.
Attackers know this, hence the exfiltration of data to a leak site. Even if a victim recovers their network, they still have the threat of their data becoming public if they fail to comply with the ransom demand.
Quite often, the encryption of the network is just used to send the message to the victim that the attackers mean business.
Living of the land
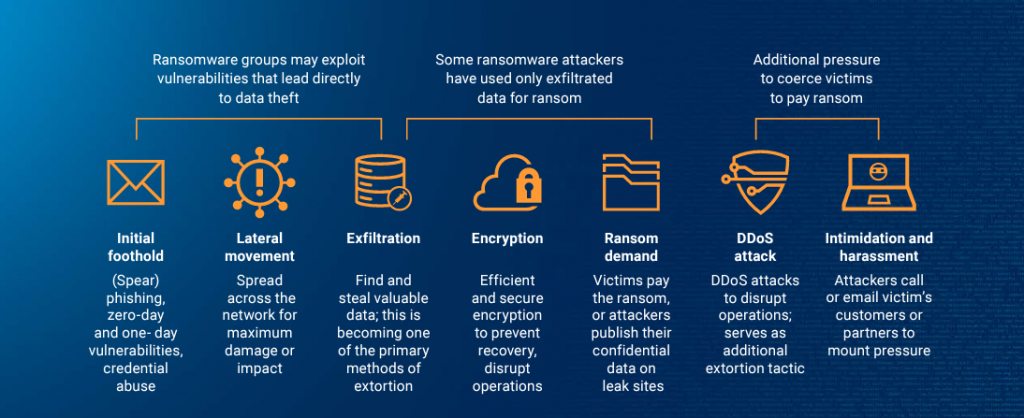
Before encrypting the victim files, the attackers will scour the target network, often using “Living of the Land” techniques to locate and exfiltrate as much data as possible.
Living off the land is the term given to the act of using services and technologies already present within the victim network to stealthily move around from system to system, often gaining elevated levels of privileges.
By using inbuilt Microsoft or Linux services and applications, it is less likely that any security tools will pick up suspicious activity and raise alerts than if the attackers deploy additional malware tools.
Some common Living of the land tools include:
- BASH or CMD terminal commands
- PowerShell scripts
- PSexec
- Microsoft.Workflow.Compiler.exe
- Mavinject.exe
- netsh.exe
- regedit.exe
- Scriptrunner.exe
- winget.exe
- apt-get
- batcat
- bundle
- certbot
- finger
Large lists of such tools and utilities can be found here, and here
Once the attacker has exfiltrated as much data that they feel would necessitate a victim to pay a ransom, the encryption process will begin.
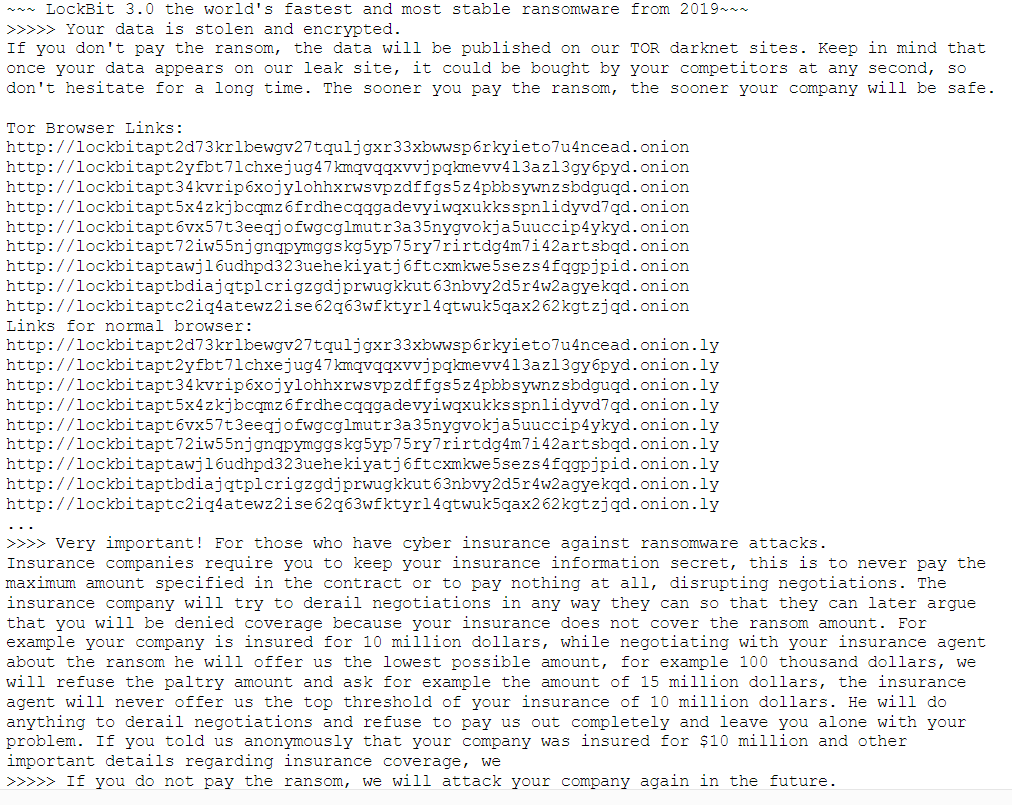
Once the victim files are encrypted, a message will be left by the encryption tool – typically the same message is placed in every folder of the victims network informing the victim of the attack, and how to go about contacting the ransomware gang to arrange payment of the ransom.
To add more pressure to victims, attacker sometimes launch secondary attacks at the target organisation, such as DDoS (Distributed Denial of Service) attacks, making it difficult for the organisation to even begin a recovery of network data.
Gang fights
Due to the vast sums of money which can be made from ransomware, it is inevitable that some gangs will go head to head with one another.
It is not uncommon to see the same victim targeted by multiple IABs and even multiple ransomware gangs.
Research has found some IABs offering the same access on multiple dark web forums
Akamai research found victims of multiple ransomware groups are almost 6x more likely to experience a subsequent attack within the first three months of the initial attack. It’s a race against time for organisations to close the gaps in their environment because of the likelihood of being attacked by another group.
No honour among thieves
In a few instances, members of ransomware gangs have had fall-outs for one reason or another with other members an have splintered off to form their own gangs.
One example of this is Conti.
On 25 February 2022, a message appeared on the darknet website run by the Conti ransomware gang.
The message pledged allegiance and support for the full-scale Russian invasion of Ukraine, announced by Vladimir Putin the day before.
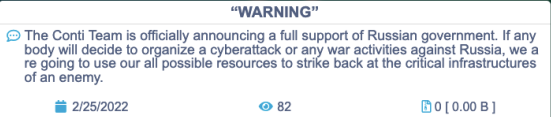
Two days after this mesasage was posted, a Twitter profile with the handle @ContiLeaks started leaking the ransomware group’s internal communications.
There are conflicting reports on who was behind the leak – it is suggested that the leaks were from a Ukrainian security researcher, but others suggest it was an affiliate against the war.
Regardless of the true source of the leak – The days were numbered for Conti and not long after, their operation ended – however, the leaks provided fuel for other to step up and take over their activities.
One of the beneficiaries of the disbanded Conti were Lockbit, who started reusing the ransomware code left behind by Conti, but LockBit were not the only gang to quickly capitalise on the Conti Leaks.
Payment of ransoms
When a company is hit with a ransomware attack, the usual messages left behind instruct the victim to pay monies into a cryptocurrency wallet – typically bitcoin.
Some ransomware gangs have used the same crypto-wallet for all victims, whereas other prefer to use a separate wallet for each victim – this makes it harder for analysis of the blockchain to determine where the monies get re-routed before the finances are exported out into hard cash.
Some countries make it an offence to pay any sort of ransom to an attacker.
For example, the UK has enforced financial sanctions under the Cyber sanctions regime since May 2019. The Cyber sanctions regime was originally introduced
when the UK was part of the European Union (“EU”). Following Brexit, the Cyber (Sanctions) (EU Exit) Regulations 2020 were introduced under the Sanctions and Anti-Money Laundering Act 2018.
Breaches of financial sanctions are a serious criminal offence and the Office of Financial Sanctions Implementation (OFSI) has the power to impose civil monetary penalties for breaches of financial sanctions under powers in the Policing and Crime Act 2017.
The statutory maximum penalty OFSI may impose is the greater of £1 million or 50% of the value of the breach (which may be estimated).
Russian invasion of Ukraine
The illegal war waged by Vladimir Putin against Ukraine has seen further restrictions posed when it comes to ransom payments – Since the invasion of Ukraine in 2022, a number of countries have placed sanctions on many Russian citizens. Because the biggest proportion of ransomware gang members are Russian, these sanctions place an even heavier penalty for companies if they choose to pay a ransom.
U.S. law imposes strict liability on anyone that makes a payment to a sanctioned entity—meaning that a lack of intent to flaunt sanctions doesn’t exonerate the paying party.
The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) and its Financial Crimes Enforcement Network both have highlighted the topic of ransomware payments in recent months. OFAC said in September 2022 that it “strongly discourages” extortion payments and reiterated that it can take action against payers.
“Under the authority of the International Emergency Economic Powers Act (IEEPA) or the Trading with the Enemy Act (TWEA), 12 U.S. persons are generally prohibited from engaging in transactions, directly or indirectly, with individuals or entities (“persons”) on OFAC’s Specially Designated Nationals and Blocked Persons List (SDN List)”
OFAC Advisory on Potential Sanctions Risks for Facilitating Ransomware Payments
Final thoughts
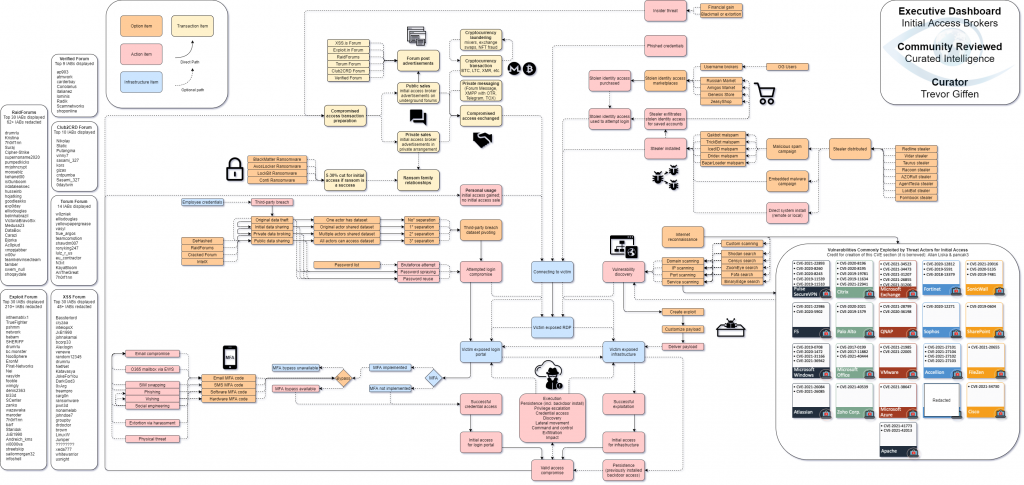
The world of ransomware is a very complex one, with multiple players, multiple technologies, and multiple attack vectors, all made harder by the use of dark web technologies, encryption, and cryptocurrencies – all designed to keep the users as anonymous as possible.
An excellent graphic which depicts this complex world is one published by Trevor Giffen, the founder of @CuratedIntel – a collection of intelligence researchers and incident responders working to make the Internet a safer place.