(30/08/23) Blog 242 – Multiple threat actors using Lockbit 3.0 code base
Lockbit are one of the most successful ransomware gangs active on the Internet and have been responsible for some of the largest ransom demands seen.
A report jointly published in June this year by multiple agencies from the US, Australia, Canada, France, Germany, New Zealand, and the U.K states that since first appearing on the scene back in 2020, they have accrued approx. USD$91M in ransom payments.
The success of the gang has not gone unnoticed by law enforcement, but also by other criminals, and many other gangs are now using the same underlying code for their ransomware attacks.
Lockbit evolution
The ransomware generator for lockbit has undergone a number of development updates since 2020.
The first variant (Lockbit 1.0) was known as the .abcd variant after the activity of renaming encrypted filed with the extension .abcd
The second variant did not differ in its encryption methods, but renamed files with the .Lockbit extension – as such, this appears to be a move to make Lockbit a name to be feared.
The third variant had a number of significant changes to how the encryptor worked and how victims contacted the gang. This new variant was dubbed Lockbit 2.0 A.K.A. LockBit Red.
LockBit 3.0 A.K.A. Lockbit Black was built from code ultimately leaked from the Conti gang. (see Below).
LockBit 4.0 A.K.A. Lockbit Green is the latest variant which we now know to also be based on the Conti code.
Conti source code leak
It is known that the code for the Conti ransomware generator was revealed to the public via a Ukrainian researcher using the Twitter handle @ContiLeaks in February 2022.
The researcher leaked 393 JSON files containing over 60,000 internal messages taken from the Conti and Ryuk ransomware gang’s private XMPP chat server.
One of the leaked files was a password protected file which was soon cracked to reveal that it was the source code for the Conti ransomware encryptor, decryptor, and builder platform.

Shortly after this devastating breach of their systems, the Conti gang shut its operations. The code however lives on.
LockBit leak
Since the leak of the Conti source code, multiple variants of the code have been seen in use by other gangs.
One such gang is the “BlooDy” gang which were first seen online in May 2022, just 2 months after the Conti Leak.
Although many gangs have repurposed the leaked Conti code, it was a leak of the actual LockBit code that has spawned so many new variants.For example, BlooDy have now moved to use the leaked LockBit 3.0 code.
In September 2022, two twitter users (@Ali_qushji and @protonleaks) shared links to LockBit v3.0 builder files.
Both twitter accounts no longer exist, but archive data shows the tweet from @Ali_qushji and the link to the online file share where the builder can be obtained.


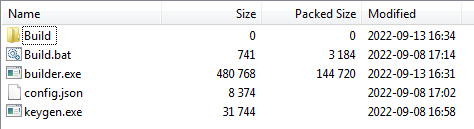
Shortly after the LockBit 3.0 leak, the first use of the code base was seen in a ransomware attack by a gang calling itself the “National Hazard Agency” was seen in September 2022.
Since then, many variants of the LockBit3.0 code have been seen in malware samples.
According to a recent report from Kaspersky, they have detected 396 distinct LockBit samples in telemetry data obtained from Kaspersky customers across the world.












