(18/08/23) Blog 230 – QR codes used in phishing attack to bypass email security scanners
A novel approach to phishing has surfaced in a large-scale attack on a major US energy supplier.
The attack begins with a phishing email that claims the recipient must take action to update their Microsoft 365 account settings.
The emails carry PNG or PDF attachments featuring a QR code the recipient is prompted to scan to verify their account.
As is common in many phishing attacks, to add a sense of urgency to the affair, the emails state that the target must complete this activity in 2-3 days.
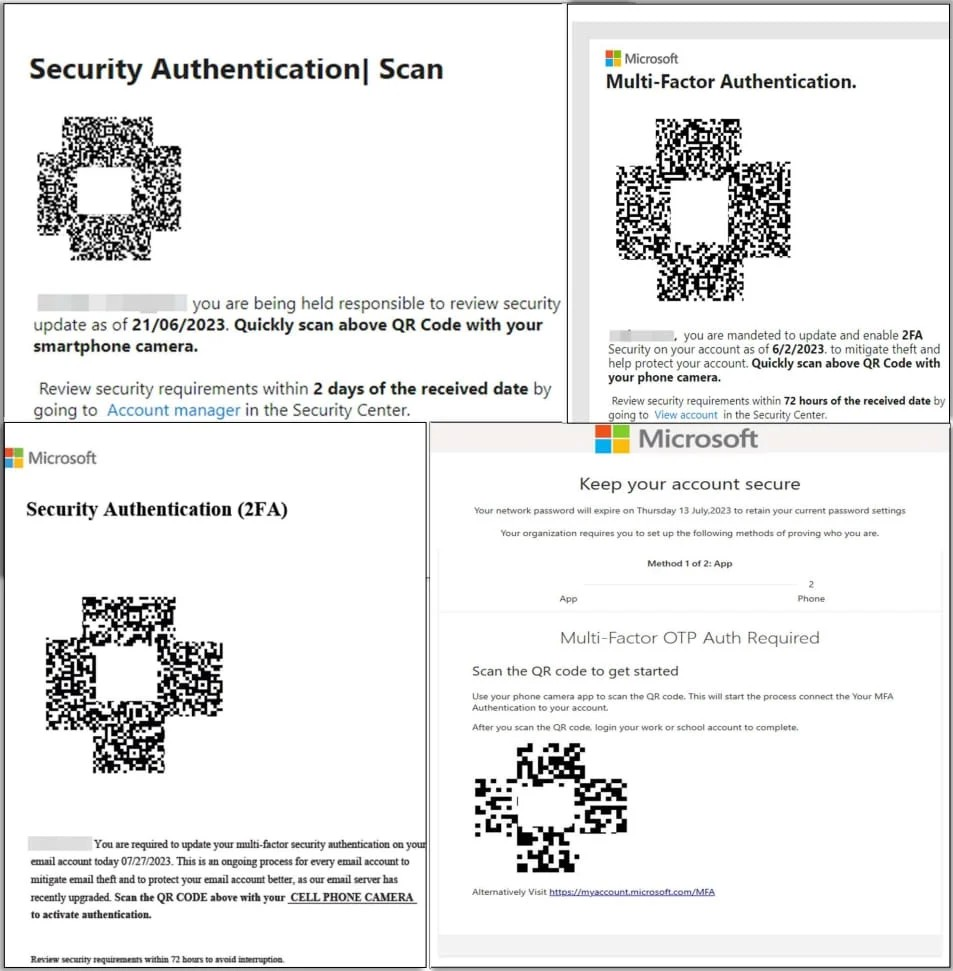
The use of QR codes embedded in images allows the threat actors to bypass email security tools which scan messages for known malicious links, thus allowing the phishing messages to reach the target’s inbox.
To evade other security controls, the QR codes in the campaign use redirects in Bing, Salesforce, and Cloudflare’s Web3 services to take the victims to a Microsoft 365 phishing page.
Hiding the redirection URL in the QR code, abusing legitimate services, and using base64 encoding for the phishing link all help evade detection and get through email protection filters.
The use of QR codes in phishing campaigns is not a new thing, but this campaign is the first one at such scale. In this campaign, over 1,000 malicious emails were sent by the attackers.
In the past, attacks hidden inside QR codes targeted victims in France in 2019 and in Germany in 2021.












