(14/08/23) Blog 226 – The future of (no) passwords
For many people, juggling multiple passwords becomes not only a chore, but also a systematic failure in the protection of accounts and services.
We all know the principles of good password hygiene*, it’s talked about endlessly on websites, and in the printed press. However, evidence supports the fact that many of us simply don’t put into practice those principles.
A quick cursory search online for “most common passwords” returns multiple websites which quote various sources offering their top ten list of commonly seen passwords, including old favourites such as “qwerty” and “123456”.

Move to MFA
For many years, security conscious vendors, platforms, and individuals have extolled the virtues of Multiple-Factor Authentication (MFA), or Two-Factor Authentication (2FA).
MFA involves a combination of attributes relating to the security of your account / device.
The premise of MFA is that to unlock your account or service, you must provide knowledge of 2 or more distinctly different pieces of data.
Typically, these pieces of data fall into one of a number of categories:
- Something you know
- Something you have
- Something you are
A username and a password are both examples of the same type of data – Something you know, and as such do not qualify for MFA. If an attacker can guess, or break your password, or obtain the data from another breach, they have all they need to access your accounts.
A username/password combo AND a PIN sent to your mobile phone is an example of something you know and something you have. In this example, you provide the username/password data, the system generates a unique value and sends it to your registered device which you then have to re-enter to the system to gain access.
Technologies such as the Google Authenticator app, or Cisco Duo offer a cryptographic way of sending authentication codes to users when they log in to their systems, and allow corporate IT departments a useful way of auditing log-on events.

With this approach to account security, if a threat actor obtains your username/password, they will still be unable to access your data unless they somehow can intercept the authenticator code, or have access to the device receiving the code.
One such attack for this is a SIM swap attack. This attack involves threat actors tricking your mobile provider that they are you, and that you want to port your number to a new SIM.
If the attacker is successful in achieving the SIM swap, then they can intercept any/all MFA requests and as such access your accounts.
Many mobile providers employ technologies and systems to identify fraudulent SIM swap attempts, but not all providers are as diligent as others, plus threat actors occasionally go to the lengths of bribing or blackmailing call centre operatives, or even have their own insiders working within mobile operators to help facilitate these such attacks.
A username/password combination used in conjunction with bio-metric data such as a fingerprint, voice imprint, or face scan is an example of something you know and something you are.
Again, if a threat actor has your username/password data, they cannot access your account without the associated bio-metric data.
Systems using bio-metrics can be fooled – copies of fingerprints can be obtained and used in conjunction with a warm glove can defeat some systems that not only look at the fingerprint pattern, but also the presence of body heat.
The rise of AI systems has already seen attacks against voice-recognition systems (I posted about this here)
FIDO is the future
FIDO – Fast Identity Online is a collection of technologies that aims to create a full range of technologies which support the secure storage and transmission of security data, such as bio-metrics, Trusted Platform Models (TPM), Security tokens, Smart cards, Near-Field Communication (NFC) systems, and more.
The FIDO Alliance is a open industry association which was launched in 2013 to promote the use of non-password based systems. Members of the alliance include Apple, Microsoft, Google, American Express, Visa, Intel, Lenovo, Meta, Samsung, Paypal, and many others.
When registering for a service which supports the FIDO standards, the user generates a user account in the normal manner, and then uses a FIDO certified device to generate a cryptographic key-pair which is associated with that account.
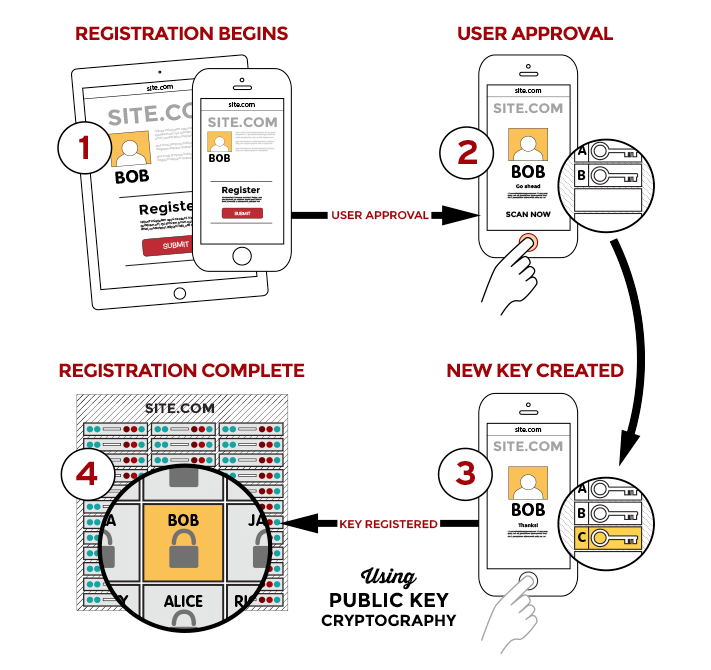
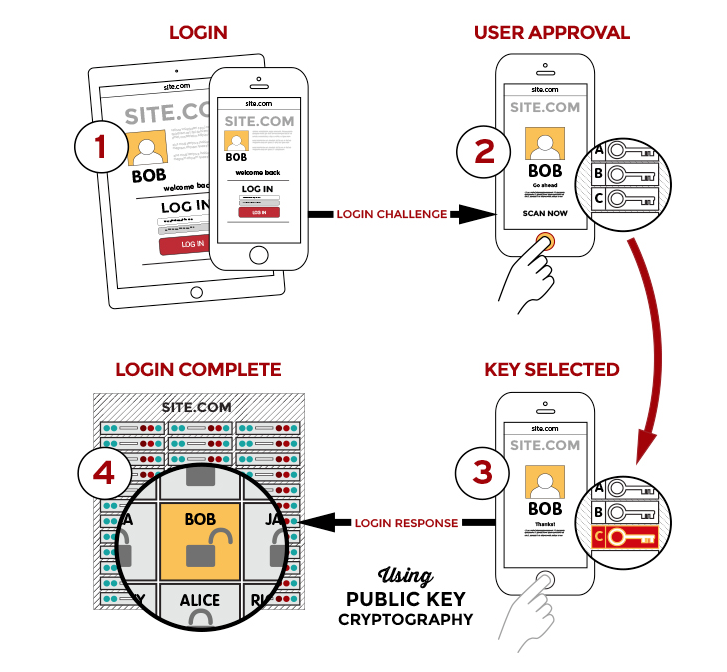
When the user wishes to log-on to the service, the user provides their account credentials and the service provides a challenge back to the device linked to the account (mobile phone, USB key fob, etc.) The device will prompt the user for the additional data – PIN, fingerprint, face-scan, etc.
Password phaseout
In the examples above, passwords are still used when creating and accessing accounts, but these processes are being phased out gradually by manufacturers and service providers.
Back in April, I posted about how Google had now introduced passkeys for users which will allow anyone using a Google service the ability to access their accounts and data without ever presenting a password.
In this new approach, a user generates a passkey for their services which is linked to their mobile device (or similar hardware) and once registered, need never enter a password again – To access the Google service, the user simply unlocks their mobile device, or provides data to their USB key, etc. The data stored in their device authenticates with the Google service and allows the online account to be accessed.
Roll-out of such services is gradually gathering pace, but it will still be quite a while until the death pf the password is finally announced, but wherever possible, if a service offers FIDO access without passwords – my advice is to use it.
*Password Hygiene
For those who still don’t know what good password hygiene looks like – here’s a list of good tips…
- Don’t re-use passwords
- If you must re-use passwords, ensure important accounts such as your email and bank accounts ALWAYS have unique passwords
- Create strong, memorable passwords – Three Random Words is a good approach
- Avoid using words which could be guessed – i.e. pet names, favourite sports team, etc.
- Never share passwords with others
- It’s OK to write passwords down, but store your list away from your PC
- Consider using a password manager tool instead of writing them down
- Ensure your password managers’ primary-password is unique and strong












