(13/08/23) Blog 225 – Checkmate – Knight ransomware posing as TripAdvisor complaint
A Security researcher at Sophos has discovered a ransomware campaign which attempts to infiltrate a victims devices posing as a TripAdvisor complaint.
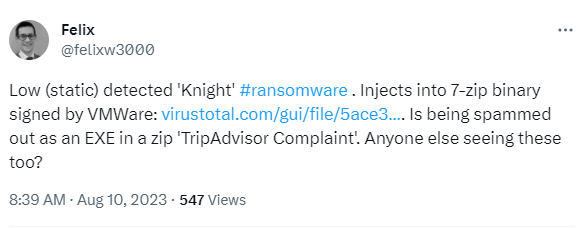
The researcher – @felixw3000 posted on the 10th August that he had seen the ransomware being sent as an EXE file posing as a TripAdviser complaint in multiple emails.
Cyclops to Knight 3
The ransomware is a re-branded Cyclops malware which has been around since May 2023. The gang posted on their blog in June that they intended to release a new version of their ransomware tool and it would be renamed Knight.
The updated malware is designed to attack VMWare ESXi, Linux and MacOS as well as Windows systems.
Fake email attachments
The email campaign being used to target victimes contain various attachments include ZIP files and PDFs.
The attachments are named ‘TripAdvisorComplaint.zip’, or ‘TripAdvisor-Complaint-[random_value].PDF.htm’
The files actually contain executables named ‘TripAdvisor Complaint – Possible Suspension.exe’.
When the file is opened, it will use Mr.D0x’s Browser-in-the-Browser phishing technique to open what appears to be a window to TripAdvisor, containing what seems to be a complaint submitted to a restaurant, asking the user to review it.
Clicking the ‘Read Complaint’ button will download an Excel XLL file named ‘TripAdvisor_Complaint-Possible-Suspension.xll’.
When you open the XLL file, Microsoft Excel will prompt the user as to whether they want to enable the add-in.
Enabling the add-in will cause the Knight Lite ransomware encryptor to be injected into a new explorer.exe process and begin to encrypt the files on the victim computer.
When encrypting files, it will append the .knight_l extension to encrypted files’ names.
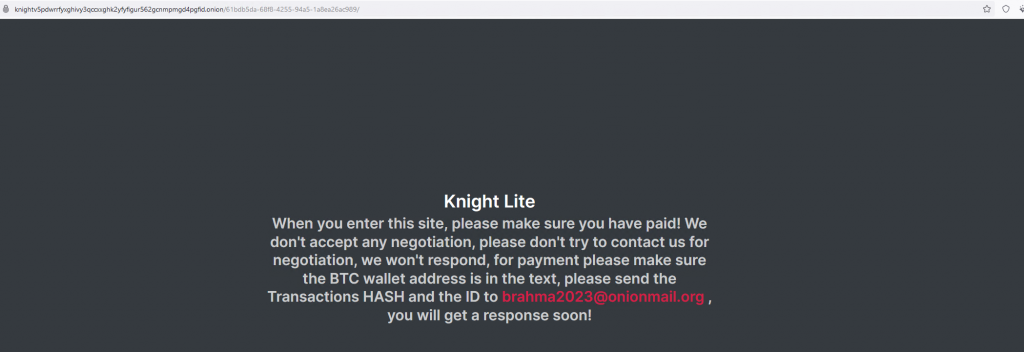
The ransomware also places a ransom note named How To Restore Your Files.txt in each folder on the affected device. The ransom note demands $5,000 be sent to a Bitcoin address along with a link to Dark web Knight_Lite website.
Low detection rate
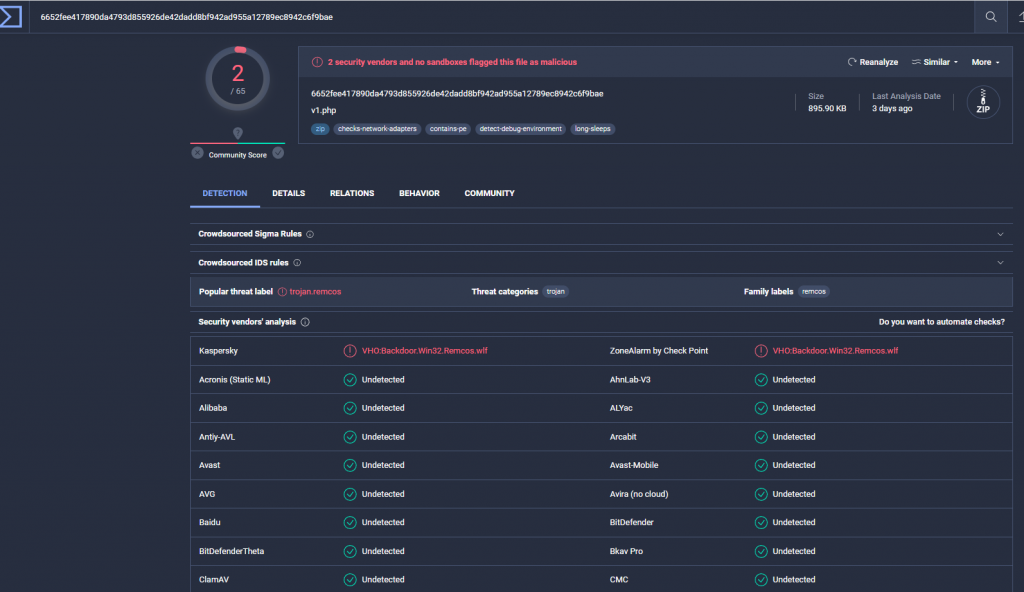
The relative newness of this malware means that currently, the anti-malware detection rate is fairly low.
Samples of the malware uploaded to VirusTotal show different detection rates depending on the sample with one such sample only being identified as malicious by 2 anti-malware utilities
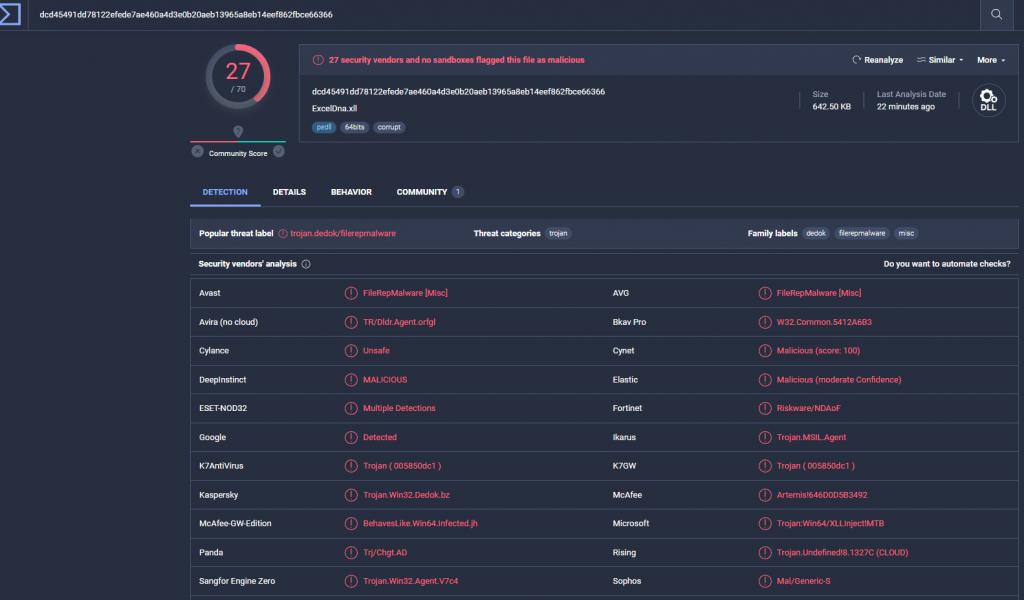
Another sample was found to be malicious by 27 vendors.