(31/07/23) Blog 212 – New Android malware retrieves credentials from images
A new malware variant has been seen on the Google play store which aims to steal sensitive user data including cryptocurrency credentials and associated funds.
Discovered by Trend Micros’ Mobile Application Reputation Service (MARS) team, the malware has been named CherryBlos and uses various distribution channels, including social media, phishing sites, and deceitful apps available on Google Play.
CherryBlos
The CherryBlos malware was first seen in April 2023 in the form of an APK file called Robot999 being promoted on various social media sites such as Telegram, Twitter, and YouTube, under the guise of AI tools or coin miners.
Trend Micro researchers traced the origins of Robot999 to a Telegram channel where “Ukraine Robot” had been promoting cryptomining utilities

In April 2023, the group offered the Robot999 APK file which contained the CherryBlos malware
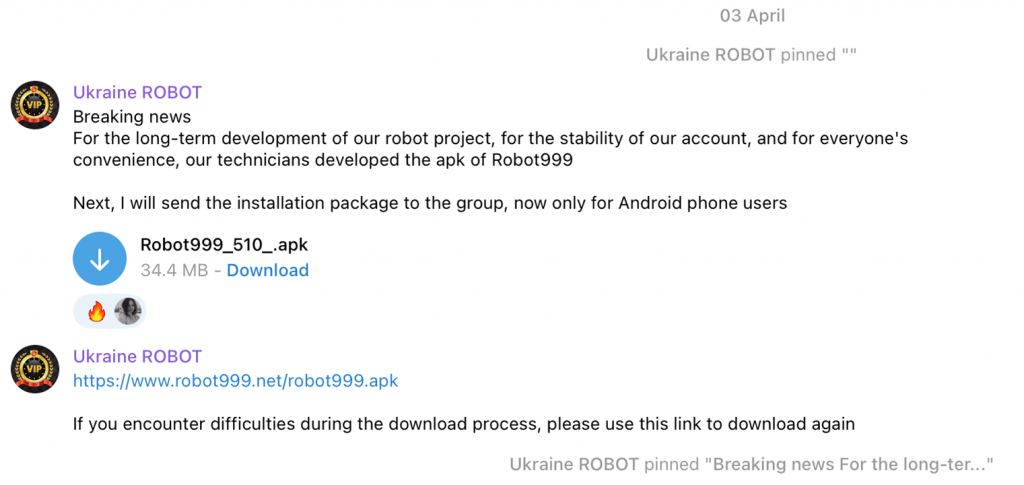
Trend Micro staff have so far identified four apps which contain the malicious CherryBlos files:
- Robot 999
- GPTalk
- Happy miner
- SynthNet
Like most banking trojans, CherryBlos requires accessibility permissions to work. When a victim opens the malicious app, a popup dialogue box is displayed prompting users to enable accessibility permissions. An official website will also be displayed via WebView to avoid suspicion from the victim.
The accessibility permissions, when granted allow the malicious app almost unfetted access to data on the victims device.
After gaining accessibility permissions, CherryBlos will request two configuration files from a Command & Control (C2) server.
The C2 server address is stored as a resource string within the app and the communication between victim and server uses HTTPS.
Credential and asset theft
CherryBlos uses several approaches to steal credentials or assets from its victim’s cryptocurrency wallets including well-designed fake wallet user interfaces when users launch official apps.
During their analysis of the malware, Trend Micro researchers identified that the malware uses JSON to organise and send captured credentials to remote servers, one of the JSON variables is called ZJC which is a first-letter combination of the Chinese translation of “mnemonic” – “助记词/Zhu-ji-ci”. This could be an indicator of the origin of the malware.
CherryBlos can also modify withdrawal addresses by overlaying a Fake interface to show the original address while users make withdrawals in a legitimate Binance app.
CherryBlos looks for one of three keywords (“Withdrawal”, “Confirm” and “Submit”) in Binance’s app, and when one of these words is detected, the malware records data such as coin type and amount and overlays a fake withdrawal view over the Binance app with pre-recorded values based on user input.
Under the fake view, the actual address and withdrawal amount in the Binance app is modified to send money to an attacker-controlled address.
Optical Character Recognition
In a novel approach, CherryBlos can read media files stored in the external storage and use OCR to recognise potential mnemonic phrases in the images.
Although not recommended, it is common for crytocurrency wallet holders to take screenshots, or photographs of their wallet pass phrases (mnemonics) for ease of referal. Using previously granted permissions, CherryBlos will scan all images looking for text and send results back to the C2 servers mentioned earlier.












