(09/07/23) Blog 190 – Ukraine war has changed the cyber threat landscape
A report by Google’s Threat Analysis Group (TAG) has shown how the Russian war against Ukraine is not just happening on the battlefield, but is very much happening in cyberspace
The report , entitled “Fog Of War” looks at the change in the threat landscape for the 1st year of the conflict.
Key findings
- Russian government-backed attackers have engaged in an aggressive, multi-pronged effort to gain a decisive wartime advantage in cyberspace, often with mixed results.
- There has been a notable change in the attention given to Ukraine by different groups. This shift is accompanied by a significant rise in the number of destructive attacks on Ukraine’s government, military, and civilian infrastructure. Additionally, there has been an increase in spear-phishing activities targeting NATO countries, along with a rise in cyber operations that aim to support various Russian objectives. As an example, it has been observed that threat actors are hacking and leaking sensitive information to promote a specific storyline.
- Moscow has leveraged the full spectrum of Information Operations – from overt state-backed media to covert platforms and accounts – to shape public perception of the war
- These operations have three goals: (1) undermine the Ukrainian government; (2) fracture international support for Ukraine; and (3) maintain domestic support in Russia for the war. There have been spikes of activity associated with key events in the conflict, such as the buildup, invasion, and troop mobilization in Russia.
- Google have made aggressive efforts across products, teams, and regions to counter these activities and aim to take action whenever they violate policies and will disrupt overt and covert information campaigns. Google continues to face relentless attempts to circumvent their policies.
- The invasion has triggered a notable shift in the Eastern European cybercriminal ecosystem that will likely have long term implications for both coordination between criminal groups and the scale of cybercrime worldwide
- Some groups have undergone divisions due to political allegiances and geopolitics, while others have experienced the loss of prominent members. This will impact our perception of these groups and challenge our conventional understanding of their capabilities.
- Another noteworthy trend is the increasing specialization within the ransomware ecosystem, where tactics are blended across different actors, making it harder to definitively attribute attacks. Additionally, the war in Ukraine has been characterized not only by what we anticipated, but also by what we did not observe. For instance, there was no significant increase in attacks against critical infrastructure outside of Ukraine.
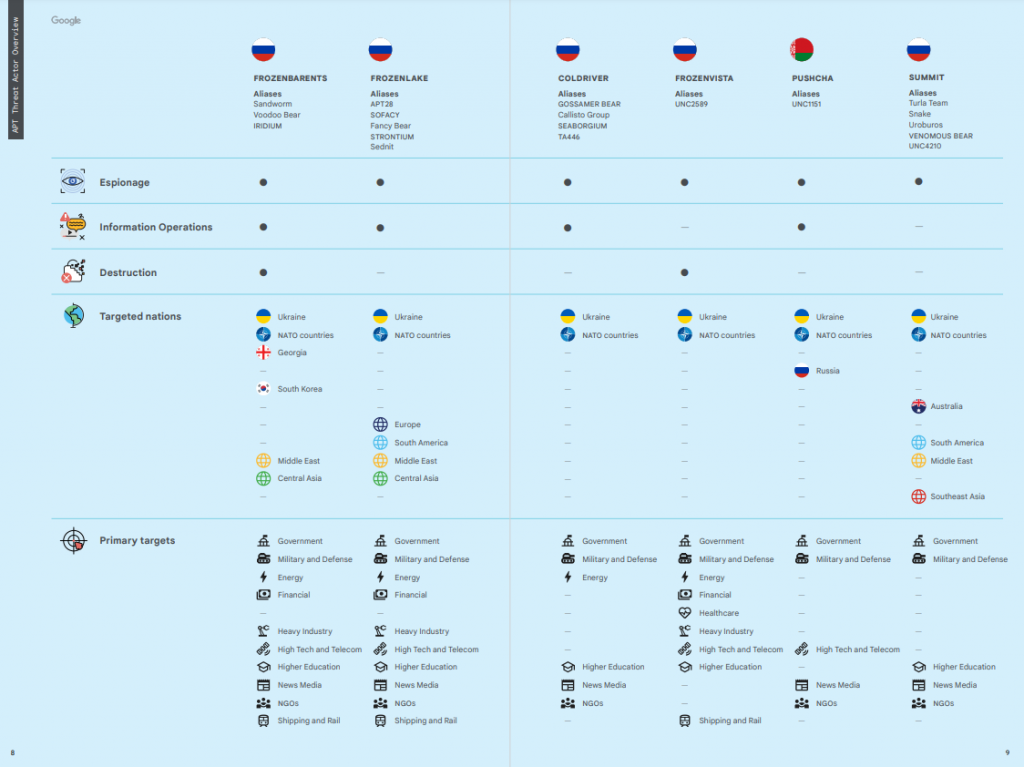
Government-backer attackers conducting online operations against multiple targets
At least six well-known hacking groups are being used by the Russian government to attack multiple Ukrainian targets, and those in support of Ukraine.
The threat actors are conducting espionage, intelligence gathering ops, and destruction campaigns against targets primarily in Ukraine, but also in NATO countries, South Korea, Australia, South America and the Middle East.
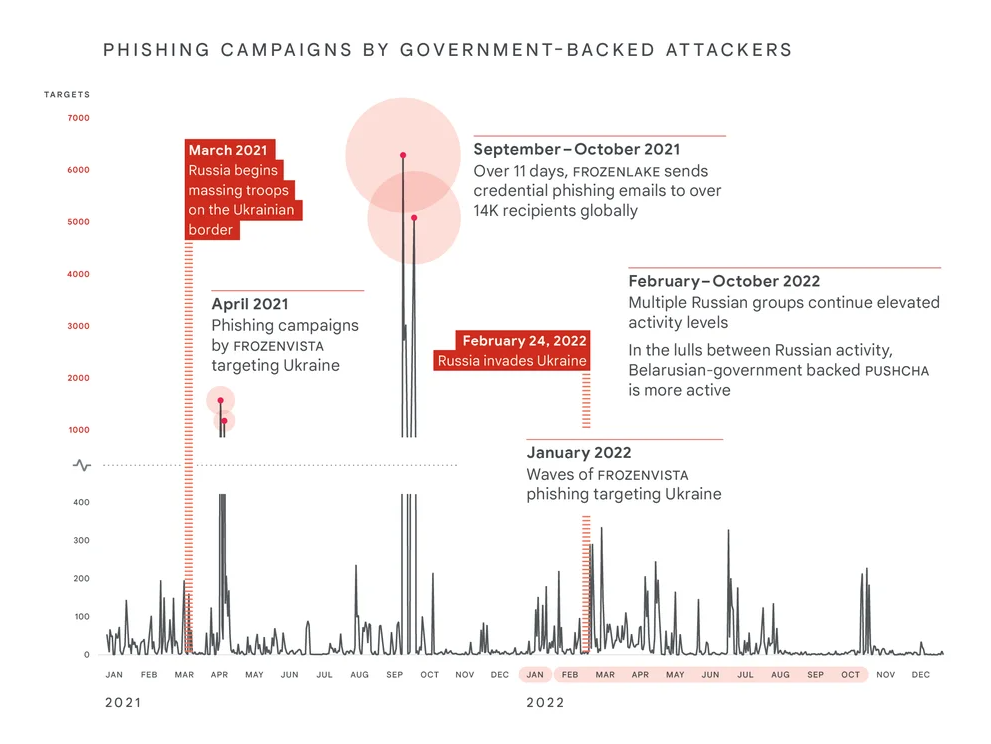
The war started before troops were mobilised
Russian government-backed attackers started their cyber operations in 2021 during the run up to the invasion.
Google systems identified a 250% increase in Russian phishing campaigns directed against users in Ukraine in 2022 (compared to a 2020 baseline).
To help counter these attacks, Google disrupted phishing campaigns against the Ukrainian government and military organizations, as well as critical infrastructure, media and the information space.
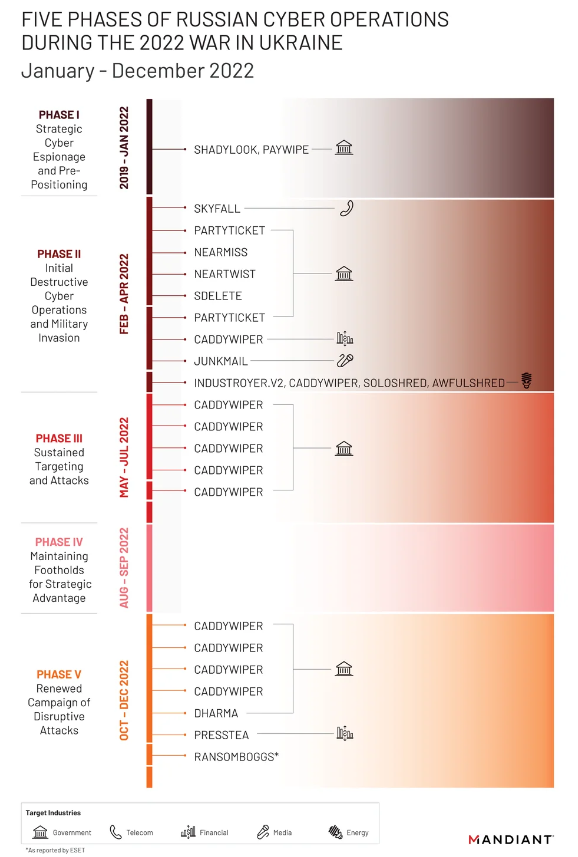
Waves of malware launched
Russian Armed Forces’ Main Directorate of the General Staff (GRU) -sponsored
actors have used destructive malware to disrupt and degrade Ukraine’s government and military capabilities. In conjunction with these attacks, there have been similar attacks on civilian infrastructure in an attempt to undermine the public’s trust in the Ukrainian government’s ability to deliver basic services.
There have been more destructive cyberattacks in Ukraine during the first four months of 2022 than in the previous eight years with a notable spike in activity at the start of the invasion. In contrast to the NotPetya attacks of 2017, there is little evidence of a spillover effect outside Ukraine.
Users in NATO countries face intensified targeting
Since the war began, a 300% increase in Russian phishing campaigns directed against users in NATO countries has been observed (compared to a 2020
baseline).
Conducted primarily by a Belarusian government-backed group that is closely aligned with Russia , these campaigns may reflect a longstanding Russian strategic priority to gather better insight into NATO activities.
A war of propaganda
Best known for their information operations that sought to sway public opinion during the 2016 US presidential election, the Internet Research Agency (IRA) has evolved significantly.
Since the invasion of Ukraine, the domestically focused cluster of IRA-related activity has shifted from a range of domestic Russian political issues to focus almost exclusively on Ukraine and mobilization.
Several campaigns also promoted the business interests of Russian oligarch Yevgeny Prigozhin, the financier of the IRA, and the leader of the Wagner group of mercenaries.
Amplifying Prigozhin propaganda film on Ukraine
Prigozhin has funded several movies through a partial ownership stake in the film company, Aurum LLC. These movies have high production value and communicate narratives portraying Russia — especially Russian military and mercenaries — in a positive light.
In 2021, they released “Солнцепёк” (“Sunlight” or “Blazing Sun” in English), which takes place in eastern Ukraine and claims to be a story based on true events from 2014 of Russian mercenaries, connected to the paramilitary Wagner Group, protecting Russians in Ukraine against Ukrainian forces.
Deepfakes used to undermine Ukrainian president
On March 16, an information operation targeting Ukraine promoted a fabricated message alleging Ukraine’s surrender to Russia via the suspected compromise and defacement of the Ukraine 24 website and news ticker in a Ukraine 24 TV broadcast with a written message.
The message was also delivered through an artificial intelligence (AI)-generated “deepfake” video impersonating Ukrainian President Zelensky delivering that same text.

Conclusion
It is very apparent that the Russian government will utilise almost any tactic in an attempt to win the illegal war against Ukraine and to save Putins embarrassment.
Whilst the focus of the attacks are on Ukrainian targets and those of NATO countries, the effects of the war are being felt globally in the worlds of finance, fuel, food, and cyberspace and will do so for a while to come.
Google’s analysts assess with high confidence that Russian government-backed
attackers will continue to conduct cyber attacks against Ukraine and NATO partners to further Russian strategic objectives, and that Moscow will increase
disruptive and destructive attacks in response to developments on the battlefield that fundamentally shift the balance — real or perceived — towards Ukraine (e.g., troop losses, new foreign commitments to provide political or military support, etc.).
These attacks will primarily target Ukraine but increasingly expand
to include NATO partners.
Russia will continue to increase the pace and scope of information operations to
achieve the objectives described above, particularly in areas of international funding, military aid, domestic referendums, and more.
What’s less clear is whether these activities will achieve the desired impact, or simply harden opposition against Russian aggression over time.













