(05/07/23) Blog 186 – Akira ransomware decryptor released
Security researchers at Avast have released a decryptor tool which allows victims of the Akira ransomware the ability to recover files without paying any money to the gangs who use it.
Currently, the tool only works on Windows platforms, but Avast are working on a version for Linux systems which should be released soon.
Avast produced the decryptor a while ago and have been using it to help victims recover files. They released to tool for public use towards the end of June.
At the time of writing, the tool is only available via the Avast website, but I suspect that it will be included in the NoMoreRansom site soon (Avast are one of the partners of that project).
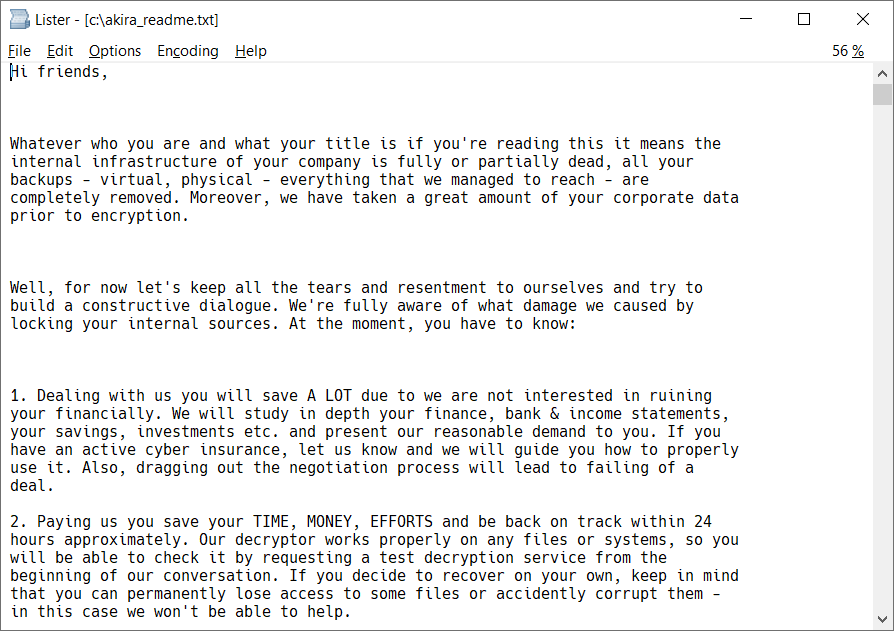
What is Akira?
The decryptor for Akira released by Avast is for the ransomware which 1st appeared in March of this year, as opposed to the ransomware with the same name which was discovered in 2017.
The Akira ransomware group has successfully targeted several high-profile organisations– including the government of Nassau Bay in Texas, Bluefield University in Virginia, and a state-owned bank in South Africa.
One of the gangs most recent targets was London Capital Group (LGC), who are still suffering the effects of the attack.

When the ransomware is deployed on a victim machine, the malware generates a symmetric key pair using the random number generator implemented by Windows CryptoAPI*. This key is then encrypted using the RSA-4096 cipher and is appended to the end of encrypted files to act as a signature for the files on the system.
*NOTE: The recently discovered Linux variant of Akira works in exactly the same way as the Windows variant except for the fact it uses the Crypto++ library as opposed to the Windows CryptoAPI.
The files themselves are encrypted by the Chacha 2008 cipher, the public key of which is hardcoded in the ransomware binary and differs per victim.
Once the malware completes its tasks, a ransom note is added to every folder