(04/07/23) Blog 185 – New malware targeting Spanish bank account holders
A highly successful malware campaign has been ravaging bank accounts of Spanish and Chilean customers for the last 2 years according to a report produced by a cyber security researcher called Pol Thill
The report which is entitled Neo_Net | The Kingpin of Spanish eCrime was conducted as part of a Malware Research Challenge sponsored by SentinelOne and vx-underground.
Neo_Net
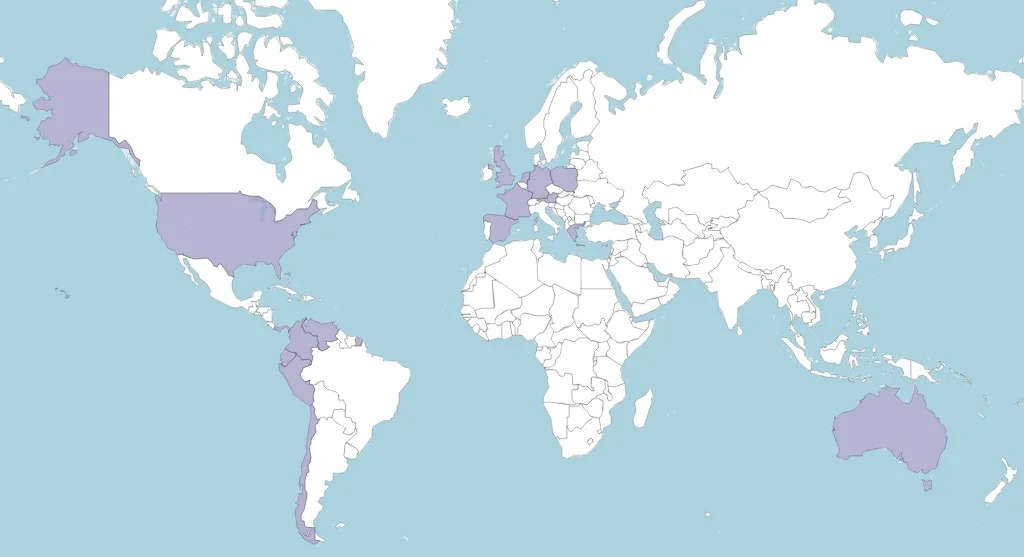
According to the research conducted for the report, Neo_Net has been conducting a global eCrime campaign targeting clients of prominent Spanish and Chilean banks between June 2021 to April 2023.
By tailoring the infrastructure used by the malware, the campaign has achieved a high success rate even though the malware uses relatively unsophisticated tools.
To date, the malware has netted the threat actors behind Neo_Net over €350,000 from victims’ bank accounts and has compromised the Personally Identifiable Information (PII) of thousands of victims.
How it works
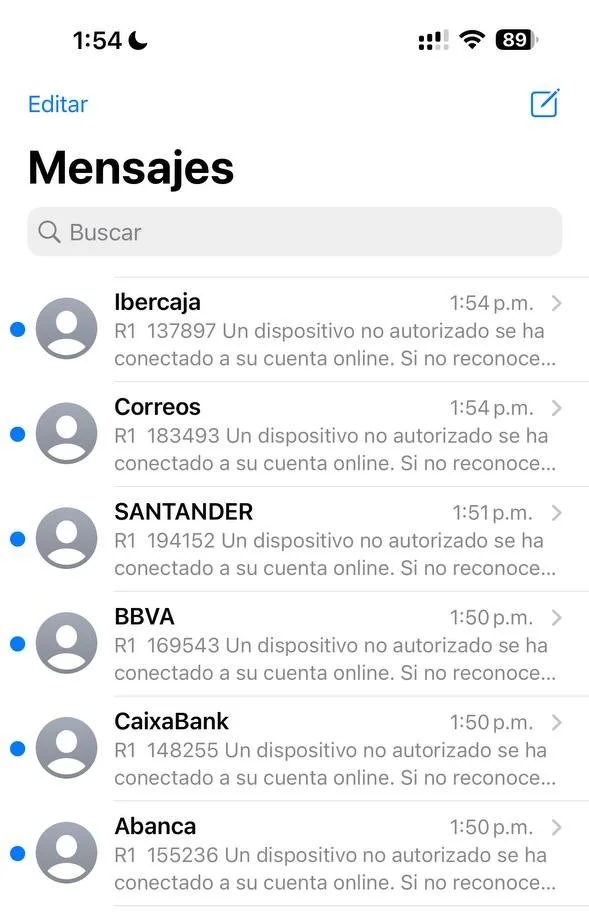
The campaign employs a multi-stage attack strategy, starting with targeted SMS phishing messages distributed across Spain and other countries.
The messages use faked Sender IDs (SIDs) to create an illusion of authenticity which mimics various well-known financial institutions in order to deceive victims.
The threat actors behind the campaign have established a wide-ranging infrastructure, including phishing panels and Android trojans.
If a victim clicks the links contained within the fake messages, they are directed to websites purporting to be that of the financial institution, but which are really phishing websites designed to harvest user credentials
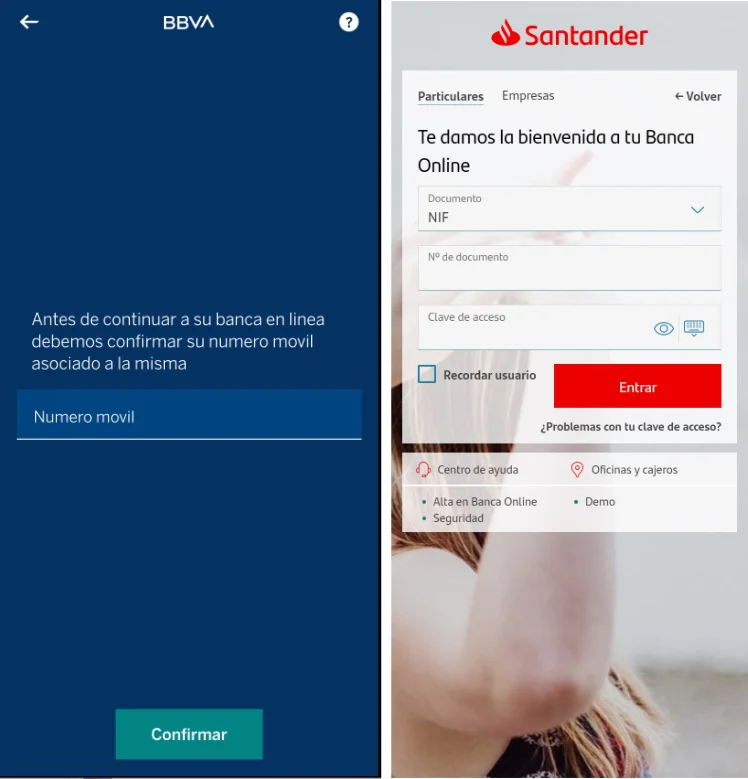
If a victim enters details into the fake websites, the data entered is immediately exfiltrated to a telegram channel owned by the threat actors which allows them instant access to the stolen data which will include the user credentials, IP addresses and HTTP user-agents.
The threat actors can then use this data to masquerade as the victim and access the victims banking accounts.
If a victims financial institution employs Multi-Factor Authentication (MFA), then the malware coaxes the victim to install a new security application (again fake) which requests permissions to send and receive SMS messages.
The real purpose of this app is to install a well-known Android malware called SMS Eye which allows the attackers to access any SMS authentication codes sent by the real bank when the attackers attempt to log-in to a victims accounts. As with the initial attack, any MFA messages are immediately exfiltrated to the Telegram channel.
Smishing-as-a-Service
As well as directly attacking victims, the gang receives revenue from a successful Smishing-as-a-Service platform the host offering targets in various countries worldwide.
Called Ankarex, the service currently has 1,700 subscribers which allows users the ability to launch and manage their own Smishing campaigns.