(26/06/23) Blog 177 – Google identify 10 vulnerabilities in Intel TDX
Researchers from the Project Zero & Cloud teams at Google have released a report detailing a security review of the Intel Trust Domain Extensions (TDX) feature.
The security review was performed in cooperation with Intel engineers on pre-release source code for version 1.0 of the TDX feature. This code is the basis for the TDX implementation which will be shipping in limited SKUs of the 4th Generation Intel Xeon Scalable CPUs.
The primary goal of the security review was to provide assurances that the Intel TDX feature is secure, has no obvious defects, and works as expected so that it can be confidently used by both cloud customers and providers.
The joint team inspected the firmware used with TDX looking for issues, including those related to arbitrary code execution, safe error handling and state management, and denial of service.
The review, which took place over a nine month period covered 81 potential attack vectors, and resulted in 10 confirmed security issues and five defense-in-depth changes.
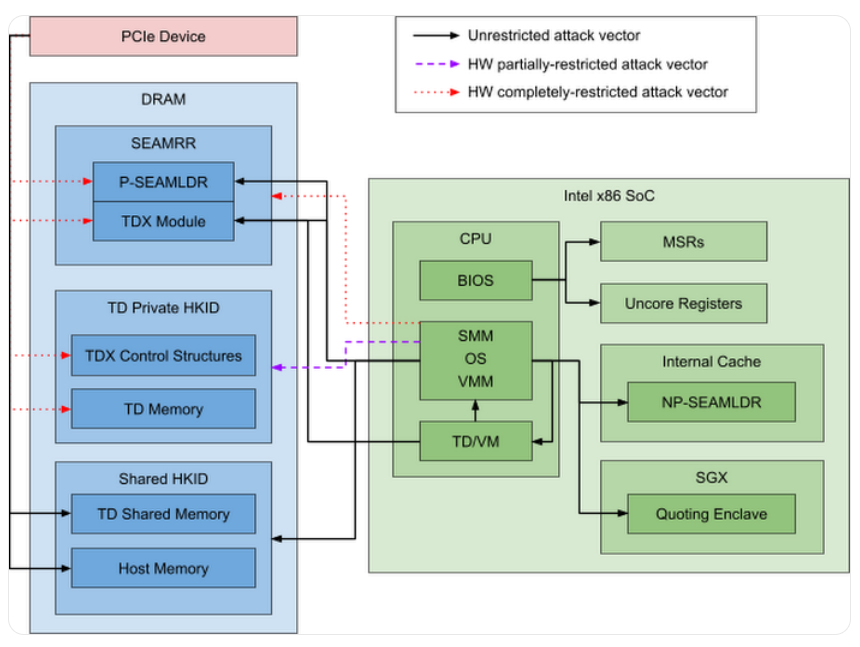
What is TDX?
Intel Trust Domain Extensions (TDX) provides hardware isolated virtual machines referred to as Trust Domains (TD), which isolates sensitive resources, such as virtualised physical memory from the hosting environment.
TDX provides assurances to cloud customers that cloud providers cannot access their virtual machine’s private information even with full control over the host control mechanisms such as the kernel services and hypervisor
Intel TDX is designed to isolate VMs from the virtual-machine manager (VMM)/hypervisor and any other non-TD software on the platform in order to protect them from a broad range of attacks. These hardware-isolated TDs include:
- Secure-Arbitration Mode (SEAM) – a new CPU mode of operation designed to host an Intel-provided, digitally-signed, security-services module called the Intel TDX module.
- Shared bit in Guest Physical Address (GPA) to help allow TD to access shared memory.
- Secure Extended Page Template (EPT) to help translate private GPA to provide address-translation integrity and to prevent TD-code fetches from shared memory. Encryption and integrity protection of private-memory access using a TD-private key is the goal.
- Physical-address-metadata table (PAMT) to help track page allocation, page initialization, and TLB consistency.
- Intel Total Memory Encryption-Multi Key (Intel TME-MK) engine designed to provide memory encryption using AES-128- XTS and integrity using 28-bit MAC and a TD-ownership bit.
- Remote attestation designed to provide evidence of TD executing on a genuine, Intel TDX system and its TCB version.
A technical white paper detailing Intel TDX can be viewed here.
Technical review paper
A summarised report is available via the Google Project Zero blog, but the full report into the findings can be obtained here.












