(04/06/23) Blog 155 – A brief(ish) history of malware
Malware is a force to be reckoned with when using any form of I.T. The rise of malware in recent years has been huge, as the payoff for criminals if they can infect an unsuspecting victim can be very lucrative.
In this post, I’ll take a look at some of the most significant stages in the history of one of the Internets most troublesome things.
Where it all started
In the early days of computer networking, the predecessor of the Internet was the ARPAnet (The Advanced Research Projects Agency Network). This was the first wide-area packet-switched network with distributed control and one of the first networks to implement the TCP/IP protocol suite.
The first computers were connected to the ARPAnet in 1969 and the network was declared operational in 1971.
Creeper
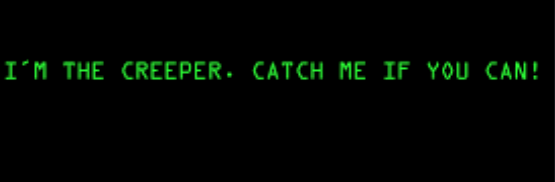
1971 also saw the worlds first malware – Named Creeper, this malware was an experimental program written by Bob Thomas at Bolt Beranek and Newman Inc. (BBN).
Its original iteration was designed to move between DEC PDP-10 mainframe computers using the ARPANET, with a later version by Ray Tomlinson designed to copy itself between computers rather than simply move.
This self-replicating version of Creeper is generally accepted to be the first computer worm and was a test created to demonstrate the possibility of a self-replicating computer program that could spread to other computers.
The program was not actively malicious software as it caused no damage to data, the only effect being a message it output to the teletype reading “I’M THE CREEPER : CATCH ME IF YOU CAN”
Rabbit
A few years later, in 1974, Rabbit (or Wabbit)appeared which followed the example of Creeper by reproducing itself across networked computers.
This time however, the malware did have a malicious nature as it copied itself repeatedly on an infected device until it filled the system with junk data and thus rendered it inoperable until the junk data was removed.
The speed of replication gave the virus its name – it bred as quick as rabbits do.
Animal
1975 saw the release of the first Trojan malware.
Developed by programmer John Walker, Animal was a game which was popular at the time where players tried to guess what animal the system was “thinking” of by asking it a maximum of 20 questions.
When users ran the program, a hidden program inside Animal (called Prevade) scanned the computer and copied Animal into every directory that did not have Animal already installed.
There was no malicious intent to Animal, but it is classed as the 1st Trojan malware in that it had another program hidden within its code.
Elk Cloner
Elk Cloner was a malware which was designed in 1982 to target Apple II computers. Designed and coded by 15 year old Richard J Skrenta Jr in 1982, this malware spread by infecting the Apple DOS 3.3 operating system using a technique now known as a boot sector virus.
Elk Cloner was attached to a game which was then set to play. The 50th time the game was started, the virus was released, but instead of playing the game, it would change to a blank screen that displayed a poem about the virus.
ELK CLONER: THE PROGRAM WITH A PERSONALITY IT WILL GET ON ALL YOUR DISKS IT WILL INFILTRATE YOUR CHIPS YES IT'S CLONER! IT WILL STICK TO YOU LIKE GLUE IT WILL MODIFY RAM TOO SEND IN THE CLONER!Elk Cloner poem
The Brain virus
In 1986, two Pakistani brothers – Amjad and Basit Farooq Alvi, created a boot sector virus that loaded a warning to individuals using pirated copies of their medical software.
The Brain virus worked by infecting the master boot record (MBR) of a victim’s machine while making a illegal copies of Alvi-owned software and then spread when the disk was inserted into the next machine.
Because there was no way to know that an infected MBR virus was coming along for the ride, it spread rapidly all across the globe.
Like many viruses at this time, the Brian virus wasn’t a destructive malware. It simply hid in the MBR so the machine wouldn’t boot but instead displayed a notification that included contact information of the Farooq Alvi brothers for remediation.
The Morris Worm
The Morris worm was the first malware to gain significant mainstream media attention and also resulted in the first felony conviction in the US under the 1986 Computer Fraud and Abuse Act.
Written by Cornell University student, Robert Tappan Morris, the worm was launched on November 2nd 1988, from the Massachusetts Institute of Technology (MIT)network and exploited weka passwords to move from one machine to another.
Morris did not intend for the worm to be destructive, instead seeking to merely highlight the weaknesses present in many networks of the time.
Unfortunately, Morris made an error when coding the worm – It was initially designed to check each infected computer to determine if the infection was already present but Morris believed that some system administrators might counter this by instructing the computer to report a false positive.
As a result, Morris programmed the worm to copy itself 14% of the time, regardless of the status of infection on the computer.
This resulted in a computer potentially being infected multiple times, with each additional infection slowing the machine down to a point of complete unuseability.

The AIDS ransomware
1989 saw the release of the AIDS malware by Joseph Popp. The story behind this malware is covered in my post yesterday, so needs no further comment here.
AOHell
In the mid 1990’s, Internet use was still a very expensive luxury, although companies such as CompuServe and AOL were starting to give away free minutes with their huge marketing campaigns.
Around the same time, Internet users started seeing the emergence of pirated software and games being touted on Bulletin Boards.
The pirated software (known as warez) was often spread around such Bullenin Boards with hidden malware. One such malware was AOHell which used a instant message bot to send messages via the AOL chat feature to unsuspecting victims informing them that there was a billing issue on their account and to avoid penalty fees being applied, they had to provide account details such as usernames and passwords.
These details were then harvested by the criminals behind the malware to be traded on other Bulletin Boards.
Michelangelo virus
Michelangelo was a boot sector virus released in 1991 that targeted DOS partitions and was spread via floppy disks.
The name was taken from the fact that the code was designed to lay dormant until March 6th, Michelangelo’s birthday.
When the malware was discovered, there was a lot of media coverage warning users to either leave their computers off on that day or change the date on their machines to a day ahead to avoid being impacted.
This was the first time a virus had received so much attention from the mainstream media, in both print and television, as seen in the BBC Newsround report below.
EarthLink Botnet
The first observed botnet was the EarthLink Spam botnet, which made its debut in 2000 and had one simple task – to send out massive quantities of spam.
During its reign, the EarthLink Botnet accounted for 25% of all email spam seen on the Internet (about 1.25 billion messages in total).
Named after the ISP who’s network was abused by the botnet, It’s operator – Khan C. Smith was sued by EarthLink for USD$24.8 million.
Smith, a Tennessee resident allegedly made USD$3 million from the botnet and used stolen credit card numbers and passwords of EarthLink users to create as many as 1,000 accounts used to send unsolicited e-mail.
Smith used dummy web sites and domain names to send spam promising free credit reports or free Internet service, but in order to get the free goods users would be asked to submit credit card details, passwords or other personal information to secure their new account.
Some of the sites offering free goods required the user to download software that contained trojan malware that allowed Smith to remotely access private information on the user’s computer.
Smith and others would then use that information to set up new spam accounts or resell those accounts to other criminals.
I Love You
The ILOVEYOU worm (A.K.A. Love Bug or Love Letter for you) that infected over ten million Microsoft Windows computers on and after 5th May 2000.
The malware spread as an email message with the subject line “ILOVEYOU” and the attachment “LOVE-LETTER-FOR-YOU.txt.vbs.”
At the time, Windows computers often hid the file extension (vbs) by default because it is an extension for a file type that Windows knows, This meant that the victim saw what looked like a harmless txt file.
Opening the attachment triggered the Visual Basic Script which overwrote random files then copied itself to all addresses in the Windows Address Book used by Microsoft Outlook and emailed itself to every contact found.
The creator of this worm was Onel de Guzman, a 24 year old resident of Manila in the Philippines.
At the time, there were no laws in the Philippines against making malware so the Philippine Congress enacted Republic Act No. 8792 to discourage future iterations of such activity. However, the Constitution of the Philippines bans ex post facto laws, and as such de Guzman could not be prosecuted.
Code Red
Code Red was a 2001 file-less worm in that it made no attempt to write to the storage of a victims device and existed only in memory.
The worm took advantage of a flaw in the Microsoft Internet Information Server – Microsoft’s in-built web server for Windows computers – and wreaked havoc by manipulating the protocols that allow computers to communicate and spread globally in just hours.
Once it found a vulnerable server, it displayed the following message:
HELLO! Welcome to http://www.worm.com! Hacked By Chinese!
The code then launched DDoS attacks against predetermined sites – one of which was the whitehouse.gov website.
Blaster
On August 11th, 2003, Blaster (A.K.A. MSBlast and lovesan) was launched which caused a Blue Screen of Death (BSOD) on victims machines and then rebooted them.
Blaster targeted a remote procedure call (RPC) vulnerability in Microsoft Windows XP and 2003 operating systems to propagate worldwide.
The worm’s goal was to perform a SYN flood attack against windowsupdate.com to prevent machines from accessing updates, however, the creator of the malware made the mistake of directing Blaster to the wrong domain.
The windowsupdate.com domain was not correct as machines instead used windowsupdate.microsoft.com to receive their updates.
Due to another error in the worm, it caused a buffer overflow on infected machines which resulted in the BSOD.
As a result of the wide adoption of Internet connectivity by 2003, Blaster unintentionally became the first global denial-of-service attack.
Mytob
Mytob was a malware first seen in 2005 and combined the functionality of a worm, a backdoor, and a botnet and infected victim machines in two different ways.
It either arrived via email through malicious attachments or exploited vulnerabilities in the Windows operating systems and used remote code execution.
Mytob utilised the victim’s email address book to propagate itself and also searched for other vulnerable machines via network scans to see if they could be compromised.
Mytob was one of the first viruses to specifically block or work against anti-virus software by preventing connectivity from the victims’ machine to AV update sites.
It achieved this by redirecting all known Anti-Virus vendor URLs to the local loopback IP address (127.0.0.1). This mean that all queries to public-facing websites resolved to the machine itself, essentially going nowhere.
CoolWebSearch
Initially seen in 2003, CoolWebSearch was the first malware operation to hijack search results from Google, overlaying search results with those from the threat actors themselves.
The purpose of the malware was to steal clicks from Google and earn the operators behind it revenue from every click made by victims.
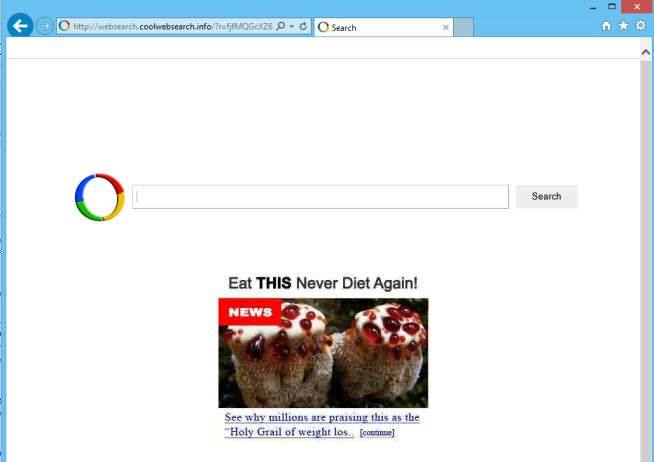
CoolWebSearch was most commonly distributed using drive-by downloads or adware programs. It was so pervasive and hard to remove that volunteers developed programs and managed web forums to help remove infections for free.
Stuxnet
Although not the first malware to affect Operational Technology (O.T.), the 2010 release of Stuxnet against the Iranian nuclear program is certainly the most high-profile example of such a malware.
Stuxnet targets programmable logic controllers (PLCs), specifically those used to control gas centrifuges for separating nuclear material at the Unanium enrichment facility in Natantz, Iran.
Exploiting four zero-day flaws, Stuxnet functioned by targeting machines using Microsoft Windows and then targeted the Siemens Step7 software which is used to program and control the PLCs used on the centrifuges.
Stuxnet had three modules: a worm that executed all routines related to the main payload of the attack; a link file that automatically executed the copies of the worm; and a rootkit responsible for hiding all malicious files and processes.

Reveton
In 2011, the world was introduced to Reveton. This was not the first ransomware – because, as mentioned earlier, that award goes to the AIDS malware back in 1989.
Reveton however is the first example of modern ransomware and established the look and feel of ransomware which still exists to this day
Features include the now ubiquitous lock screen that provides details of what happened, how to get in touch with the threat actors, how to pay the ransom, and how to decrypt files, etc. were first seen with Reveton.
Another first for Reveton was the use templates for the lock screens which would display an appropriate message based on geolocation and present the victim with instructions on how to make payment in their native language.
Flame
At the time of its discovery in 2012, Flame was considered the most advanced malware ever found.
The Budapest University of Technology and Economics stated in its report that Flame “is certainly the most sophisticated malware we encountered during our practice; arguably, it is the most complex malware ever found”
It had everything—a worm-like capability to spread via networks, the ability to record and capture screenshots and audio, the ability to eavesdrop on and record Skype conversations, and a capability to turn Bluetooth devices into listening beacons that could then exfiltrate and move files to a predetermined Command & Control (C2) server.
Linked to the Equation Group – believed to be a unit of the US National Security Agency (NSA) – Flame initially infected approximately 1,000 machines, with 65% of the infections seen in Iran, Israel, Palestine, Sudan, Syria, Lebanon, Saudi Arabia, and Egypt.
The malware supports a “kill” command which wipes all traces of the malware from the computer.
After its public exposure, the “kill” command was sent and all the initial infections of Flame stopped operating.
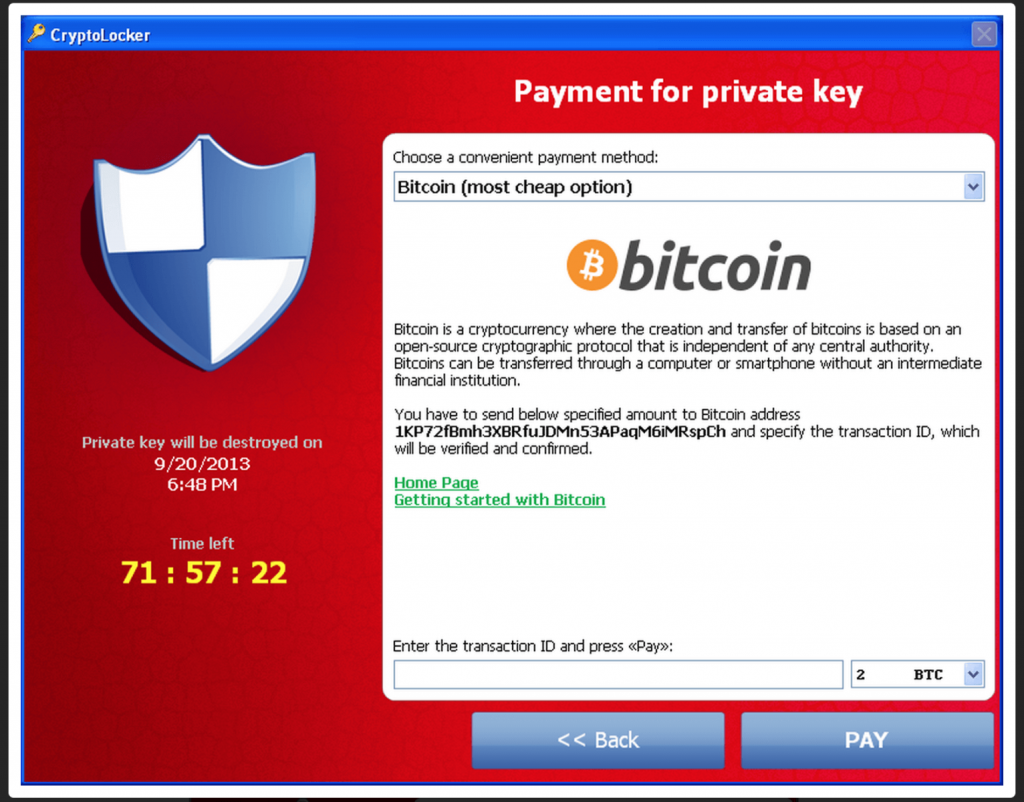
Cryptolocker
CryptoLocker was the first ransomware to demand payment via crypto-currency – Specifically Bitcoin.
Upon infection, victims were displayed a lock screen which (in 2013) said that the price for decryption was two BTC.
Heartbleed
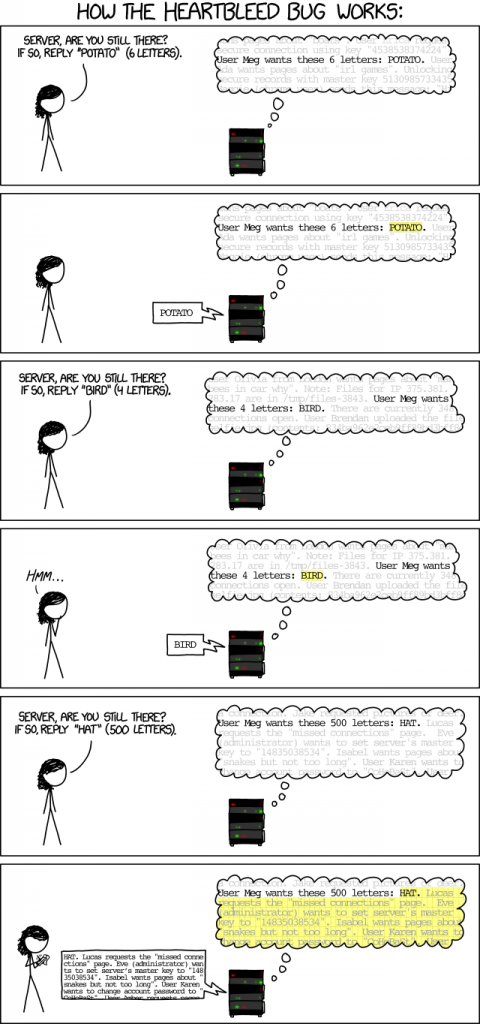
In 2014, Heartbleed burst onto the scene and caused major headaches for IT admins across the globe.
Heartbleed stems from a vulnerability in OpenSSL, which is an open source cryptographic library used by thousands of technologies worldwide.
OpenSSL periodically sends out a heartbeat message to ensure that secure endpoints are still connected. User systems send OpenSSL a specific amount of data and then ask for the same amount back as verification the connection is still established.
The vulnerability which was discovered allowed users to claim they’re sending the maximum amount of data allowed (64kb), but actually only send a single byte.
The vulnerable service will respond with the last 64kb of data stored in its RAM, which could include anything from user names to passwords to secure encryption keys.
Mirai
Mirai was the first botnet to target Internet of Things (IoT) devices. Although it primarily targeted network routers, Mirai also included various other IoT devices including fridges, webcams, smoke detectors and headsets.
Released in 2016, Mirai was mainly a DDoS botnet and has been responsible for some of the largest (by Gbps) attacks ever seen on the Internet.
Mirai was not only a high-profile attack because it was novel but also because it was able to amass a global botnet army in such a short amount of time, allowing it to redirect internet traffic to targeted sites from infected systems around the world. This made it especially hard to defend against, as the flood of traffic came from everywhere.
American college students Paras Jha, Dalton Norman, and Josiah White were the co-authors of Mirai. Jha and White ran a company called Protraf Solutions, offering mitigation services for DDoS attacks. Their story was a classic case of racketeering offering DDoS mitigation services to the very organisations their malware attacked.
Variants of Mirai are still being used around the world because the developers eventually released its code online for other criminals to use.
Petya / NotPetya & Wannacry
In 2017, The ShadowBrokers leak of the United States National Security Agency (NSA) was unprecedented and devastating—not just because it revealed secret malware being developed at the highest levels of the U.S. government, but also because threat actors effectively repurposed the tools and exploits that were released.
Part of the framework of tools included malware known as DoublePulsar, a backdoor attack that contained the infamous “EternalBlue” exploit.
EternalBlue was a zero-day exploit that the NSA kept in their arsenal that targeted Microsoft’s SMB (Server Message Block) protocol (CVE-2017-0444).
It was this exploit which was eventually used to spread the infamous Petya, NotPetya and WannaCry ransomware with disastrous consequences.
Note – I wrote about NotPetya in my 1st post back in January – you can read that here.
These ransomware variants were so disruptive that they caused the shutdown of tens of thousands of facilities worldwide.
Attribution for this leak was initially blamed on Russia, but to this day, nobody has been able to attribute the ShadowBrokers hack/leak to any specific entity.
Final thoughts
This post serves to highlight some of the stand-out malware which has plagued I.T. users for the last 50-or-so years.
By no means is it a comprehensive list and I’m sure I have missed some other notable examples, but it goes to show that no matter what, malware is here to stay.
All we can do is ensure our devices are as up-to-date with security patches, that we use a good, up-to-date anti-malware product, and that we remain vigilant with emails, downloads, and suspicious websites.
In the words of the long-gone UK T.V. show – Crimewatch – “Don’t have nightmares”!












