(31/05/23) Blog 151 – A cautionary tale of default credentials
We all know that we should change any and all default credentials on a system to something strong and safe right?
Well sometimes when people set up systems quickly to test something, or to have a play about, that might not always be the case as one Raspberry pi user found out to their dismay!
What is a raspberry pi?
If you aren’t familiar with the amazing world of the pi, then this next bit is for you – for others who are – skip to the next heading.
Raspberry Pi is the name given to a series of small, credit-card sized computers developed in the UK by the Raspberry Pi foundation.
The devices are classed as Single-Board Computers (SBCs) in the fact that they are complete device with all the standard features required of a functional computer such as microprocessor(s), memory, input/output (I/O), etc. all on one single circuit board.
Since their introduction in 2012, the Raspberry Pi has achieved huge success worldwide and has spawned multiple variants for all manner of implementations.
The devices have gained a massive following with computer and electronics hobbyists with thousands of projects available for people to experiment with.

When setting up a Raspberry Pi for use, many people opt for the official Raspberry Pi operating system – Raspberry Pi OS – previously called Raspbian.
The default credentials for this OS after installation is:
- username – pi
- password – raspberry
The problem
The malware targets Raspberry Pis’ being used with the default credentials of “Pi” & “raspberry” and immediately sets up a persistence mechanism which allows attackers to gain entry to the system even after reboot.
YouTube cyber security researcher John Hammond gives a brilliant walk through of this malware on his channel
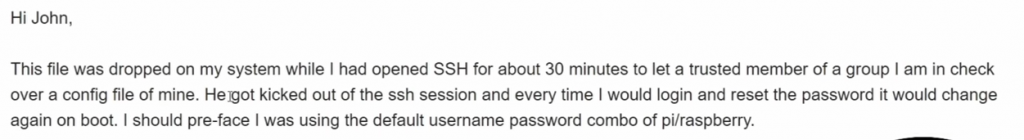
He received the malware sample from a subscriber who explained that they had set up a Raspberry Pi with default credentials and opened up an SSH channel for a colleague to access the device for a project they were working on.
Almost immediately, the device was compromised.
After initial compromise and persistence setup, the malware proceeds to build a communication channel which utilises IRC – Internet Relay Chat – to allow the attackers to bring the compromised Pi’s into their Botnet.
Towards the end of his tear-down of the malware, Hammond discovers that this is not actually a new malware and that there are online posts dating back to 2017 which show similar code being used to compromise Raspberry Pis
Check out the video here:
Final thoughts
Well, there is only one final thought really – Never use any system, no matter what with its default credentials – ALWAYS change them to something only you know which is safe and strong.












