(29/05/23) Blog 149 – .zip domains already being used for phishing
Earlier this month, I posted about the new .zip TLD which had been opened up for sale by google, and the issues it would inevitably bring. Well, it hasn’t taken long for criminal gangs to start using the domains as part of their ever increasing arsenal of devious tricks.
Browser-based archive tool
A new ‘File Archive in the Browser’ phishing kit abuses .zip domains by displaying fake WinRAR or Windows File Explorer windows in the browser to convince users to launch malicious files.
A blog post by security researcher mr.d0x explains how they created a phishing toolkit which allows users to create fake in-browser instances of the popular WinRAR utility and fake Windows explorer windows to trick users into thinking that they are actually opening .zip files.
Navigating to the domain mrd0x.zip opens a webpage, which, to the untrained eye looks just like an application not a webpage
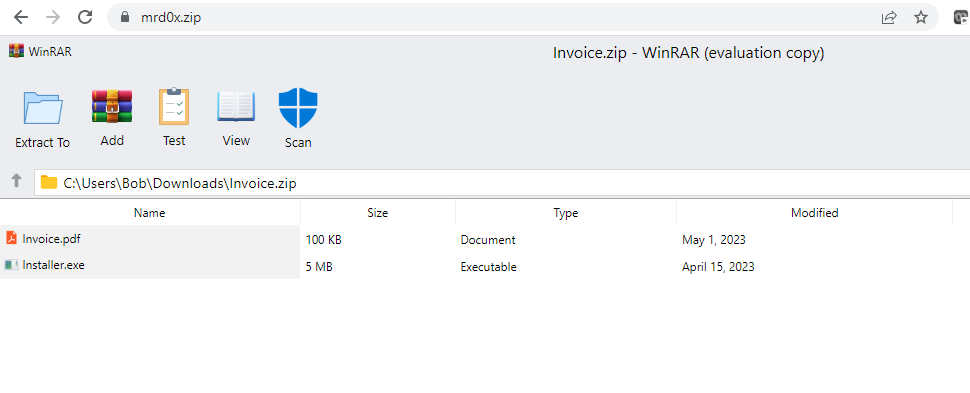
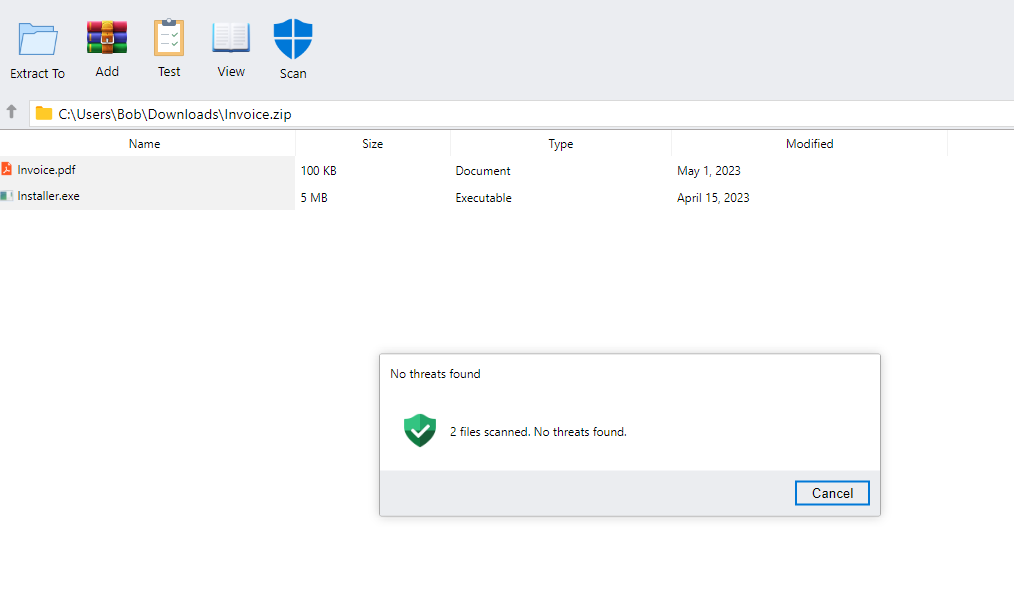
Far a bit of added realism, the website (app) has a scan utility which when clicked tells you that the files are completely fine and not malware at all – honest!
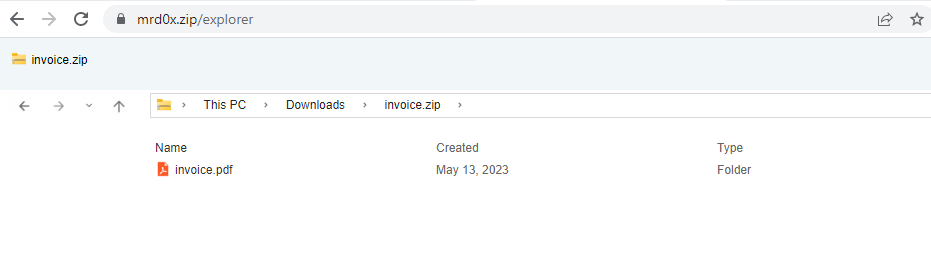
If your potential victim is suspicious of archive files – give them a link to Windows explorer instead.
Using the phishing toolkit
In his blog post, mr.d0x explains that the phishing toolkit can be used for both credential theft and malware delivery.
For example, if a user double-clicks on a PDF in the fake WinRar window, it could redirect the visitor to another page asking for their login credentials to properly view the file – thus harvesting an unwitting victims credentials.
If a user clicks on what they think is a PDF file it could be configured so that the toolkit instead downloads a similarly named .exe when clicked instead. For example, the fake archive window could show a document.pdf file, but when clicked, the browser downloads document.pdf.exe.
Because Windows does not show file extensions by default, the user will just see a PDF file in their downloads folder and potentially double-click on it, not realizing it is actually an executable, until its too late.












