(22/05/23) Blog 142 – Captia have a new cyber issue
It really is not a good time to be a Capita cyber security team member – hot on the heals of the ever-continuing saga of their March ransomware attack, the company has not been taken to task by Colchester city council who have started an investigation onto the discovery of an unsecured Amazon S3 data bucket which has exposed the benefits received by local residents in 2019-20 & 2020-21.
A statement on the council website informs people that the council is “taking swift and decisive action in response to the unsafe storage of personal data by its financial services contractor, Capita”
The statement also mentions that the breach has not affected just Colchester residents, but also that of several other local authorities around the country.
“The council is extremely disappointed that such a serious and widespread data breach has occurred and is robustly addressing the matter with Capita. I want to reassure all residents that we are taking steps with Capita to fully understand how they have caused this data breach as well as any further action required.“
Richard Block, Colchester City Council’s Chief Operating Officer,
Quick fix
Following the discovery of the exposed data, Capita has confirmed that it has since been made secure and confirms that the data does not include any bank details.
What is an S3 bucket?
An S3 bucket (Simple Storage Service) is the term given to an Amazon Web Services (AWS) data storage container.
An S3 instance can contain hundreds of data buckets, and each bucket can contain hundreds of data objects.
These data containers are similar to files and folders in a traditional hard-drive storage system.
Data elements have 3 main components:
- The objects contents – The data itself
- The objects metadata – descriptors about the object such as size, name, create date, modify date, etc.
- The objects unique identifier
These components allow the data to be very quickly indexed and organised so that the data can be searched and accessed by multiple systems and API’s (Application Programming Interfaces) easily.
S3 buckets enable large amounts of data to be stored and accessed through cloud systems.
Companies store data in S3 buckets for various reasons including big data analytics, disaster recovery, dynamic website content, and user-generated content.
S3 buckets are typically created in the cloud in a data region which is close to the main users – for AWS in the UK, this would most likely be in one of the two regions which serve the UK:
- EU-West 1 – Dublin
- EU-West-2 – London
Securing S3 buckets
Amazon offer a huge range of options for configuring and securing S3 buckets to allow customers as much freedom as possible over how their data is accessed.
The default configuration is that all buckets are locked down so that only the creator/owner has access.
How do buckets “leak”?
Having a bucket in this default configuration is only useful if the owner is the only entity that requires access. Typically though, with cloud systems, the data is designed to be accessed by others – as mentioned earlier.
Access can be granted by either security policies or ACLs (Access control lists) – very similar to how files and folders are accessed in a traditional IT environment.
Policies define which entities can access a bucket and its objects and what actions those entities can perform.
In the example below, entities are being granted the ability to list all objects in a bucket called test and then the ability to Put (write), Get (read), and Delete items in the bucket.
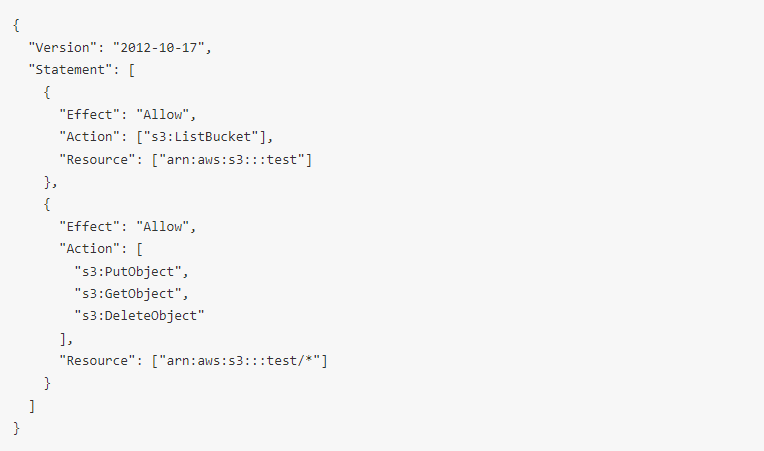
Its easy to see how complex this can become, and as such how easy it could be to make a mistake in the security configurations which then lead to non-authorised entities being able to access buckets and their data objects – A leaky bucket.












