(20/05/23) Blog 140 – The State of Ransomware
If you’ve been following my blog this year so far, you’ll have noticed that there has been a large number of posts where ransomware is the main topic. Unfortunately, this is because ransomware remains the number one threat to most companies at the moment.
Sophos, the UK-based security software and hardware company has just released its annual State of ransomware report for 2023 and the picture is fairly bleak.
Facts and figures
Target audience
For the report, Sophos sent questionnaires to thousands of companies they work with and compiled results from 3,000 respondents across 14 countries between January & March 2023. The companies selected ranged from those with 100 – 5,000 staff members with an annual revenue between <$10M – >$5B.
Results
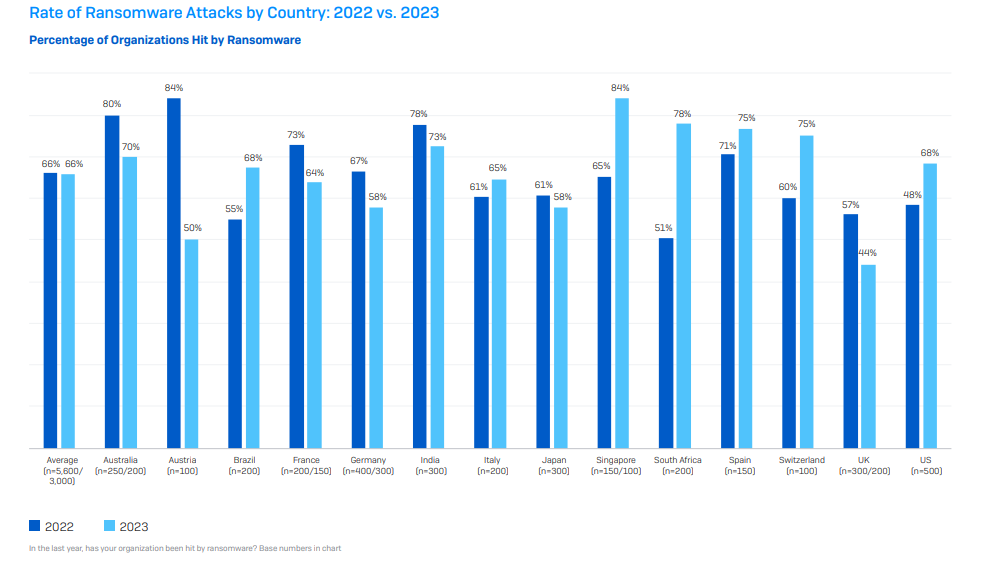
The first result in the report shows that the number of ransomware attacks has stayed at the same level since 2022 with 66% of respondents reporting that their organisation had been hit with an attack, but that the geographic regions targeted had changed.
Singapore reported the highest number of attacks at 84% of companies targeted, whereas the UK had the lowest rate of attacks at 44%.
Austria saw the sharpest decline in attacks since 2022 – a fall from 84% to 50% and South Africa saw the highest rise in attacks moving from 51% in 2022 to 78%in 2023
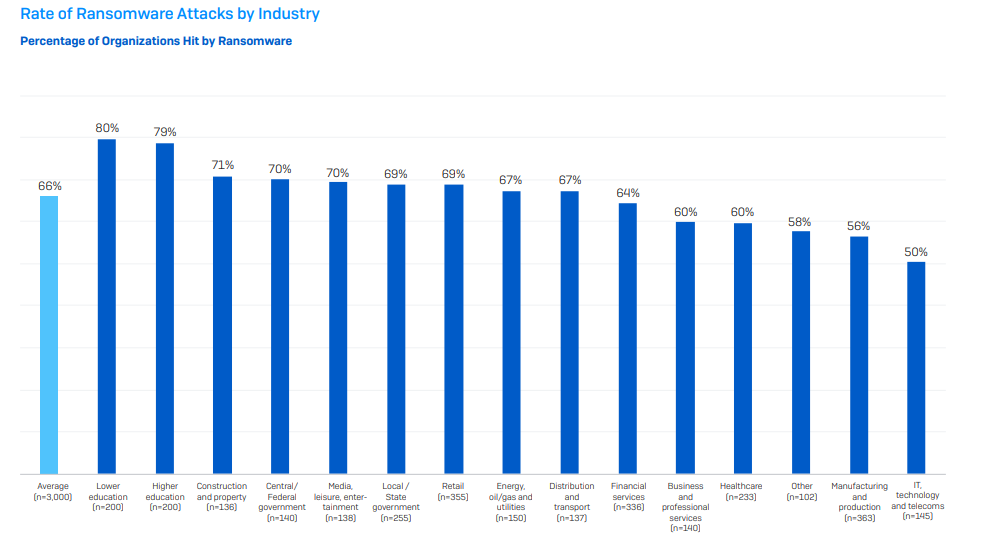
The Education sector has become the target of choice in 2022-2023 with both lower and higher education sectors reporting a sharp increase in attacks at 80% & 79% respectively.
Unsurprisingly, the IT sector seems to be the most resilient to attacks with 50% of respondents in that sector reporting an attack.
Ransom or extortion
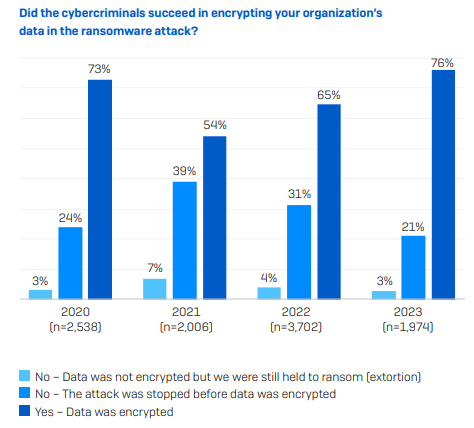
The number of successful attacks which resulted in data being encrypted as opposed to simply being stolen and held to ransom (extortion) has risen slightly compared to figures from 2020, but significantly since those figures for 2022. This is most likely down to threat actors finding novel ways round the controls put in place since 2020.
Paying ransoms
Most organisations are loathe to pay a ransom, and most do not, however, those which have reported paying to get their data back report that the cost of the ransom has almost doubled.
In 2022, the average payment was $812,380, whereas the figure for 2023 is $1,542,233.
The number of organisations paying over $1M has risen sharply with 40% of targeted companies paying in excess of the $1M figure compared to just 11% in 2022.
Attack vectors
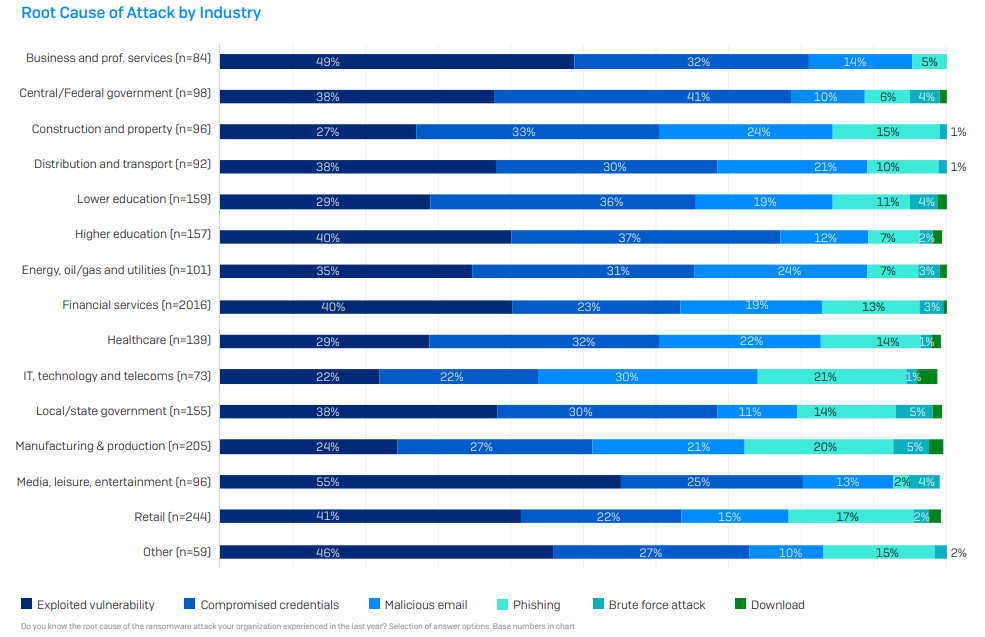
Across all sectors consulted in the survey, the figures for how the attack occurred shows that exploited vulnerabilities were the number one attack vector, followed by compromised credentials.
The media, leisure and entertainment industry has the worst record for vulnerable systems with 55% of respondents in that sector stating thats how they were compromised
It seems that government agencies are the worst for having weak credentials with 41% of organisations saying that was the root cause of their attacks.
IT, technology and telecoms companies were the sector industries who reported the highest number of cases (21%) tracing back to compromise via phishing.
Final thoughts
These figures are quite stark and highlight that the fight against ransomware is far from over. Vulnerable systems are still the number one way of attacking an organisation – industries from all sectors need to invest more in removing old, unsupported systems for those which are better designed to defend against ever-changing attacks.
Similarly, industries need to work more at educating users about the importance of good, strong credentials. Enforcing better policies for credential creation and use, but also to move away from the traditional username/password approach to that of Multi-Factor Authentication (MFA).












