(17/05/23) Blog 137 – RA GROUP steals 2.5Tb of data
A fairly new player in the ransomware game calling themselves the RA GROUP has listed four victims on its leak site with a total haul of over 2.5TB of stolen data.
The four companies breached include:
- EyeGene – A Korean R&D company specialising in the prevention and treatment of aging-related adult diseases (1.4TB data stolen)
- Bisco Industries – A distributor of Electronic Components and Fasteners used for production in Aerospace, Communication, Computer, Fabrication, Industrial Equipment, Instrumentation, Marine and Military Industries (580GB data stolen)
- Wealth Enhancement group – A US-based financial management company (65GB dfata stolen)
- Insurance providers group – An Illinois-based insurance provider (441GB data stolen)

Having first been seen on the 22nd April 2023, the group have managed to claim 4 scalps in just 24 days. Although it seems like they managed to compromise their victims on two separate days.
Standing on the shoulder of giants
Their ability to conduct their attacks so swiftly seems to be due to the fact that they are using the BABUK ransomware code which was leaked back in September 2021 on a Russian forum as opposed to developing their own code.
Babuk
Babuk call themselves cyberpunks who randomly test corporate network security and if successful, encrypt data and ask for money so as to not publish the data they gain access to.
So in other words – A ransomware gang!
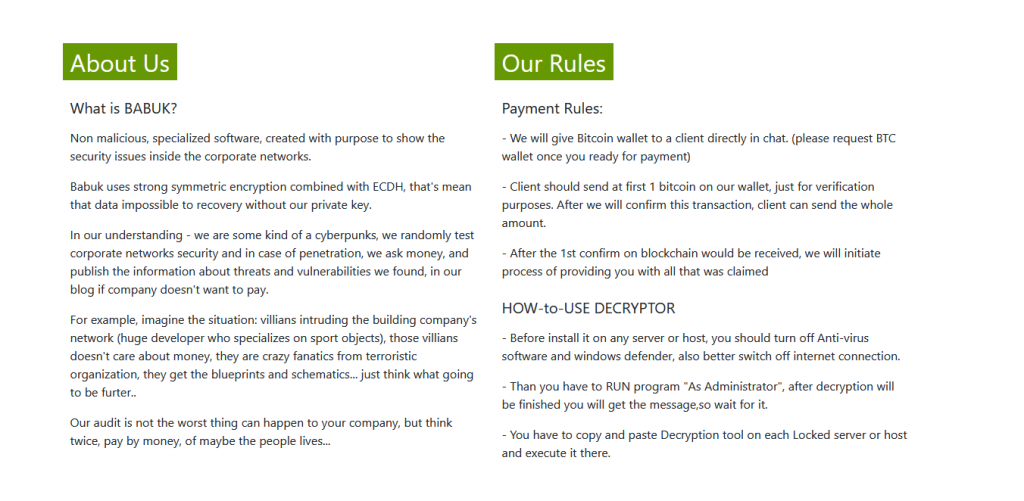
The BABUK gang have publicly expressed that they are against the Black Lives Matter movement and LGBT communities. They also have a major beef with Elon Musk and state on their leaks site that if they manage to penetrate any entities related to the Worlds Richest Man, they will publish it immediately with no ransom required.
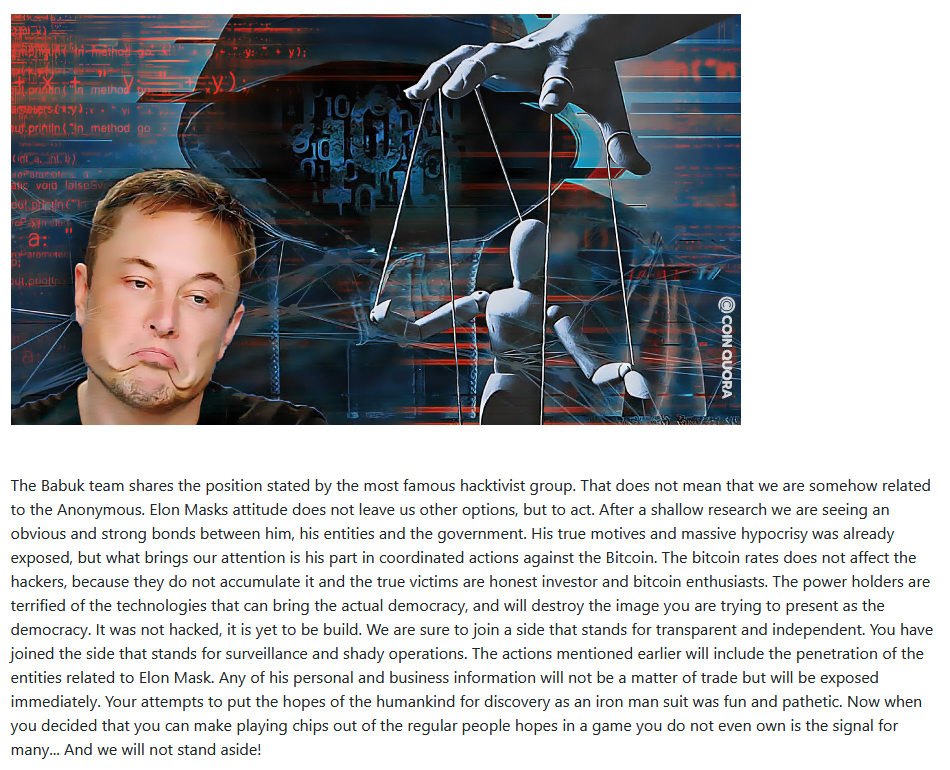
Betrayal, backstabbing, and internal struggles
The BABUK gang attacked the Washington DC Metropolitan Police Department back in April 2021 and managed to get access to 250GB of data

After the attack, the Admin allegedly wanted to leak the data for publicity, while the other gang members were against it.
This caused internal issues with the group and shortly after, the group splintered with the original Admin forming the Ramp cybercrime forum and the remaining members launching Babuk V2, where they continue to perform ransomware attacks.
Soon after the Ramp cybercrime forum went live, it suffered a series of DDoS attacks. The Admin blamed his former partners for these attacks.
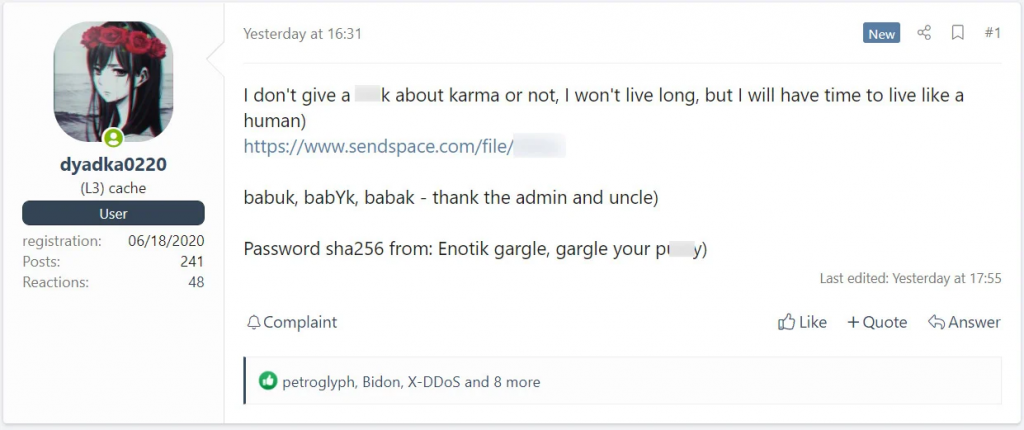
Shortly after this, the BABUK source code was leaked.
The code was leaked by someone with the username dyadka0220 who claimed to have terminal cancer and that they wanted to release the source code to the ransomware whilst they had time to live like a human.
FBI most wanted
One of the developers / admins behind BABUK – Mikhail Pavlovich Mateev has been added to the FBI’s list of most wanted fugitives.

Mateev, a Russian national has been linked to numerous ransomware variants including Lockbit, Babuk, and Hive.
Matveev has been identified as one of the alleged developers/administrators behind the Babuk ransomware variant and has been charged with multiple Lockbit, and Babuk attacks including the one against the Washington D.C. Metropolitan Police Department.
Mateev has also been added to the ever-growing US sanctions list:













