(23/04/23) Blog 113 – OSINT pt2
In the 2nd post of this mini-series on OSINT, I’ll take a look at how social media can be used as part of an OSINT investigation. The sub-topic of SOCMINT -Social Media Intelligence.
Oversharing
People simply cant stop over sharing on social media, whether directly, or via being tricked into responding to quizzes and challenges and whilst the majority of the data shared will be used by marketing and advertising companies, the data is also very useful to someone conducting an OSINT investigation.
Personal Social Media
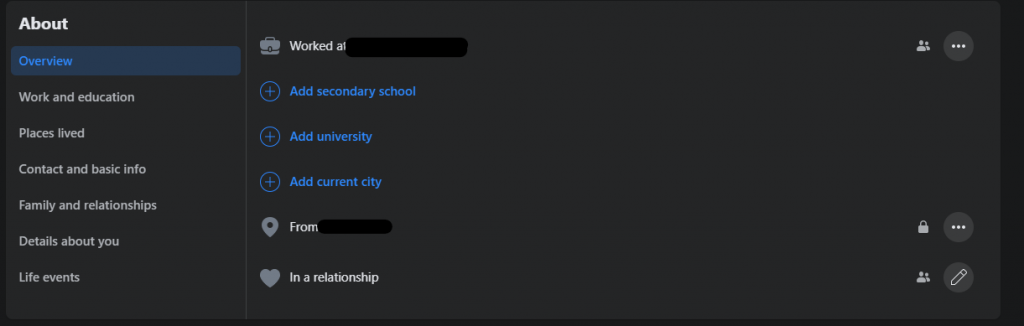
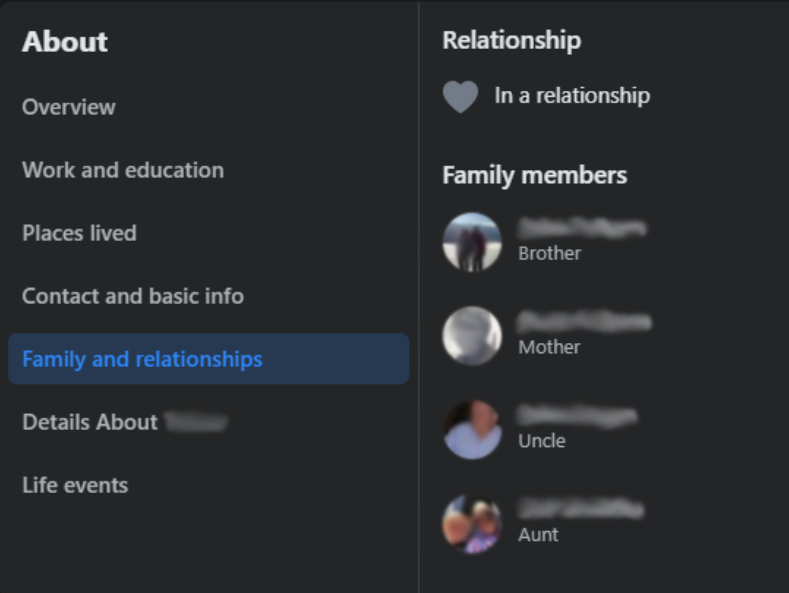
Personal social media sites like Facebook try to get you to post all sorts of personal data – birthdays, relationships, address, hobbies, education, employment, etc.
All this data is very handy to a would-be social engineer or fraudster as it gives them some really useful insights to a person.
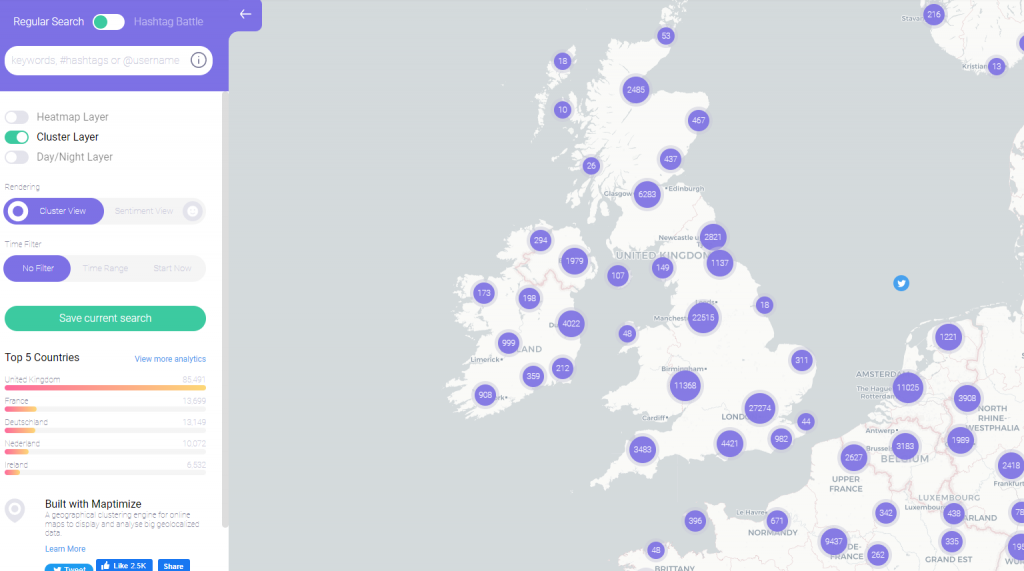
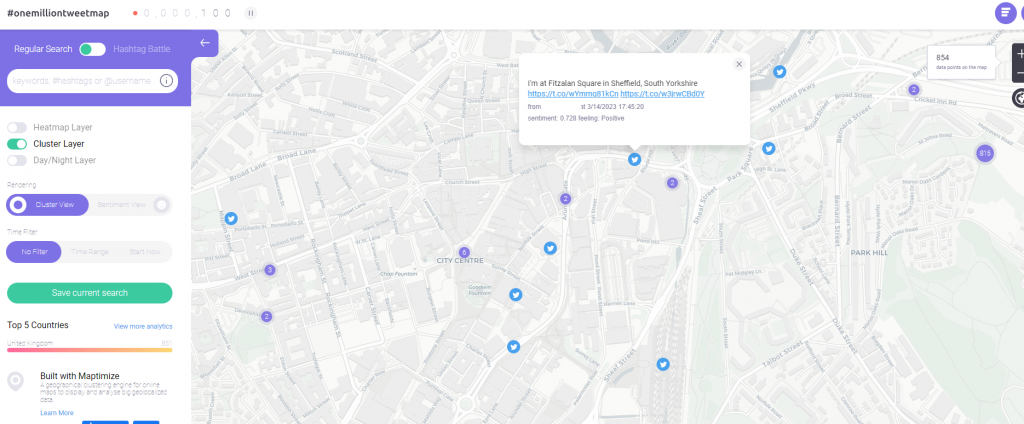
Twitter is another place where people often over share. If a user tweets or uploads a photo to twitter and they haven’t switched off the Geo-tagging function, then these photos can be used by others to get useful data about where the user might be.
Aggregating data like this can lead to the narrowing-down of potential places a user might live, or frequent.
Sites such as onemilliontweetmap.com can be quite useful at identifiying people in a specific area.
Professional social media
LinkedIn is another really good source of data for the fact that it not only shows personal information, but also business related data.
Most people who have a LinkedIn profile, don’t regularly update their profile information, but when they do it’s typically for a small number of reasons – either they are looking for a new job, have recently taken a new job or role, or had a promotion.
Regardless of the reason for the profile update, it becomes a very attractive source of information for someone running an OSINT operation.
Quite often, when a person adds or updates their employment information on LinkedIn, they give away useful tidbits of data relating to the companies they have worked for (Project titles, IT systems used, contracts worked on, etc.) – this can be really useful data for an attacker who might use the data in a social engineering campaign.
Forums
Another useful set of resources are those sites typically used by those searching for help and assistance. There are many different forums online to help those with a specific problem.
Think websites like GitHub, Reddit, Stack Exchange, and other such sites where IT technicians and developers might go to ask questions of their peers in regards to solving a tricky issue at work.
These sorts of posts might expose code which a developer is struggling to get to work, or a configuration issue on a router, or firewall or even just a throw-away comment about a specific software version they use.
Identifying users
Often, when a user builds a social media profile, they don’t use a real name, but instead use an alias.
However, most of the good online usernames have alreday been taken, so when a user gets a username they like, they quite often use the same name across multiple accounts – They use the same name on Twitter, Snapchat, Instagram, their Playstation account, their Xbox account, their Tripadviser account, etc.
If any one of these accounts is used to post any personal data, then you can use that to unravel all their other accounts.
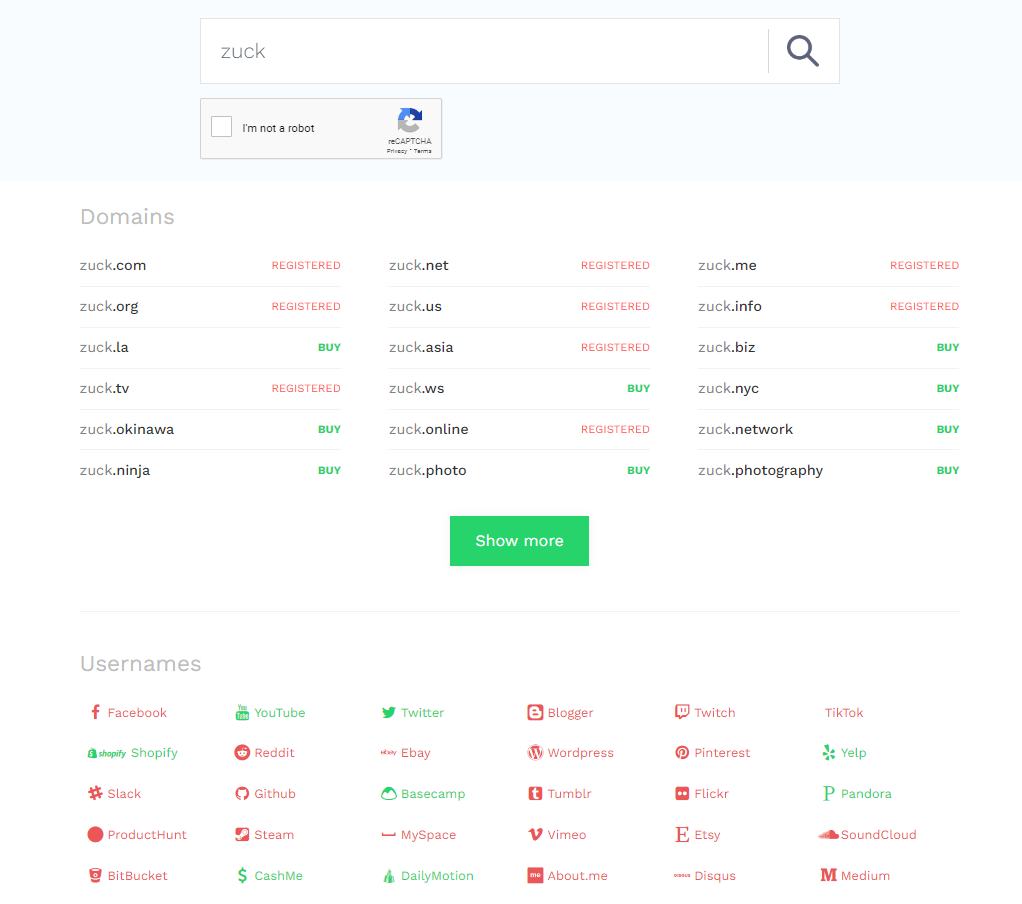
A useful website to use to see if a specific username has been taken on a social media site is Namechk.com. This website will check all the major social media sites to see if an account is registered under the name you supply. It also checks to see if any domains are registered with the same name.
If a site shows in red, it means that the name is already taken on that site – if it is green no account has been found which matches.
Social media ID’s
Whenever a social media account is created it has 2x “names” One is the vanity name which is the one used by the user to advertise their account. The other is the ID name (or number) used to identify the account in the database which drives the site.
If a user ever changes their vanity name, it will not change the ID value.
As such, if you can identify the ID of an account, then you can always identify the account even if the vanity name changes.
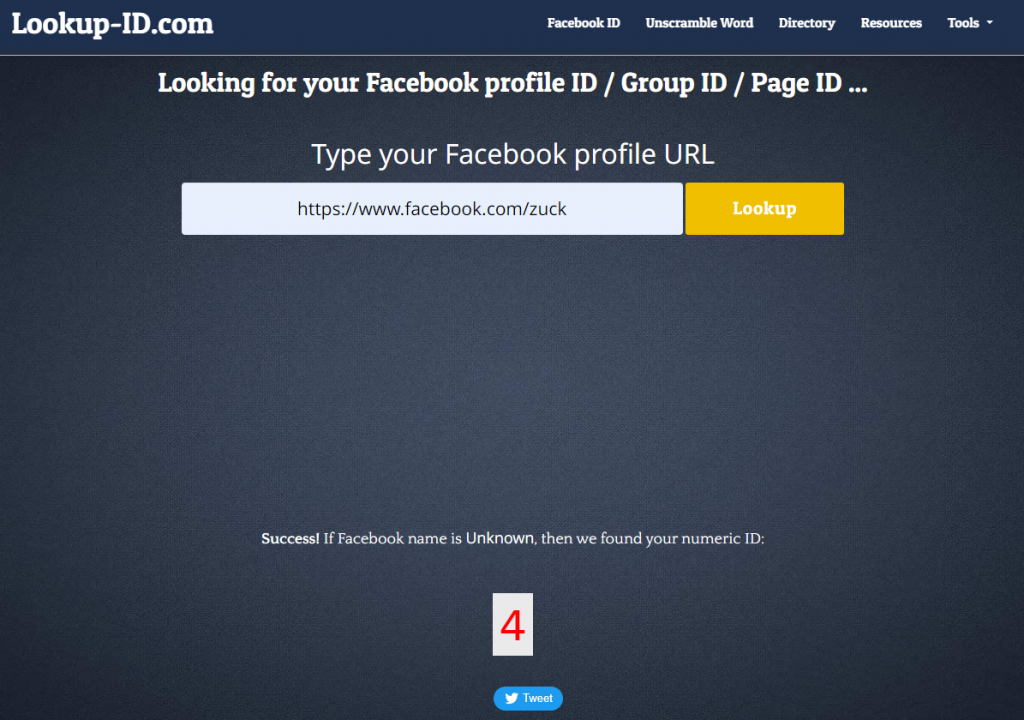
One site which can obtain the ID for a Facebook account is lookup-id.com
Other types of ID
If a person manages or owns a website which uses Google analytics or AdMob analytics then this can be used to check to see if they own or operate other websites.
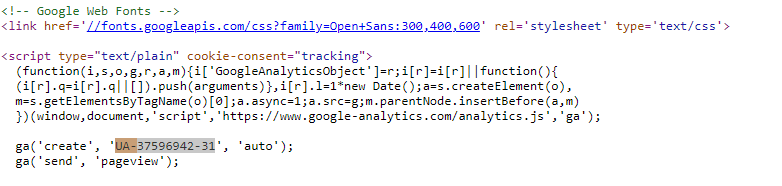
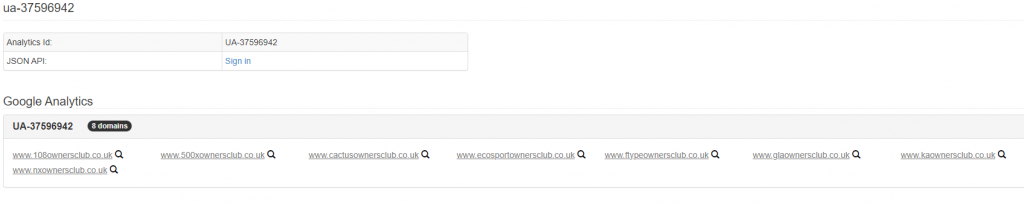
A Google Analytics ID has the structure “UA-XXXXXX” so by searching the HTML source code for “UA-” will identify any Google analytic IDs in a webpage. Simply copy the ID to the website spyonweb.com and then search to see if any other sites use the same Google ID.
There are many sources of data across various social media sites which can be very handy to a would be fraudster, so it pays to be cautious with the amount of data shared online.
In the next post, I’ll take a look at Metadata












